Netwrix helps you comply with India’s Digital Personal Data Protection (DPDP) Act
About the DPDP Act
India’s Digital Personal Data Protection (DPDP) Act, 2023 establishes a comprehensive legal framework for processing digital personal data. It defines obligations for Data Fiduciaries and Data Processors and grants rights to Data Principals, including consent management, access, correction, and grievance redressal. The Act emphasizes purpose limitation, data minimization, security safeguards, and timely breach notification to the Data Protection Board of India.
The DPDP Act applies to processing of digital personal data within India and to processing outside India if it is in connection with offering goods or services to Data Principals in India.
PDP Benefits
Top reasons why organizations comply with the DPDP Act:
- Builds trust and transparency
Shows a commitment to lawful, fair, and transparent processing that respects Data Principal rights. - Reduces legal and operational risk
Mitigates penalties, compliance orders, and reputational harm from breaches or noncompliance. - Aligns with global privacy standards
Supports harmonization with frameworks such as GDPR and APAC privacy laws for multinational operations. - Elevates data governance maturity
Promotes strong inventories of personal data, access controls, and measurable safeguards across hybrid environments.
How does Netwrix help you comply with DPDP?
Netwrix solutions help operationalize DPDP requirements by providing visibility into personal data, governing access and privileges, detecting threats, and producing audit evidence. Together they support consent-driven processing, purpose limitation, and robust security safeguards.
Our solutions support:
- Discovery and classification of personal and sensitive data for inventories and risk-based safeguards
- Access governance and least privilege across identities and data
- Privileged access control with full accountability and recording
- Continuous auditing, alerting, and searchable evidence
- Threat detection, breach investigation, and timely notification readiness
- Configuration integrity and change control for critical systems
Netwrix Data Classification
Automatically discovers and classifies personal and sensitive data across cloud and on premises repositories. Helps enforce purpose limitation, data minimization, and retention policies.
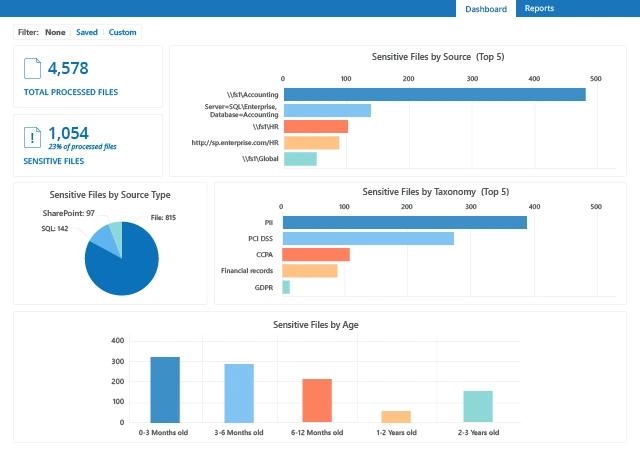
Netwrix Access Analyzer
Provides unified visibility into who has access to personal data and how it is used. Supports least privilege, periodic access reviews, and rapid remediation of overexposure.
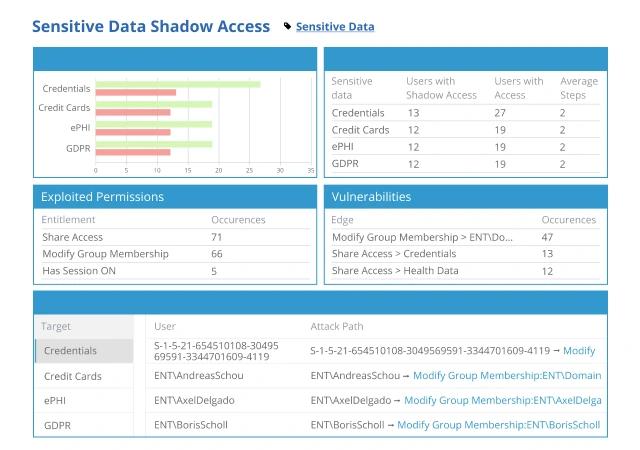
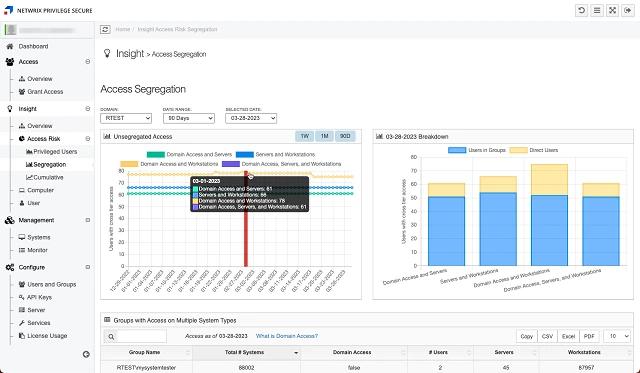
Netwrix Privilege Secure
Delivers just in time privileged access, credential vaulting, and session monitoring with recordings. Reduces insider risk and provides evidence of control over administrator activity.
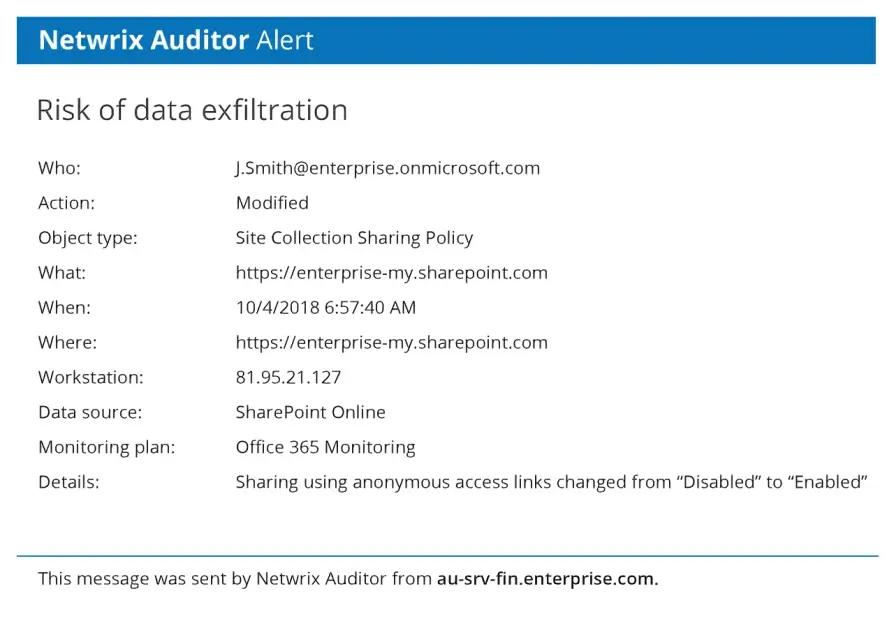
Netwrix Auditor
Creates centralized audit trails, predefined compliance reports, real time alerts, and Google like search. Simplifies evidence production for regulators and internal assurance.
Netwrix Threat Manager
Detects complex attacks, insider threats, and anomalous activity. Helps organizations rapidly identify, contain, and report personal data breaches.
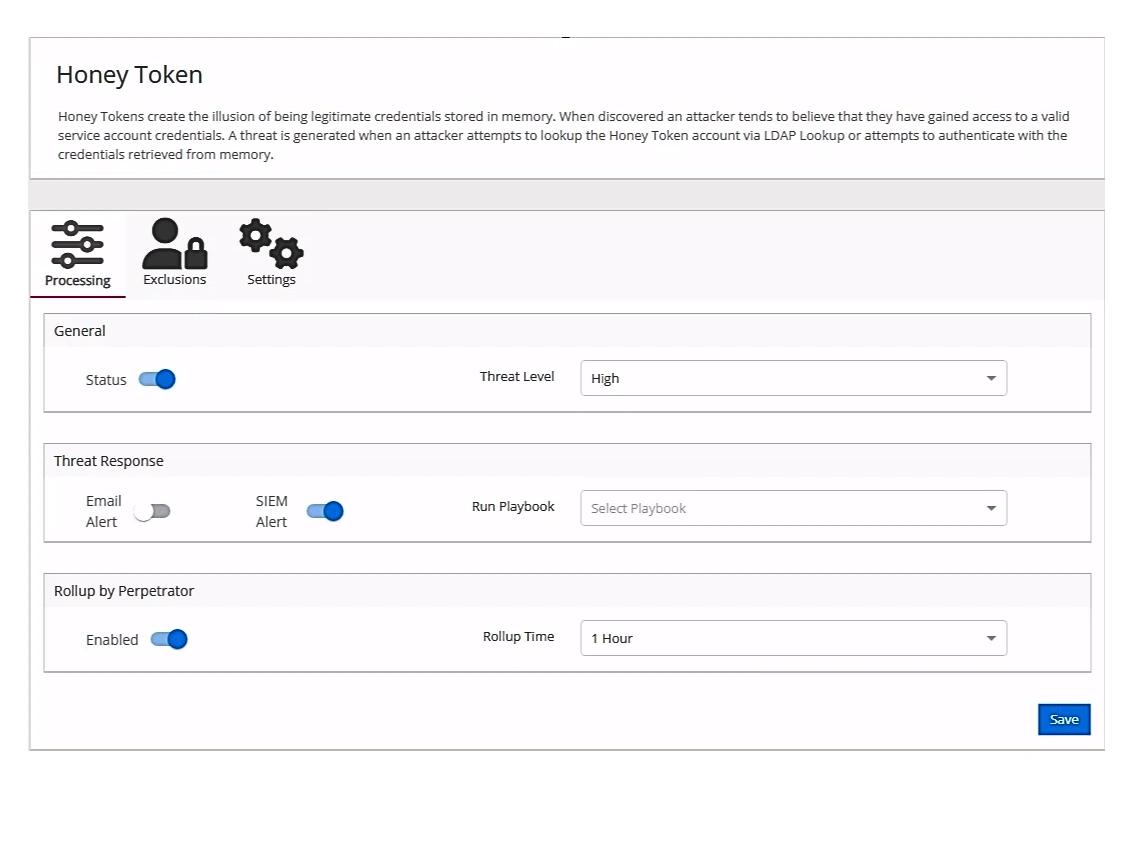
Netwrix ITDR
Identity threat detection and response for spotting compromised accounts and risky authentications. Strengthens identity assurance to prevent unauthorized access to personal data.
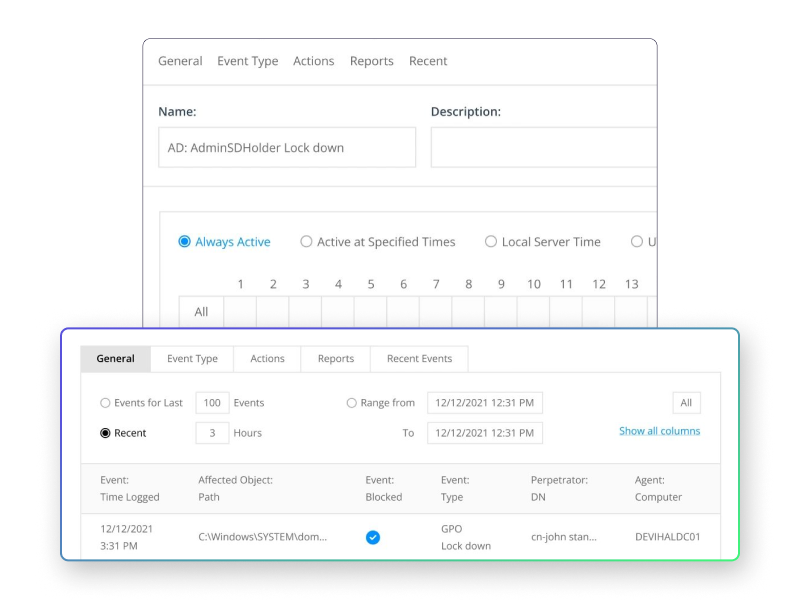
Netwrix Change Tracker
Monitors and enforces secure configurations and detects unauthorized changes on critical systems. Supports continuous assurance that safeguards remain effective.
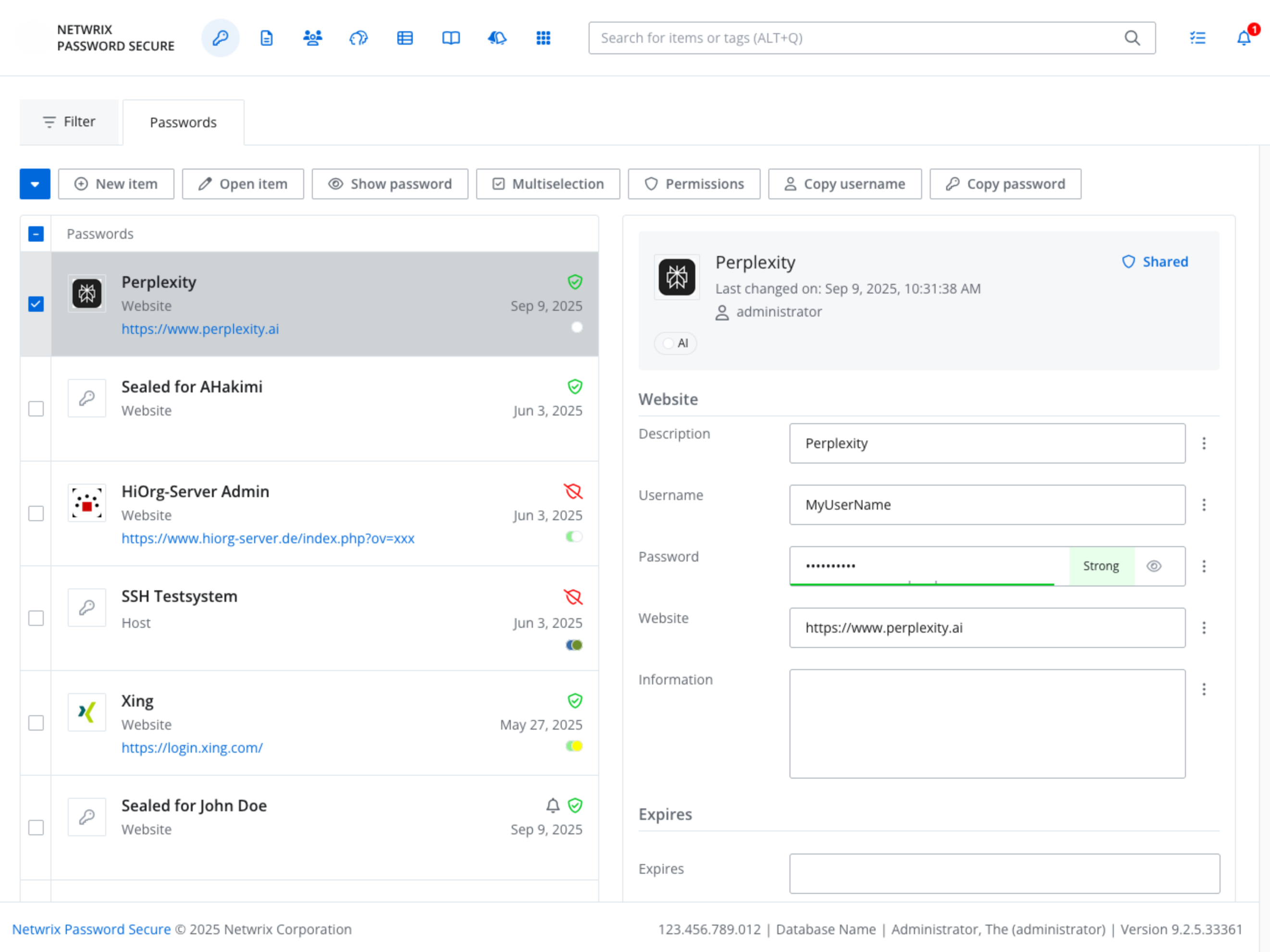
Netwrix Password Secure
Enforces strong, compliant password policies and secure credential management to reduce the likelihood of unauthorized access to personal data.
Netwrix PingCastle
Assesses Active Directory and Entra ID for misconfigurations and excessive privileges that could expose personal data. Feeds remediation plans to reduce identity risk.

FAQs
Share on
View related compliance concepts
Netwrix helps you comply with Korea’s National Network Security Framework (N2SF)
Netwrix helps you comply with APRA CPS 234
Netwrix helps you comply with the Philippines Data Privacy Act (DPA)
Netwrix helps you comply with Indonesia’s Personal Data Protection (PDP) Law
Netwrix helps you comply with PDPA
