Centre de ressourcesGuide pratique
Comment détecter qui a désactivé un compte utilisateur dans Active Directory
Comment détecter qui a désactivé un compte utilisateur dans Active Directory
Audit Natif
- Exécutez gpedit.msc → Créez un nouveau GPO → Modifiez-le → Allez dans « Configuration de l'ordinateur » → Stratégies → Paramètres Windows → Paramètres de sécurité → Stratégies locales > Politique d'audit :
- Auditez la gestion des comptes → Définir → Succès.
- Allez dans Event Log → Définir :
- Taille maximale du journal de sécurité à 4 Go
- Méthode de conservation pour le journal de sécurité pour Écraser les événements selon les besoins.
- Associez le nouveau GPO à l'OU avec les comptes utilisateurs → Allez dans "Gestion de la stratégie de groupe" → Cliquez-droit sur l'OU défini → Choisissez "Lier un GPO existant" → Sélectionnez le GPO que vous avez créé.
- Forcez la mise à jour de la stratégie de groupe → Dans "Group Policy Management" → Cliquez avec le bouton droit sur l'unité d'organisation définie → Cliquez sur "Group Policy Update".
- Ouvrez ADSI Edit → Connectez-vous au contexte de nommage par défaut → Cliquez avec le bouton droit sur l'objet DomainDNS portant le nom de votre domaine → Propriétés → Sécurité (Onglet) → Avancé (Bouton) → Audit (Onglet) → Ajouter le principal « Tout le monde » → Type « Réussite » → S'applique à « Cet objet et les objets descendants » → Permissions → Sélectionnez toutes les cases à cocher sauf les suivantes :
- Contrôle total
- Liste des contenus
- Lisez toutes les propriétés
- Lisez les permissions → Cliquez sur « OK ».
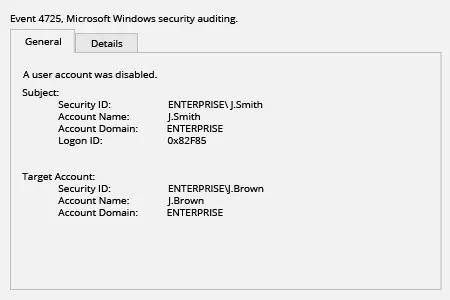
- Ouvrez l'Observateur d'événements et recherchez dans le journal de Sécurité les ID d'événement 4725 (catégorie de tâches de Gestion de compte utilisateur).
Netwrix Auditor for Active Directory
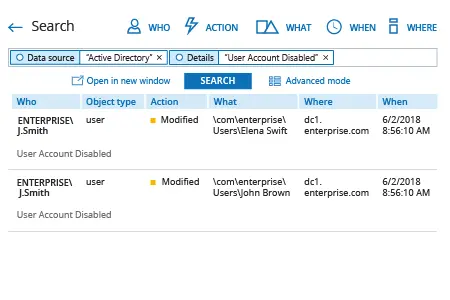
- Exécutez Netwrix Auditor → Allez dans "Recherche" → Cliquez sur "Mode avancé" si ce n'est pas sélectionné → Configurez les filtres suivants :
- Filter = "Source de données"
Operator = "Équivaut à"
Value = "Active Directory" - Filter = "Détails"
Operator = "Contient"
Value = "Compte utilisateur désactivé"
- Filter = "Source de données"
- Cliquez sur le bouton « Rechercher » et examinez qui a désactivé quels comptes d'utilisateur dans votre Active Directory.
Partager sur
