Netwrix Auditor: The NetApp Monitoring Software
Track every change and access event on your filers with intelligent NetApp monitoring that transforms logs into actionable insights.
Read their Stories
Trusted by





































































A comprehensive NetApp monitoring tool that works smarter
Detect data security threats
Gain visibility into suspicious changes and data access, anomalous user behavior, excessive access rights, and more.
Pass audits with ease
Provide reports mapped to the most common compliance regulations, including PCI DSS, HIPAA, SOX, GLBA, FISMA/NIST, CJIS, and GDPR.
Boost IT team productivity
NetApp monitoring software helps your IT team detect, investigate, and remediate changes faster so they can focus on the things that really matter.
Correlate activity across systems
Correlate NetApp activity with other systems to reveal the full story on attacks or insider threat behaviors.
Capabilities
Transform complexity into intelligence with NetApp monitoring software designed for modern storage environments
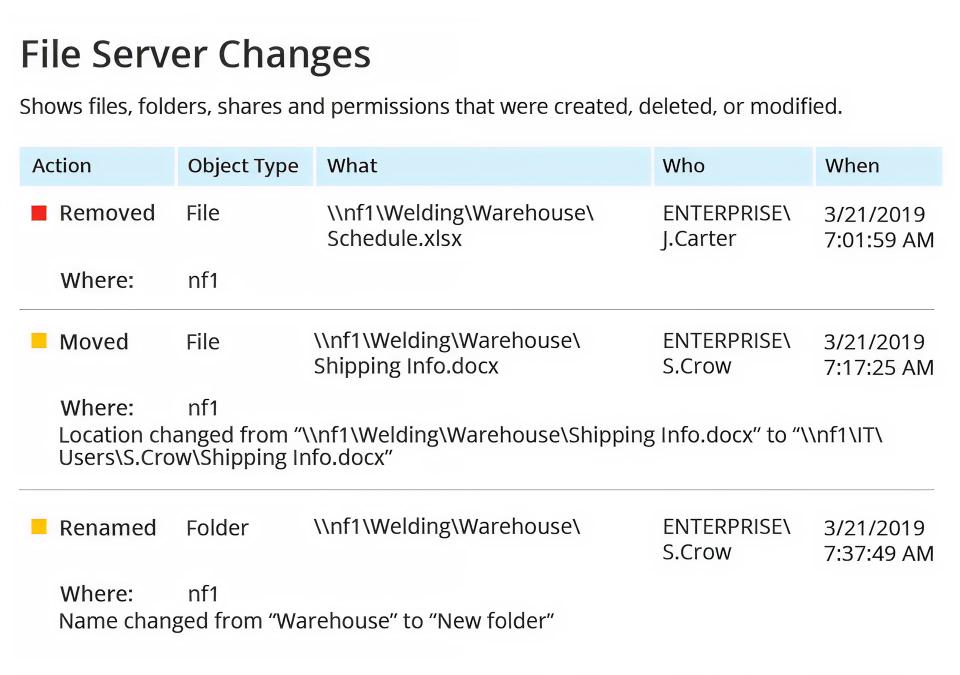
Ready to get started?
Solutions
Go beyond single-threat protection. Secure every angle with Netwrix solutions.






