Netwrix Privileged Access Management (PAM)
Third-party vendor access
Grant temporary privileged access to contractors and vendors. Monitor external user sessions and automatically revoke access.
Why Netwrix for third-party vendor access?
Enable secure, controlled external access for vendors, contractors, and service providers — while monitoring sessions, enforcing least privilege, and automatically revoking access when the job is done.

Enable secure, temporary access for external users
Vendors and contractors often need privileged access to internal systems. Without proper controls this becomes a major attack vector. Vendor-PAM solutions help streamline access while enforcing security policies.
Monitor sessions and maintain full visibility
Recording and auditing third-party sessions is key to knowing “who did what, when.” This helps mitigate the risk of misuse, credential exposure, or supply-chain attacks.
Apply just-in-time & least-privilege controls
Grant vendors access only as long as necessary, to only what they require — reducing standing privileges and the attack surface.
Automate revocation and simplify governance
When tasks complete, vendor access should end automatically. PAM solutions enable automatic cleanup, audit trails, and ensure compliance with external access policies.
Key features of third-party vendor access with Netwrix PAM
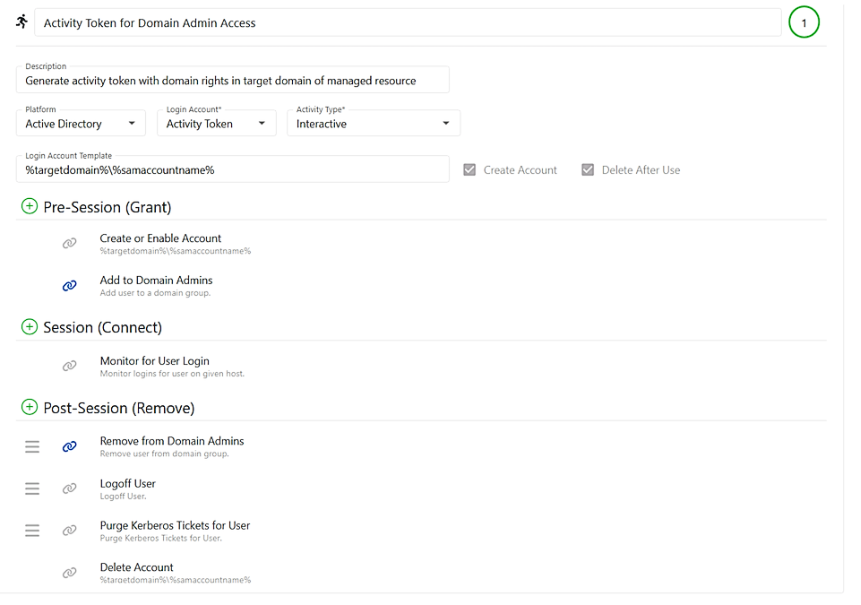
Example:
Vendor access request received
A third-party vendor submits a request for privileged access to complete scheduled maintenance on a critical system.
Access approved with time limits
The IT team uses Netwrix Privilege Secure to approve the request. The system automatically provisions temporary credentials valid only for the maintenance window.
Session monitored in real time
As the vendor connects, Netwrix Privilege Secure records the entire session, capturing keystrokes and screen activity. The security team can view the session live or review it later for audit purposes.
Task completed and access revoked
Once the vendor finishes the maintenance task, their privileged session ends and Netwrix Privilege Secure automatically revokes access, deletes temporary credentials, and logs all activity.
Audit report generated
A detailed session report is automatically created, showing who accessed what, when, and what actions were performed — helping the organization demonstrate compliance and maintain accountability for all third-party activity.
Result
With Netwrix Privilege Secure, organizations enable secure, temporary access for vendors and contractors, monitor all privileged sessions, and automatically revoke access once tasks are complete. This ensures least privilege, compliance, and protection against supply-chain threats without slowing down essential work.
Ready to get started?
"With Netwrix Privilege Secure we implemented privileged access management for our critical systems in days instead of months and it seamlessly integrated with our current systems and security controls."
Craig Larsen, Information Systems Administrator
Eastern Carver County Schools
