Improve Your IT Security Posture by Reducing Your IT Risks
Netwrix Auditor’s IT Risk Assessment reports help you identify weaknesses in your
IT security policy settings and practices so you can continually improve your
security posture. Quickly spot the risks that require your immediate attention
and drill down to actionable details that enable prompt mitigation.
Download Free
20-day Trial
20-day Trial
We care about security of your data.
Privacy Policy
Privacy Policy
Launch In-Browser Demo
No need to deploy the product
Identify and Close Security Gaps with Continuous Risk Assessment
IT risk assessment helps you identify vulnerabilities that put your information
assets and business continuity at risk. Netwrix Auditor makes it easy to understand
your current risk profile, prioritize your response, know what steps to take to
remediate each issue, fine-tune risk levels to your
particular environment and then review the new risk profile to assess the success
of your efforts. By repeating this process, you can continuously improve your
security posture, as well as provide proof to management or auditors of your
compliance with internal policies or external regulations.
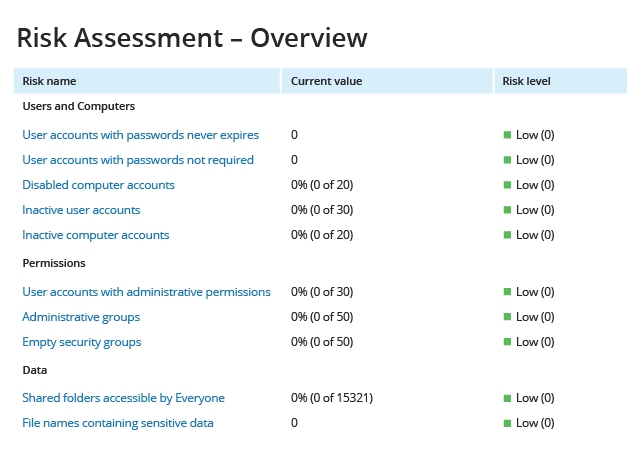
Gain a bird's-eye view
of your security posture
of your security posture
Understand your security posture in key areas at a glance. Automated
monitoring and scoring enables you to easily prioritize your risk mitigation efforts.
In addition to enabling cleanup prior to launching a security monitoring program,
this dashboard also enables continual assessment and improvement in each of three
key areas: permissions, data, and user and computer accounts. Start with the area
where the risk is highest and dive into the specific risk factors that require
your immediate attention.
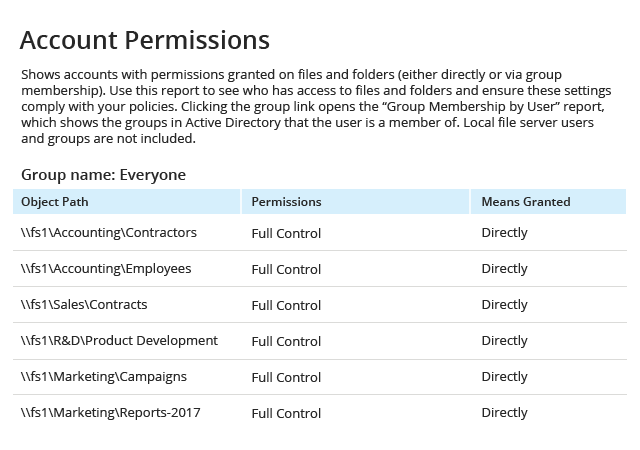
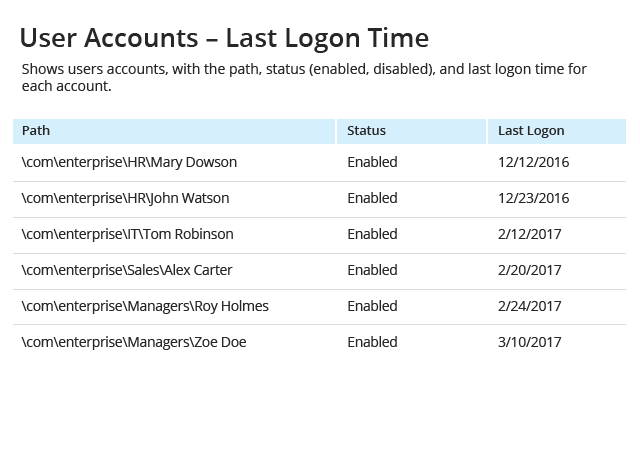
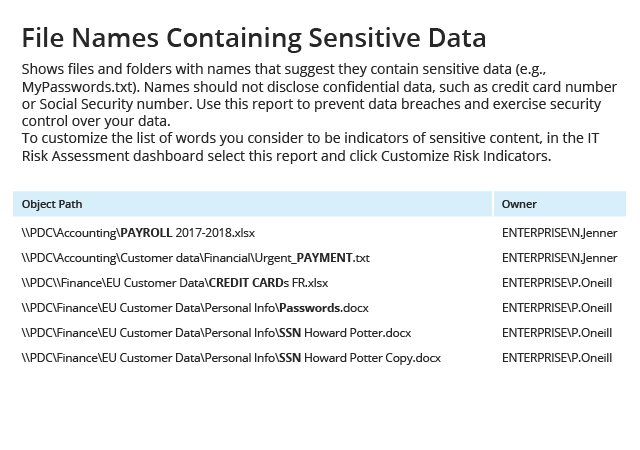
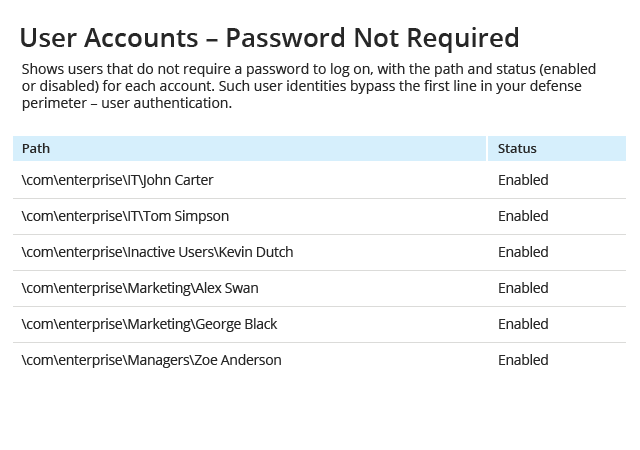
Get actionable data about how to reduce the identified risks
Drill down into detailed reports to determine which policy settings,
configurations, permissions or security practices you need to adjust to reduce each
risk to an acceptable level. For example, the reports will identify which shared
folders are accessible by “Everyone”, which user accounts are inactive but not
disabled, which files contain sensitive data in their names or which accounts
can access your network without authentication.
Tailor risk levels
to your IT environment
to your IT environment
No one knows your organization better than you do. If you find that
the current thresholds for the various risk factors do not reflect your
organization’s priorities and risk tolerance, adjust them to redefine when each
risk factor is considered low, moderate or high. This fine-tuning will help you
keep a close eye on the risks that are most important to your business and
remove other factors from your radar.

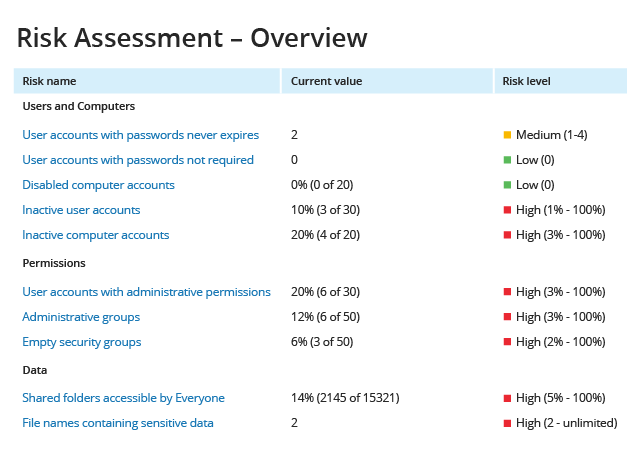
Continuously evaluate
your security posture
your security posture
After you have remediated your top risk factors for data, permissions,
and user and computer accounts, evaluate whether your security posture has improved,
and repeat the risk assessment and mitigation process continuously. Present the IT Risk
Assessment report to your management and auditors to prove that you have an effective
risk mitigation program in place.