Netwrix Identity Management
Identity risk detection and analysis
Continuously detect risks like conflicting entitlements, SoD violations, and dormant accounts with Netwrix Identity Management
Why Netwrix for identity risk detection and analysis?
Gain continuous visibility into identity-based threats, enforce policy-based controls to prevent escalation, and reduce your attack surface with Netwrix Identity Management.

Identify hidden access risks
From dormant accounts to privilege creep and conflicting access rights, Netwrix discovers identity risks before they become breaches.
Apply policy-based controls
Define rules for segregation of duties (SoD), entitlement conflicts, inactive identities, and automatically enforce or remediate them with automated SoD enforcement.
Remediate identity risks
Automatically surface, prioritize, and act on identity risks so your security team can focus on the highest-impact issues.
Demonstrate compliance and governance
Detailed audit logs and risk-analysis reports help you prove control of identity risks to auditors, regulators, and stakeholders.
Features that enable identity risk detection and analysis
Example:
Dormant accounts reveal hidden risks
During a scheduled scan, Netwrix Identity Management detects multiple dormant user accounts that have not logged in for over three months. Several of these accounts still hold elevated privileges, creating potential entry points for attackers.
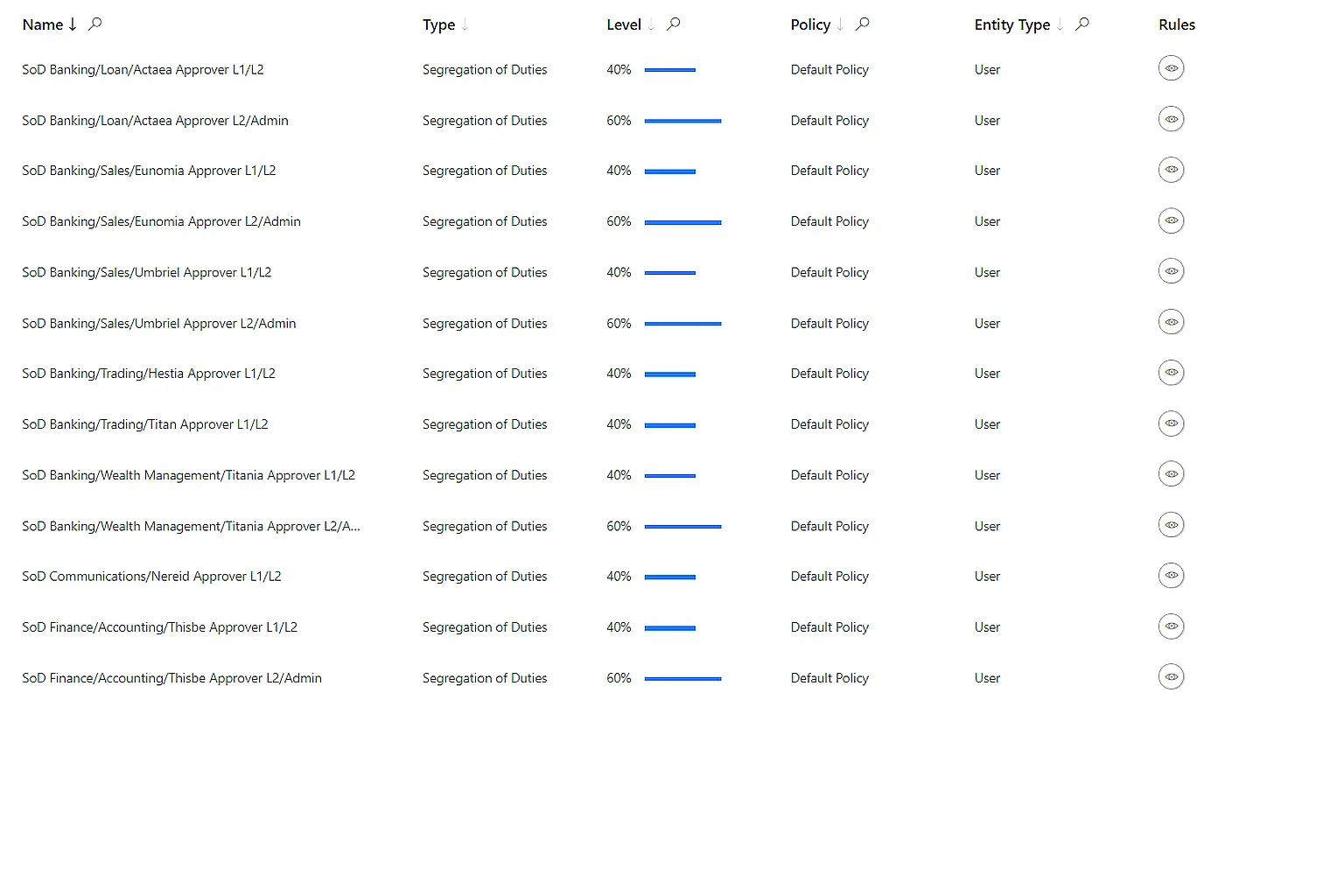
Segregation of duties conflicts identified
Further analysis uncovers a policy violation in the finance department where a user can both create and approve vendor payments. This conflicting combination breaches internal controls and introduces a fraud risk.
Automated policy enforcement remediates issues
Predefined policies automatically disable dormant accounts and revoke conflicting permissions. Notifications are sent to data owners for validation, and all corrective actions are logged for audit purposes.
Risk dashboards highlight remaining exposure
Security and compliance teams review dashboards displaying current identity risks ranked by severity. This visibility helps prioritize additional remediation and monitor the organization’s overall risk posture in real time.
Audit-ready reports confirm compliance
When auditors request evidence, IT exports detailed reports showing identified risks, remediation actions, and policy enforcement history. These records demonstrate continuous monitoring and effective governance.
Result
With Netwrix Identity Management, organizations detect and mitigate identity-related risks such as dormant accounts, privilege creep, and segregation of duties violations. Automated policy controls, real-time analytics, and detailed reporting reduce exposure, enforce least privilege, and simplify regulatory compliance.
Ready to get started?
"With Netwrix Identity Manager, we save a considerable amount of time — both in the IT team's day-to-day management and for access and rights management in general. Netwrix Identity Manager also detects any changes in new arrivals or rights granted somewhere else, so we can quickly get information and act upon it."
Michel Tournier, CIO
Wendel
