How to check users in Windows 10 and Windows 11 using PowerShell
- Create a file containing the computer list → Open the PowerShell ISE by clicking on the Start button and typing “PowerShell ISE”→ Run the following script, adjusting the file name and path for the export:
$computers=Get-Content-PathC:\data\computers.txt
Get-WmiObject-ComputerName$computers-ClassWin32_UserAccount-Filter"LocalAccount='True'"|SelectPSComputername,Name,Status,Disabled,AccountType,Lockout,PasswordRequired,PasswordChangeable,SID|Export-csvC:\data\local_users.csv-NoTypeInformation
- Open the file produced by the script in MS Excel.
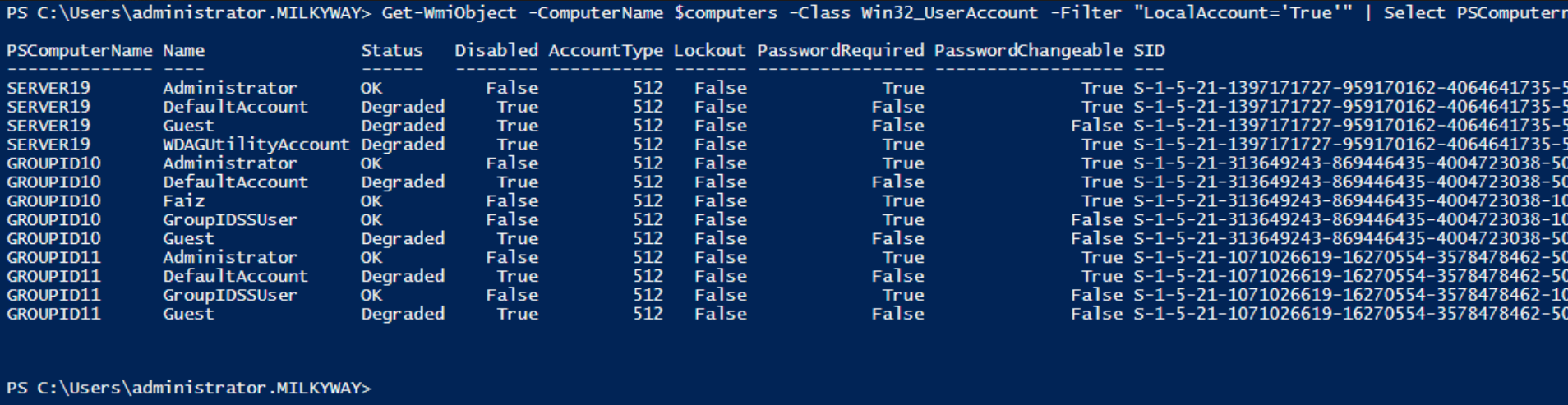
The PowerShell script does not produce an output because we save the results in a CSV file. To see the results in the PowerShell window, remove the last part where we save the output in CSV, and add the switch format table, like below.
Get-WmiObject-ComputerName$computers-ClassWin32_UserAccount-Filter"LocalAccount='True'"|SelectPSComputername,Name,Status,Disabled,AccountType,Lockout,PasswordRequired,PasswordChangeable,SID|format-table
Without the help of a format-table switch, the results would be shown user-by-user, expanding to multiple pages. Using the switch, the result will be formatted in a tabular form and will give you the output as below.
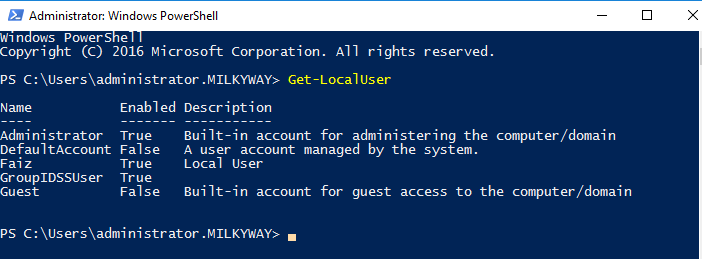
Get-LocalUser
The Get-LocalUser PowerShell cmdlet retrieves information about local user accounts on a Windows system. You can run this command in a PowerShell window to list local user accounts and their properties, including name, description, and status as enabled or disabled.
Get-LocalUser
This will display a list of local user accounts on the system in a row-wise manner; CMD lacks this by showing them randomly in one or two rows. Type “Get-LocalUser” in PowerShell and press Enter.
List local users in CMD
If you want to list Windows users who are currently logged in or have accounts on the system, you can use the net user command in the command prompt. This will list all user accounts on the system. Below is how to list users in cmd.
net user
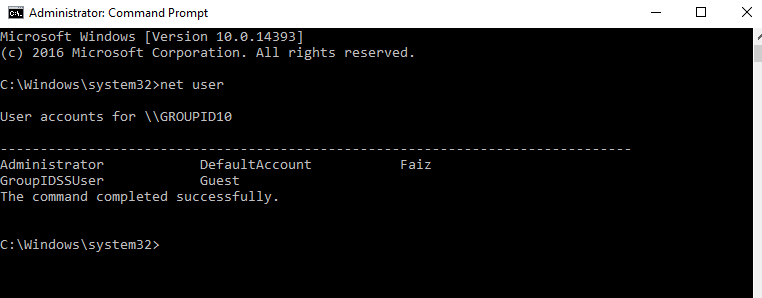
This Windows command line will show users in cmd.
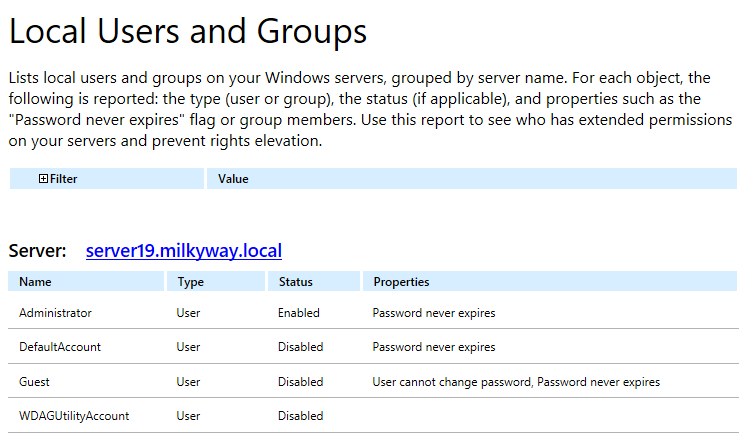
- Run Netwrix Auditor → Navigate to "Reports" → Expand the "Windows Server" section → Go to "Windows Server – State-in-Time" → Select "Local Users and Groups" → Click "View.". You can also search for reports.
- To save the report, click the "Export" button → Choose a format from the dropdown menu → Click "Save".