Endpoint Management
Close gaps across your security stack with Netwrix Endpoint Management — continuous and automatic policy enforcement for privileges, device control, USB protection, and beyond.
Read their Stories
Trusted by




































































Unsecure and inconsistent endpoint configurations in multi-OS environments lead to malware, data exfiltration, noncompliance, and downtime
Local admin rights invite malware threats
Local admin rights are required for some apps and processes, but they pose serious security risks.
Uncontrolled devices put data at risk
USBs, printers, Bluetooth, and all peripherals are potential exit points for data exfiltration.
Lost, stolen, and unencrypted USB drives
USB drives without remote management, data wiping, and password reset are compromised more easily.
Misconfigured settings and CIS controls
Unauthorized or accidental configuration changes lead to noncompliance and security vulnerabilities.
Use cases
Automatically enforce endpoint policies wherever users work
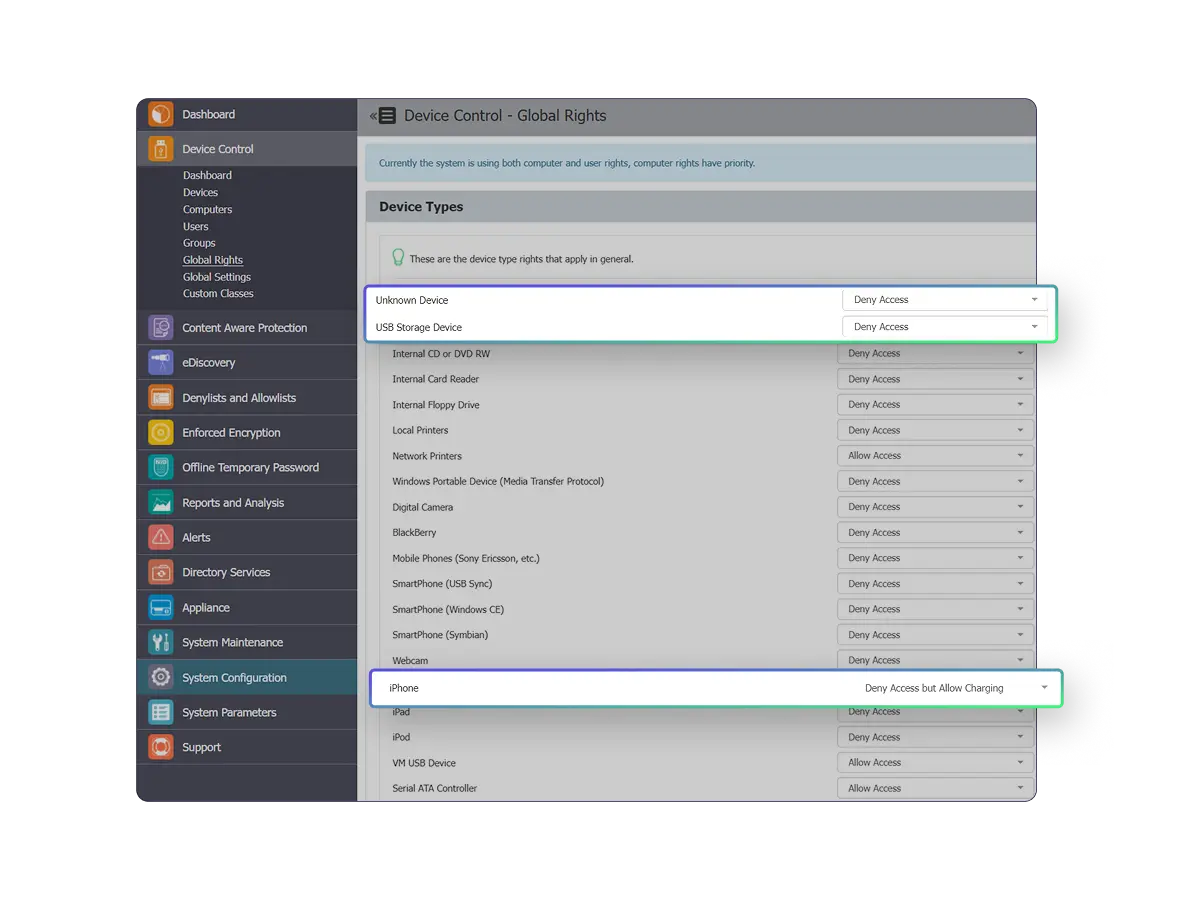
Device control
Manage and monitor USBs, ports, peripherals, printers, Bluetooth, and more. Prevent data loss with granular device control across operating systems.
USB security
Secure USB drives with FIPS-validated encryption and manage them centrally. Only Netwrix provides remote wipe, password reset, and granular controls.
Endpoint privilege management
Block unauthorized software installations while allowing approved business applications. Maintain productivity without compromising endpoint compliance standards.
Compliance monitoring
Monitor and baseline CIS controls across Windows, macOS, and Linux endpoints. Validate compliance with regulations like CMMC, PCI-DSS, HIPAA, and others.
Migrate GPOs to Microsoft Intune
Migrate on-prem GPOs to Microsoft Intune or other MDM service. Close CSP gaps, standardize settings for remote PCs, and achieve Group Policy parity.
GPO Management in the cloud
Create, edit, target, and link real Group Policy settings from a centralized cloud interface. Simplify endpoint management for non-domain-joined PCs.
The Netwrix approach
Policy-driven endpoint management that blends security with productivity
Get in touch
Let’s talk security
Protect your endpoints and close the policy enforcement gap
Unlike reactive endpoint security tools like EDR, antivirus, and SOAR, Netwrix takes a proactive approach. The Netwrix Endpoint Management solution closes security gaps across your existing tools by delivering continuous and automatic policy enforcement across Windows, macOS, and Linux operating systems. Netwrix fortifies your security posture, simplifies management, and validates compliance.

Complimentary, not competitive
Netwrix Endpoint Management tools are designed to fill the policy enforcement gaps that tools like EDR, MDM, and others leave behind.
Powerful, layered defense in depth
Remove local admin rights, block ransomware and unknownware, enforce USB encryption, and lock down apps and services based on network conditions.
Simplified management that unlocks productivity
Manage non-domain computers, accelerate login times, simplify software deployment, and delight users by improving desktop experiences.
Compliance without compromise
Gain the visibility and reporting capabilities needed to monitor policy drift, validate enforcement, and ensure security with frameworks like CIS.
Endpoint Management FAQs
Have questions? We’ve got answers.
See Endpoint Management in action