Data access governance
Reduce data breach risk by knowing where sensitive data resides and who has access to it
Read their Stories
Trusted by




































































Organizations often lack continuous, identity-centric control over sensitive data access, increasing insider risks, compliance gaps, and enterprise-wide breach exposure.
Uncontrolled access to sensitive data
Without continuous visibility into who can access sensitive data across file shares, cloud platforms, and collaboration tools, organizations unknowingly expand their attack surface and increase data breach risks.
Static access reviews that fail in dynamic environments
Point-in-time access reviews fail to control evolving permissions and sensitive data, resulting in persistent overexposure of critical information.
AI and insider risk amplifying data exposure
Overly broad identity permissions combined with enterprise AI tools accelerate sensitive data misuse, reducing the time between excessive access and data loss.
Inability to prove who had access and why
When regulators or incident responders demand accountability, security teams cannot quickly prove who accessed sensitive data, increasing audit and legal risks.
Use cases
Continuous, identity-centric data access governance in practice
Identify and assess sensitive data risks
Discover and classify sensitive and regulated data, correlate it with identity-driven access, and prioritize remediation based on risk and business impact.
Reduce data overexposure
Continuously identify and remove stale, duplicate, and excessive permissions across on-premises and cloud environments to reduce sensitive data overexposure.
Enforce least privilege
Continuously align access to sensitive data with business need by removing inherited or outdated permissions and limiting the impact of compromised identities.
Automate risk-based access reviews
Prioritize access certifications using data sensitivity and access paths so high-risk exposures (including AI-accessible repositories) are reviewed and remediated first.
Detect abnormal access and data misuse
Monitor unusual access patterns, bulk reads and unauthorized permission changes to identify insider threats, compromised accounts and AI-accelerated exfiltration attempts.
Accelerate incident response and recovery
Rapidly identify exposed sensitive data and the identities involved, then automate remediation to minimize impact and reinforce continuous data governance.
The Netwrix approach
Continous data access governance for enterprise security
Protect sensitive data with least-privilege access
Once risks are understood, data access governance focuses on enforcing least privilege and keeping access aligned with business need as environments change. Netwrix enables data access governance controls that make least privilege practical to implement and sustain across complex, distributed environments.
Enforce least privilege access consistently
Ensure people have access only to the data required for their role. Remove excessive, inherited, or outdated permissions as roles change, reducing both the likelihood of misuse and the potential blast radius if an account is compromised.
Delegate access decisions to data owners
Identify accountable data owners and give them visibility into who can access the data they own. Enable regular access reviews and attestation so permissions remain aligned with business requirements while reducing dependency on security and IT teams for routine decisions.
Streamline access requests and approvals
Support controlled access requests that route decisions to the people closest to the data. This improves provisioning accuracy, shortens approval cycles, and reduces manual ticket handling without sacrificing governance.
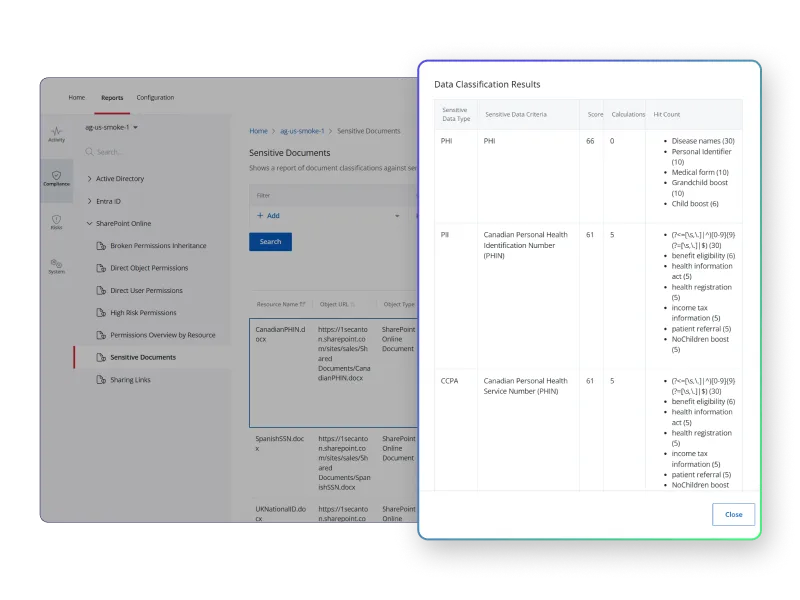
Maintain consistent data classification
Apply and maintain consistent data tagging across environments so downstream controls, such as monitoring, alerting, and remediation, rely on accurate context. Consistent classification ensures security decisions reflect data sensitivity rather than location alone.
