AS-REP Roasting Attack - How It Works and Defense Strategies
AS-REP Roasting is a Kerberos-based credential harvesting technique that targets accounts configured without Kerberos pre-authentication. An attacker can request an AS-REP for such an account, receive data encrypted with the account’s long-term key, and crack that encrypted blob offline to recover the plaintext password. Because the attack uses standard Kerberos flows and offline cracking, it is stealthy and effective against weak or static passwords.
Attribute | Details |
|---|---|
|
Attack Type |
AS-REP Roasting (Kerberos credential extraction) |
|
Impact Level |
High |
|
Primary Attack Vector |
Accounts with “Do not require Kerberos pre-authentication” set; LDAP enumeration; network access to KDC |
|
Motivation |
Credential theft, lateral movement, privilege escalation, persistence |
|
Common Prevention Methods |
Enforce Kerberos pre-authentication, strong/long passwords, disable legacy accounts, monitor Kerberos activity, MFA, account hardening |
Risk Factor | Level |
|---|---|
|
Potential Damage |
High — compromised credentials may enable lateral movement and privilege escalation |
|
Ease of Execution |
Medium — requires enumeration of target accounts and offline cracking resources |
|
Likelihood |
Medium to High in environments with legacy/configuration gaps |
What is AS-REP Roasting?
Kerberos normally requires pre-authentication: the client must prove its identity to the Key Distribution Center (KDC) before the KDC issues a Ticket Granting Ticket (TGT). If an account is configured to skip pre-authentication (the “Do not require Kerberos pre-authentication” setting), an attacker can send an AS-REQ for that account and the KDC will return an AS-REP containing data encrypted with the account’s long-term key (derived from its password). The attacker extracts that encrypted blob and performs offline password cracking against it — if the password is weak, the attacker recovers it and can then authenticate as the account. This technique is known as AS-REP Roasting.
How Does AS-REP Roasting Work?
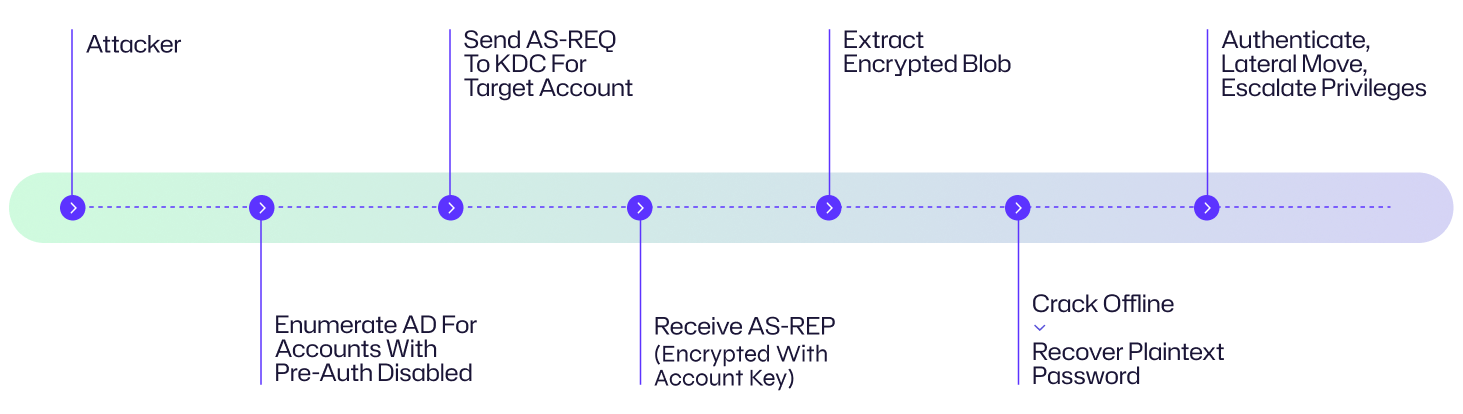
Below is a step-by-step breakdown of a typical AS-REP Roasting attack.
1. Reconnaissance — find accounts without pre-authentication
Attackers enumerate directory accounts to find users or service principals with Kerberos pre-authentication disabled ("Do not require Kerberos pre-authentication"). These are often legacy service accounts, computer accounts, or misconfigured user accounts. Enumeration is performed via LDAP/AD queries or reconnaissance tooling.
2. Request AS-REP for target accounts
For each discovered account, the attacker sends an AS-REQ to the domain KDC for that username. Because pre-authentication is disabled, the KDC returns an AS-REP containing data encrypted with the account’s password-derived key.
3. Extract the encrypted blob
The attacker extracts the encrypted portion of the AS-REP response (the encrypted timestamp or encrypted part of the ticket) and formats it for offline cracking.
4. Crack the key offline
Using offline password-cracking tools (GPU-accelerated or distributed cracking), the attacker attempts to recover the password via brute force, dictionaries, or targeted candidate lists. Weak or static passwords are vulnerable.
5. Use recovered credentials for lateral movement & persistence
Once the password is recovered, the attacker can authenticate as that account, move laterally, access services, or escalate privileges. Service and machine accounts often have broad access, increasing impact.
✱ Variant: Targeting machine/service principals and long-lived accounts
AS-REP Roasting frequently targets non-interactive accounts (service principals, computer accounts) that were configured without pre-authentication for compatibility. These accounts often have long, static passwords and broad access, making them high-value targets.
Attack Flow Diagram
Example: Organization Perspective
An attacker scans Contoso’s AD and finds several legacy backup service accounts marked "no pre-auth" for compatibility with an old appliance. The attacker requests AS-REPs for those accounts, extracts the encrypted responses, and cracks a weak password offline. Using the recovered credential, the attacker accesses backup shares and domain resources, then escalates further by exploiting misconfigured group memberships
Examples & Real-World Patterns
Case | Impact |
|---|---|
|
Legacy backup/service accounts |
Attackers harvest credentials from service accounts configured without pre-auth, enabling data access and lateral movement. |
|
Automated scanning in pentests |
Red teams frequently include AS-REP checks to identify legacy exposure and weak password risks. |
Consequences of AS-REP Roasting
AS-REP Roasting can produce broad impacts if the compromised account has privileged access or access to sensitive data.
Financial Consequences
Compromise of service accounts can lead to theft of IP, customer data, or financial records, potentially triggering fines, remediation costs, or ransom demands.
Operational Disruption
An attacker using service credentials can access backups, alter scheduled tasks, or disrupt critical services, leading to outages and recovery costs.
Reputational Damage
Public disclosure of a domain compromise — especially if customer data or availability is affected — damages trust and can hamper partnerships.
Legal and Regulatory Impact
Exposure of regulated data may trigger GDPR, HIPAA, PCI, or other compliance investigations and fines.
Impact Area | Description |
|---|---|
|
Financial |
Data theft, fraud, extortion, remediation costs |
|
Operational |
Service outages, backup tampering, recovery workload |
|
Reputational |
Customer/partner trust erosion |
|
Legal |
Regulatory penalties, breach notifications |
Common Targets: Who is at risk?
Accounts with pre-authentication disabled
Legacy service accounts, compatibility accounts for old appliances
Non-interactive service principals
Static passwords and long-lived credentials
Accounts with weak or unrotated passwords
High cracking risk
Large estates with poor account hygiene
Many legacy systems and misconfigurations
Risk Assessment
Risk Factor | Level |
|---|---|
|
Potential Damage |
High — credentials can enable domain pivoting and data exfiltration. |
|
Ease of Execution |
Medium — requires AD enumeration and offline cracking resources. |
|
Likelihood |
Medium to High — many enterprises retain legacy/compatibility accounts. |
How to Prevent AS-REP Roasting
Prevention is straightforward conceptually but requires consistent account hygiene and configuration controls.
Enforce Kerberos pre-authentication
Enable Kerberos pre-authentication for all accounts unless absolutely required for legacy functionality. Minimize and justify any accounts configured to skip pre-auth.
Harden account passwords & lifecycle
Use long, randomly generated passwords for service and machine accounts, rotate passwords regularly (gMSAs where possible), and avoid storing secrets in plaintext.
Replace legacy patterns
Migrate legacy applications to support modern authentication or use dedicated, isolated service accounts with constrained access and frequent rotation. Prefer Kerberos constrained delegation where applicable.
Apply least privilege & segmentation
Limit the privileges of service accounts and isolate legacy systems via network segmentation.
Use MFA & Conditional Access
Require MFA and conditional access for interactive admin workflows. Note that AS-REP targets non-interactive accounts, so MFA is part of defense-in-depth rather than a direct mitigation for all cases.
How Netwrix Helps Defend Against AS-REP Roasting
Netwrix Identity Threat Detection & Response (ITDR) strengthens your defenses by continuously monitoring Active Directory and Microsoft Entra ID for risky account configurations, including those vulnerable to AS-REP Roasting. With real-time alerts on suspicious Kerberos activity, LDAP reconnaissance, or abnormal authentication attempts, ITDR enables security teams to act before attackers can crack service account credentials. By combining proactive detection with automated response workflows, Netwrix helps organizations minimize lateral movement opportunities and close the identity gaps that adversaries exploit.
Detection, Mitigation and Response Strategies
Detection
- Monitor AD queries and LDAP enumeration for scans that list account flags or query for pre-auth disabled attributes.
- Log and alert on excessive AS-REQ/AS-REP exchanges for accounts that normally should not be requested from unusual sources.
- Inventory accounts with pre-auth disabled and flag unexpected changes; maintain baseline.
- Honeypots/honey accounts: create decoy no-preauth accounts and monitor for AS-REP requests.
- Watch for signs of credential use after cracking: unusual logins, resource access, or lateral auth patterns.
Response
- Immediately rotate or disable exposed accounts if you detect suspicious AS-REP activity.
- Enable pre-authentication, rotate passwords, and replace with managed identities where possible.
- Conduct credential hunts for signs of recovered credential use and perform scope/impact assessments.
- Block attacker infrastructure at network level if identified and feasible.
Mitigation
- Eliminate accounts that require no pre-auth where feasible, or isolate and harden them.
- Introduce automated detection (SIEM rules) for LDAP enumeration, AS-REQ spikes, and AS-REP hits against decoy accounts.
- Integrate secret scanning in CI/CD to prevent accidental credential leakage.
Industry-Specific Impact
Industry | Impact |
|---|---|
|
Healthcare |
Compromised backup/service accounts could expose EHR backups and PHI. |
|
Finance |
Access to transaction systems or reporting servers can lead to fraud or data theft. |
|
Government |
Exposure of service credentials risks sensitive system access and national security data. |
Attack Evolution & Future Trends
- GPU acceleration & cloud cracking make offline password recovery faster and cheaper.
- Automated reconnaissance integrates AD enumeration and AS-REP requests into multi-stage campaigns.
- Shift to managed identities reduces exposure where implemented, pushing attackers toward legacy/high-value targets.
- Use of AI to prioritize cracking — attackers may apply ML to pick best candidate passwords.
Key Statistics & Infographics (suggested telemetry)
- Percent of accounts with pre-authentication disabled in your environment.
- Average password age for service accounts.
- Time to crack common password classes on available cracking hardware (for risk modeling).
Final Thoughts
AS-REP Roasting is effective and low-noise, preying on configuration gaps and weak credential hygiene. Eliminating pre-auth disabled accounts, enforcing managed secrets, and monitoring Kerberos/AD enumeration are the most effective defenses.
FAQs
Share on
View related cybersecurity attacks
Abusing Entra ID Application Permissions – How It Works and Defense Strategies
AdminSDHolder Modification – How It Works and Defense Strategies
Kerberoasting Attack – How It Works and Defense Strategies
Hafnium Attack - How It Works and Defense Strategies
DCSync Attacks Explained: Threat to Active Directory Security
Golden SAML Attack
Understanding Golden Ticket Attacks
Group Managed Service Accounts Attack
DCShadow Attack – How It Works, Real-World Examples & Defense Strategies
ChatGPT Prompt Injection: Understanding Risks, Examples & Prevention
NTDS.dit Password Extraction Attack
Pass the Hash Attack
Pass-the-Ticket Attack Explained: Risks, Examples & Defense Strategies
Password Spraying Attack
Plaintext Password Extraction Attack
Zerologon Vulnerability Explained: Risks, Exploits and Mitigation
Active Directory Ransomware Attacks
Unlocking Active Directory with the Skeleton Key Attack
Lateral Movement: What Is It, How It Works And Preventions
Man-in-the-Middle (MITM) Attacks: What They Are & How to Prevent Them
Why Is PowerShell So Popular for Attackers?
4 Service Account Attacks and How to Protect Against Them
How to Prevent Malware Attacks from Impacting Your Business
What is Credential Stuffing?
Compromising SQL Server with PowerUpSQL
What Are Mousejacking Attacks, and How to Defend Against Them
Stealing Credentials with a Security Support Provider (SSP)
Rainbow Table Attacks: How They Work and How to Defend Against Them
A Comprehensive Look into Password Attacks and How to Stop Them
LDAP Reconnaissance
Bypassing MFA with the Pass-the-Cookie Attack
Silver Ticket Attack
