Endpoint Data Loss Prevention (DLP)
Stop sensitive data from leaving endpoints across apps, browsers, AI tools, copilots and removable devices on Windows, macOS and Linux with context-aware enforcement.
Read their Stories
Trusted by




































































Shadow AI, insider threats and mixed OS or offline endpoints create blind spots that leave sensitive data vulnerable to exfiltration.
Shadow AI Expands Data Exposure
Employees paste sensitive data into AI tools and copilots outside security oversight, creating uncontrolled exfiltration paths that traditional DLP policies were never designed to detect or stop.
Insider Risk at the Endpoint
Malicious or careless insiders can move sensitive data through apps, browsers, USB devices or printers, bypassing perimeter controls and increasing the risk of undetected data loss.
Mixed OS Creates Policy Gaps
Inconsistent controls across Windows, macOS and Linux endpoints create enforcement gaps, making it difficult to apply uniform data protection policies or maintain visibility into user activity.
Offline Endpoints Lack Oversight
Air-gapped and intermittently connected systems often operate without continuous monitoring, creating blind spots where sensitive data can be copied, moved or removed without detection.
Use cases
Control data movement across endpoints and AI
Block sensitive data in AI tools and copilots
Prevent classified data from being entered into generative AI tools and embedded copilots using context-aware policies based on data sensitivity, user identity and application behavior.
Stop unauthorized USB and device transfers
Enforce granular controls over USB drives and external media to prevent sensitive data copying across Windows, macOS and Linux endpoints without disrupting legitimate workflows.
Prevent data exfiltration via browsers and apps
Block sensitive data uploads to web apps, SaaS platforms and local applications with policy enforcement that adapts to user identity, file sensitivity and destination risk.
Enforce consistent protection across mixed OS
Apply unified, context-aware policies across Windows, macOS and Linux to eliminate enforcement gaps and ensure consistent data protection across heterogeneous endpoint environments.
Maintain protection on offline and air-gapped systems
Extend policy enforcement to air-gapped and intermittently connected endpoints, reducing blind spots where sensitive data could otherwise be copied, moved or removed without oversight.
Reduce insider risk with context-aware enforcement
Correlate data sensitivity, user identity and device context to detect risky behavior and automatically block unauthorized data movement before exposure escalates.
The Netwrix approach
Prevent sensitive data exfiltration at the endpoint
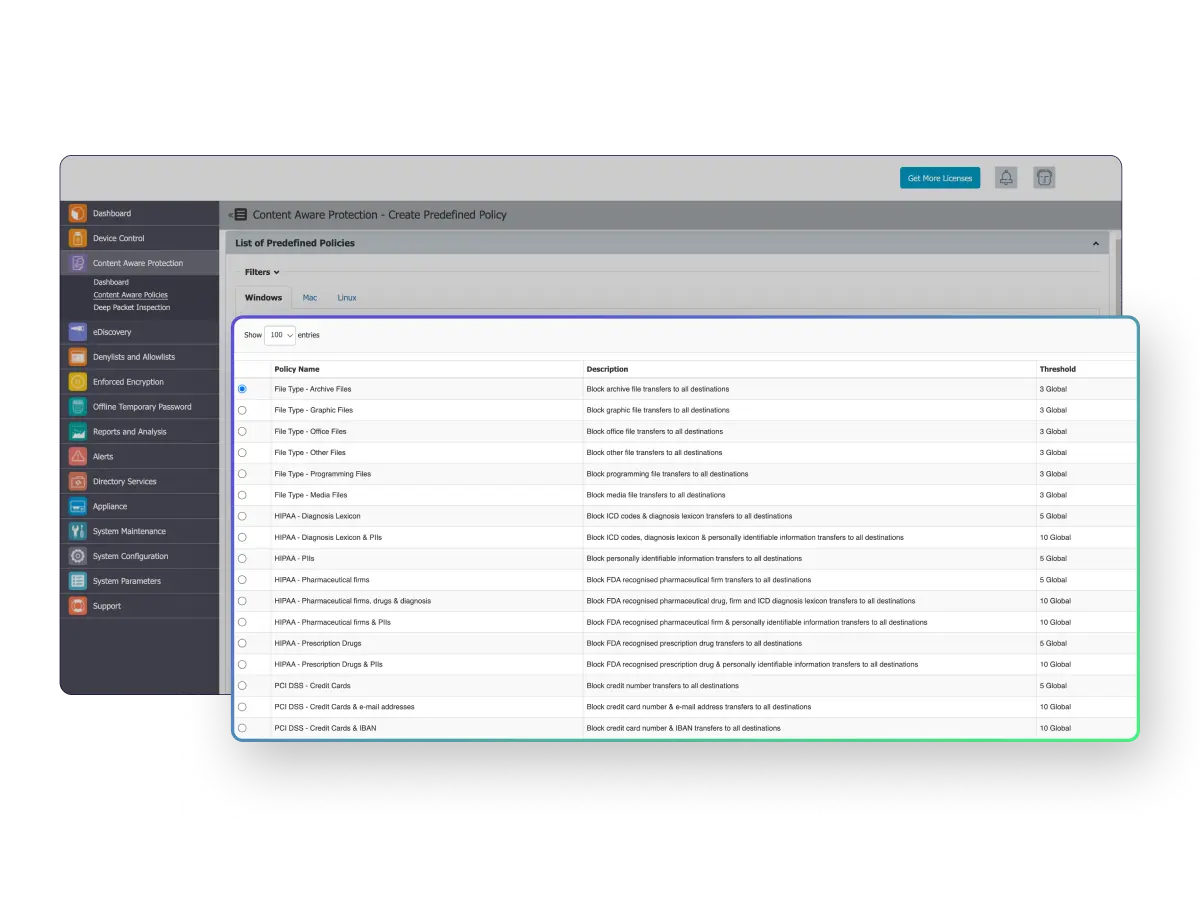
See for yourself
Ready to take the next step?
Data and Identity Powered Endpoint DLP Enforcement
Netwrix delivers endpoint DLP that unifies content-aware protection for data in motion, device control, enforced encryption with MDM for USBs, and eDiscovery for data at rest within a single policy-driven framework across Windows, macOS and Linux. Policies driven by data sensitivity, user identity and device context prevent exfiltration across apps, AI tools and peripherals, even on offline or air-gapped endpoints.

Consistent enforcement across Windows, macOS and Linux
Apply unified DLP policies across Windows, macOS and Linux endpoints to eliminate control gaps and ensure consistent protection regardless of operating system or device configuration.
Control data across more than 40 device types
Block or restrict sensitive data transfers across USB drives, Bluetooth, printers and over 40 peripheral device categories to reduce insider-driven exfiltration risks.
Enforce policies using identity and data context
Use data sensitivity, user identity and device context to apply precise controls that reduce false positives and prevent unauthorized data movement at the endpoint.
Protect data even on offline and air-gapped systems
Maintain policy enforcement and visibility on intermittently connected or air-gapped endpoints to prevent exfiltration and reduce blind spots beyond the corporate network.
Trusted by professionals
Don’t just take our word for it
Data Loss Prevention FAQa
Have questions? We’ve got answers.
See DLP in action

