Discover and Classify Sensitive Data
Gain control of sensitive information with Netwrix
Read their Stories
Trusted by




































































Sensitive data is scattered and overexposed across environments, leaving organizations without the continuous visibility and classification required to reduce breach risk, enforce least privilege, prevent data loss, and prove compliance.
Uncontrolled data sprawl
Sensitive data multiplies across file shares, cloud, SaaS, and AI-connected platforms, expanding your attack surface faster than security teams can track it.
Stale or incomplete classification
Point-in-time scans miss newly created or modified sensitive content, leaving high-risk data untagged, overexposed, and invisible to enforcement controls.
Excessive and inherited access
Over-permissioned users and service accounts quietly expand the blast radius, turning a single compromised identity into a large-scale data exposure event.
Low-fidelity DLP controls
Inaccurate or missing classification fuels false positives and blind spots, allowing truly sensitive data to slip past prevention controls.
Audit and compliance gaps
Without defensible discovery and consistent labeling, organizations cannot prove who accessed sensitive data, how it was protected, or whether exposure has been reduced.
Use cases
Continuously discover, classify, and reduce data risk
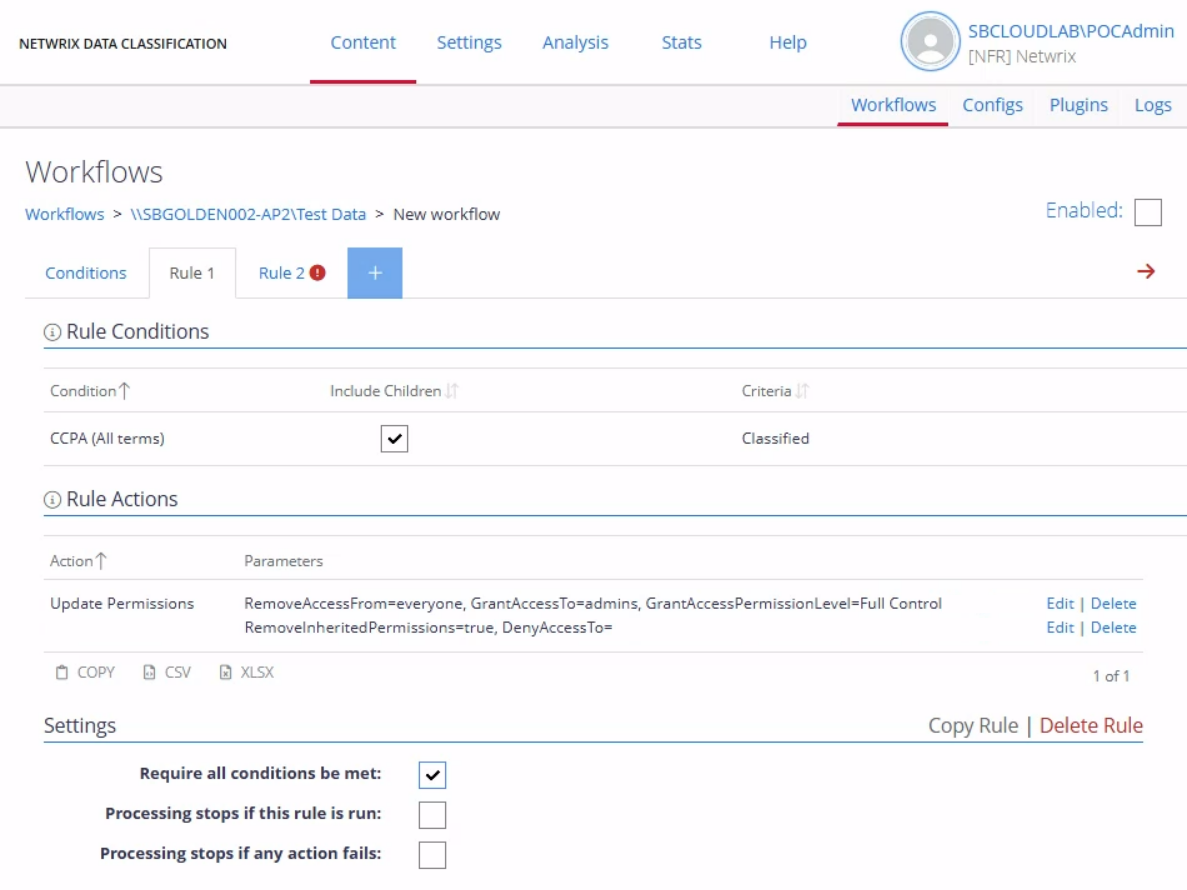
Discover and classify sensitive data
Continuously locate sensitive and regulated data across file shares, cloud platforms, SaaS applications, and AI-connected repositories. Apply high-fidelity, context-aware classification to accurately tag content and reduce exposure before it becomes a breach risk.
Run data risk assessments
Assess sensitive and business-critical data for overexposure, excessive permissions, and policy violations. Combine sensitivity, access context, and activity signals to prioritize remediation based on real data risk — not assumptions.
Remediate data exposure
Reduce risk quickly by removing excessive access, correcting inherited permissions, relocating sensitive data, or eliminating redundant, obsolete, or trivial (ROT) data. Automate remediation workflows to shrink your attack surface without disrupting business operations.
Get visibility into data access
See who has access to sensitive data, how that access was granted, and how it is being used. Correlate classification with permissions and identity context to enforce least privilege with precision.
Monitor activity and detect threats
Detect abnormal behavior, unauthorized access, and early indicators of compromise by combining data sensitivity with user activity. Identify AI-driven or insider risks before sensitive data is exfiltrated.
Simplify compliance and audit readiness
Maintain defensible discovery and consistent classification to prove control over regulated data. Streamline DSAR responses, support regulatory reporting, and provide clear audit evidence on demand.
The Netwrix solution
Continuously Discover, Classify, and Reduce Data Risk
Get in touch
Let’s talk security
Why Netwrix for data classification?
Sensitive data is often scattered across file shares, cloud platforms, databases, and applications, making it hard to protect and easy to overexpose. Without visibility and classification, you can’t enforce the right controls or prove compliance. Netwrix helps you automatically discover and classify sensitive data, so you know where it resides, who has access to it, and how it’s being used.

Locate sensitive data everywhere
Automatically identify sensitive and regulated information across on-premises and cloud environments, including files, databases, and collaboration platforms.
Classify data for better protection
Automatically tag sensitive data by type, such as PII, PHI, or financial records, to apply consistent controls with your DLP solution and prioritize risks.
Reduce compliance risk
Classification helps align with frameworks like GDPR, HIPAA, and PCI DSS by ensuring regulated data is identified and properly secured.
Enable least privilege access
Knowing where sensitive data resides allows you to restrict access and remediate unnecessary permissions.




