Como auditar quem acessou dados no MS Teams e SharePoint Online
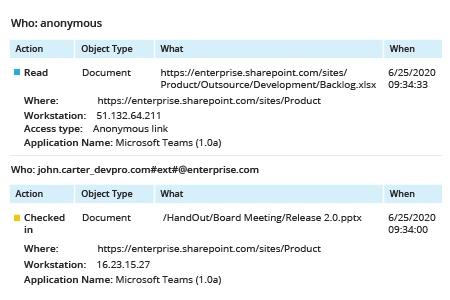
Netwrix Auditor para SharePoint
- Execute o Netwrix Auditor → Navegue até “Relatórios”.
- Expanda a seção “SharePoint Online” → Vá para “Atividade do SharePoint Online” → Selecione “Toda a Atividade do SharePoint Online por Usuário”.
- Clique em “View Report”.
Saiba mais sobre Netwrix Auditor for SharePoint
Auditoria Nativa
- Abra o painel de Security & Compliance do Office 365.
- Vá para Pesquisar -> Clique em “Pesquisa de log de auditoria”.
- Nos filtros de Atividades, escolha “Atividades de arquivo e pasta”, e então clique em “Pesquisar”
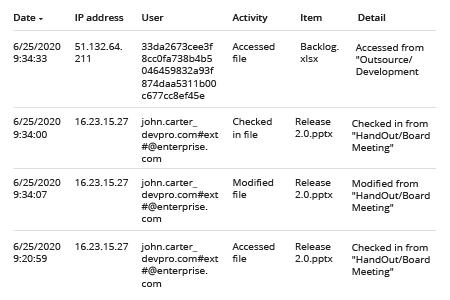
4. Para revisar o caminho até o documento afetado, clique no evento e navegue pelas seções de Detalhes para ver o “Object Id”:

5. Para agrupar os eventos pelo usuário que estava acessando os dados, você precisará baixar os dados em um arquivo .csv e ordenar os dados lá.
Uma maneira melhor de monitorar o acesso a dados no MS Teams e SharePoint Online
Usuários de negócios armazenam documentos, planilhas, apresentações e muitos outros tipos de arquivos em seus sites SharePoint e MS Teams — e podem compartilhar qualquer um desses conteúdos com outras pessoas dentro ou fora da organização em apenas alguns cliques. Portanto, monitorar o acesso de perto é essencial para a segurança dos dados. Além disso, a maioria das regulamentações de conformidade exige auditoria de acesso a dados para provar que você tem controle sobre dados sensíveis.
Embora o Log de Auditoria Unificado nativo do Office 365 permita que você revise eventos de acesso, suas opções de filtragem são tão limitadas que os profissionais de TI frequentemente têm que gastar uma quantidade significativa de seu valioso tempo refinando e analisando eventos de acesso, aumentando o risco de que atividades perigosas ou maliciosas passem despercebidas.
Netwrix Auditor permite que organizações atendam a rigorosos requisitos de conformidade e reduzam o risco de exposição de dados ao fornecer monitoramento abrangente e automatizado do acesso a dados no SharePoint e MS Teams. Utilizando sua função de busca flexível, você pode facilmente ajustar seus critérios de busca para rapidamente filtrar eventos. Além disso, você pode inscrever qualquer pessoa nos relatórios exatos de que precisam, reduzindo sua carga de trabalho enquanto mantém todos devidamente informados. Você também pode configurar alertas baseados em limiares e eventos para ficar por dentro de qualquer atividade suspeita.
Compartilhar em
