NetApp Reporting Software
Privacy Policy
What data can I get?
When auditing NetApp storage devices manually, you can spend a lot of time and effort sifting through cryptic native logs but still fail to find important events, like who removed critical data or modified access rights to it. This NetApp software reports on every critical change made to files, folders, shares, permissions and configurations across your NetApp systems, so you can spot and remediate unwanted modifications before they cause real damage.
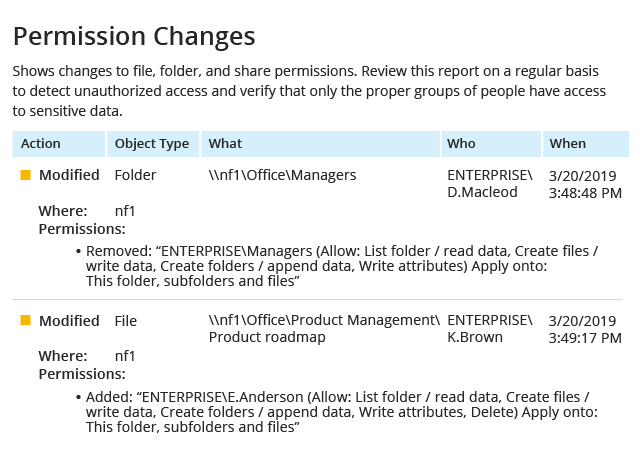
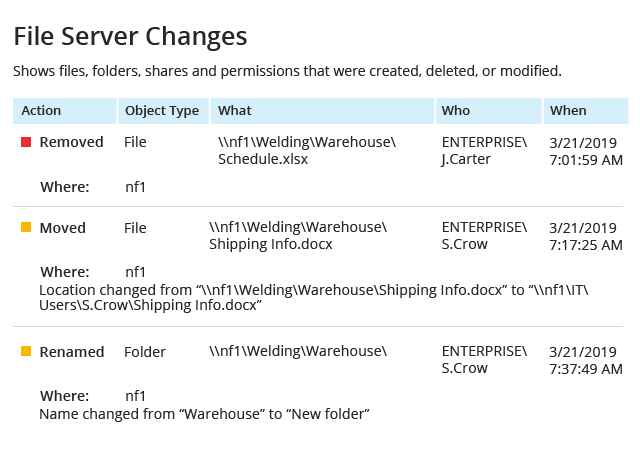
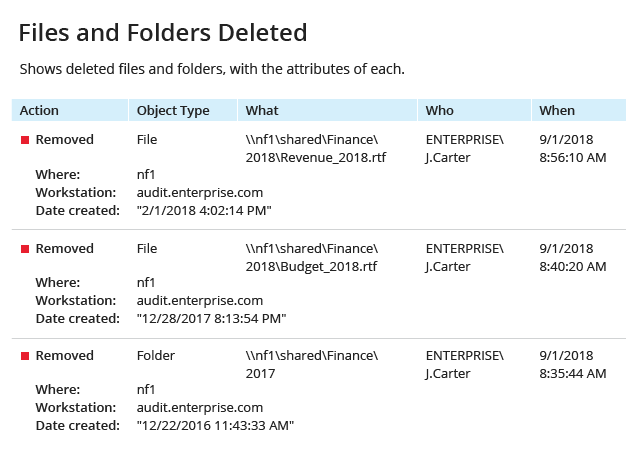
When auditing NetApp storage devices manually, you can spend a lot of time and effort sifting through cryptic native logs but still fail to find important events, like who removed critical data or modified access rights to it. This NetApp software reports on every critical change made to files, folders, shares, permissions and configurations across your NetApp systems, so you can spot and remediate unwanted modifications before they cause real damage.
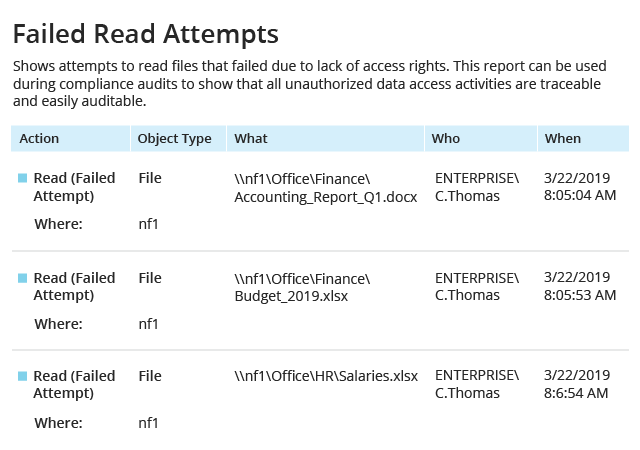
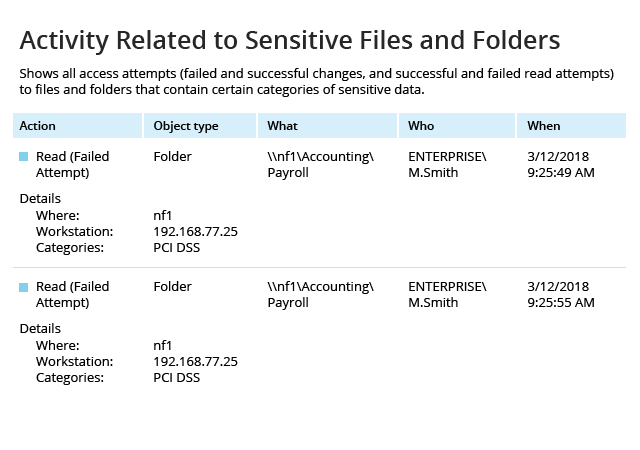
Native logs are noisy and contain so many access events that it's hard to dig out the truly valuable information. This NetApp reporting software from Netwrix empowers you to gain control over user activity by providing actionable reports on both successful and failed access attempts to your data, so you can quickly detect suspicious attempts to access sensitive data.
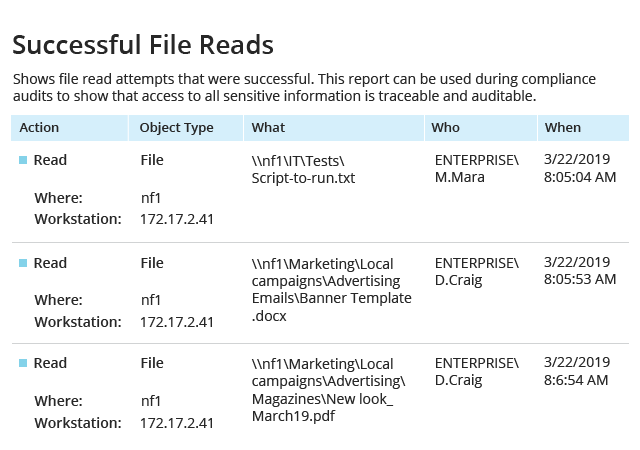
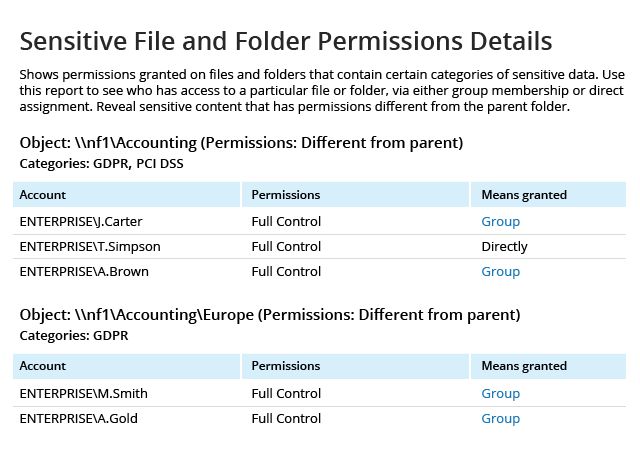
To ensure that your customer data and business-critical documents stay secure, you need to systematically check which users and groups have access to them. With Netwrix, you can quickly review effective permissions to files and folders in your NetApp environment and ensure they are in line with internal policies and the least-privilege principle.
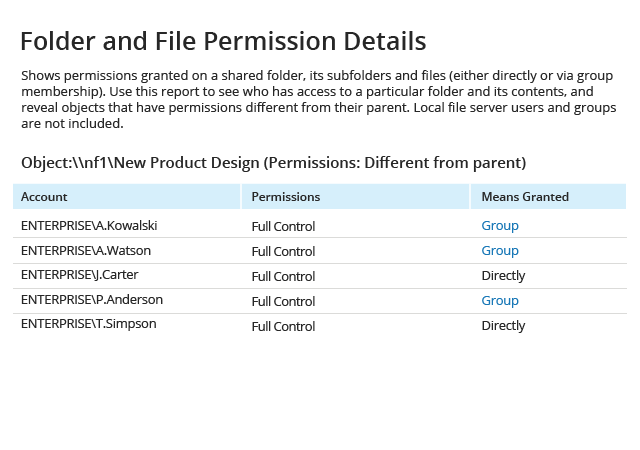
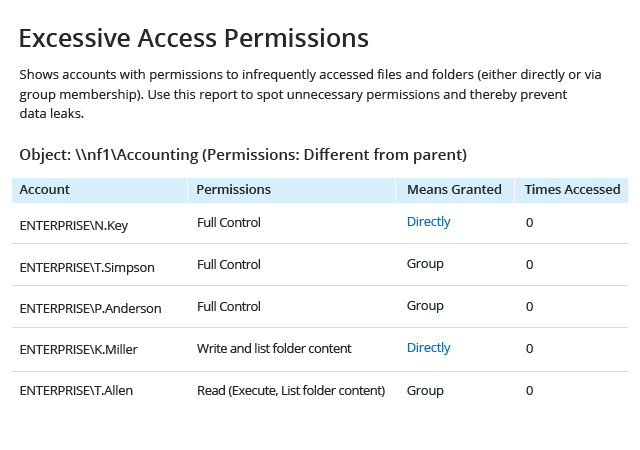
To ensure that your customer data and business-critical documents stay secure, you need to systematically check which users and groups have access to them. With Netwrix, you can quickly review effective permissions to files and folders in your NetApp environment and ensure they are in line with internal policies and the least-privilege principle.
In order to protect your sensitive files and comply with regulatory standards, you need to know what kinds of information is stored in your IT infrastructure, exactly where that data is located, and who has access to it, as well as stay informed about every action that might threaten it. Netwrix Auditor in combination with Netwrix Data Classification identifies the types of sensitive information you store, their location and whether this data is overexposed. Plus, you can quickly check who has access to critical data and get a clear picture of what’s going on around it. Regularly review this information to minimize the risk to data security.
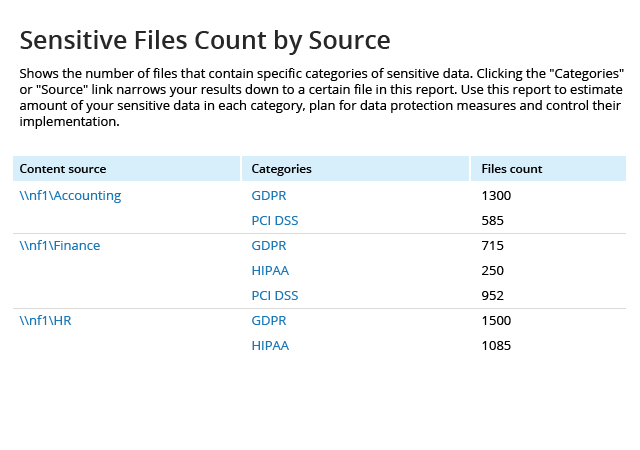
Not every NetApp filer storage reporting tool can help you effectively analyze your data structure and usage patterns. File analysis reports from Netwrix deliver information on data ownership, data usage, data volumes, empty folders, and stale and duplicate files, so you can optimize space on your file servers and improve your storage management processes.
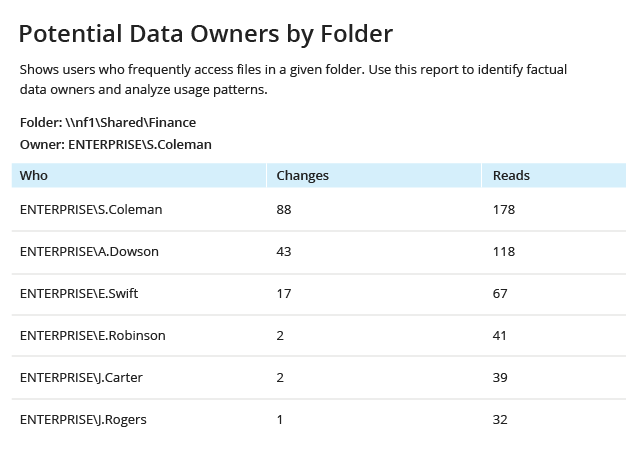
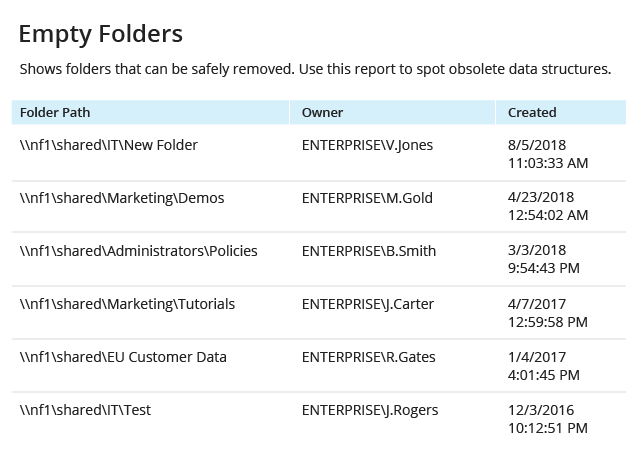

Not every NetApp filer storage reporting tool can help you effectively analyze your data structure and usage patterns. File analysis reports from Netwrix deliver information on data ownership, data usage, data volumes, empty folders, and stale and duplicate files, so you can optimize space on your file servers and improve your storage management processes.
How can I use this data?
Without a 360-degree view of your IT infrastructure, it’s hard to find weak spots. Netwrix Auditor’s Risk Assessment dashboard pinpoints the most critical misconfigurations, such as potentially harmful files stored across your servers, file names that indicate they contain sensitive data or folders with permissions granted to everyone, so you can remediate these IT risks before they result in data leaks.
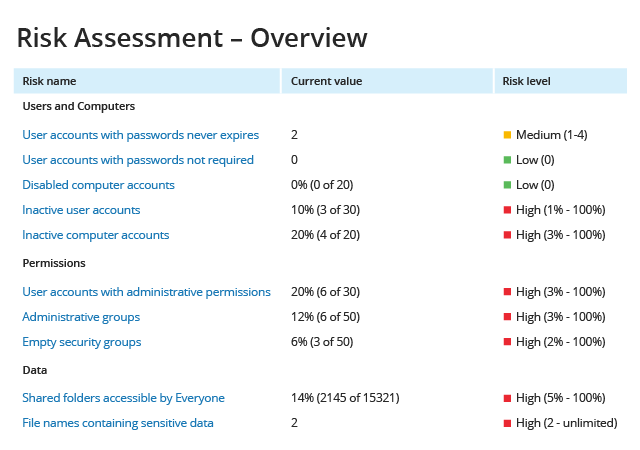
Without a 360-degree view of your IT infrastructure, it’s hard to find weak spots. Netwrix Auditor’s Risk Assessment dashboard pinpoints the most critical misconfigurations, such as potentially harmful files stored across your servers, file names that indicate they contain sensitive data or folders with permissions granted to everyone, so you can remediate these IT risks before they result in data leaks.
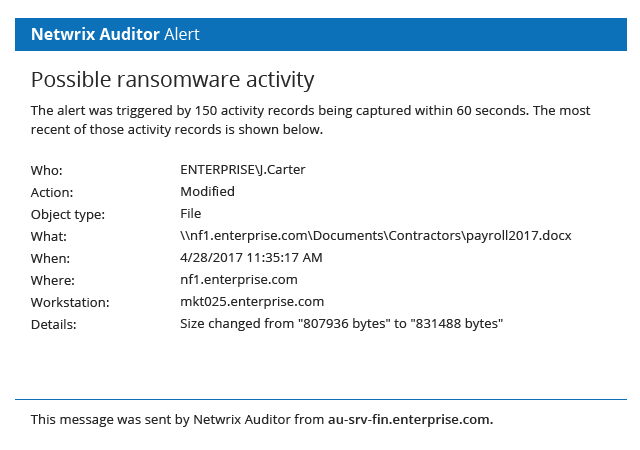
To maximize data protection, you need to constantly monitor suspicious actions around your sensitive data. For instance, the sooner you spot a ransomware attack, the better your chances of saving most of your critical data. With threshold-based alerting from Netwrix, you’ll be the first to know about critical events, such as when someone is trying to modify too many files at a time, so you can block such attacks before it’s too late.
If an attack involves a chain of malicious actions stretching across NetApp ONTAP systems, basic alerts might not be enough. Netwrix Auditor provides a unified view of all anomalous activity alerts triggered by an individual across all audited systems and the cumulative risk score so you can spot malicious insiders and compromised accounts — even if they cover their tracks carefully.
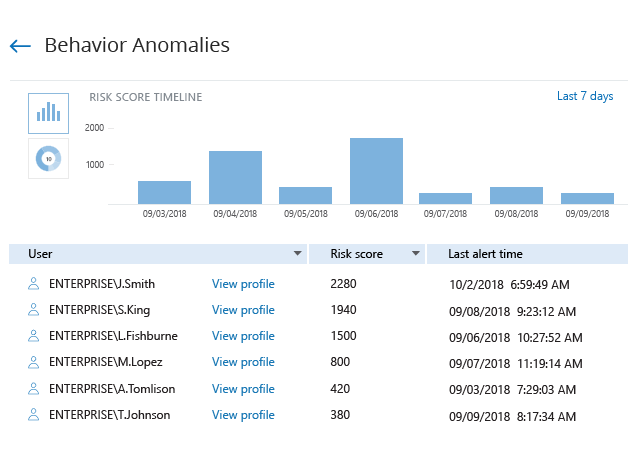
If an attack involves a chain of malicious actions stretching across NetApp ONTAP systems, basic alerts might not be enough. Netwrix Auditor provides a unified view of all anomalous activity alerts triggered by an individual across all audited systems and the cumulative risk score so you can spot malicious insiders and compromised accounts — even if they cover their tracks carefully.
To strengthen the security of your sensitive data, it’s critical to find even subtle signs of account compromise, such as suspicious surges in data access or activity outside business hours. With reports on user behavior and blind spot analysis, you can quickly identify these subtle indicators of threats and remediate them promptly.
Whenever you need to investigate a security incident or figure out what caused downtime or performance issues, Netwrix Auditor’s Interactive Search saves you from having to painstakingly dig this information out of native audit logs. Quickly sift through your audit data and get answers, such as who deleted a financial document, who gave excessive permissions to a contractor or exactly how an administrator changed file access permissions. Plus, it’s easy to create custom reports and alerts based on your search criteria to stay aware of similar incidents in the future.
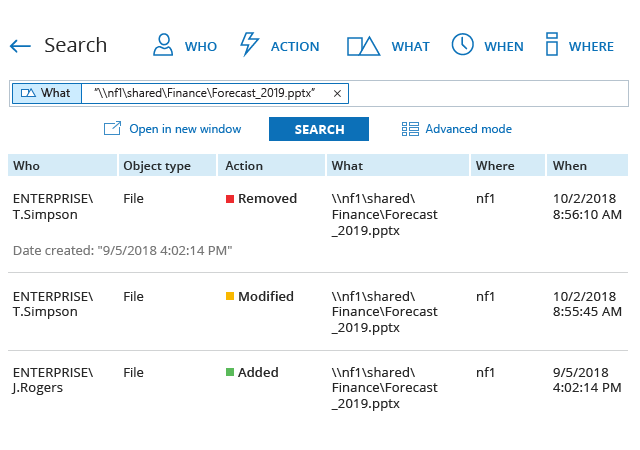
Whenever you need to investigate a security incident or figure out what caused downtime or performance issues, Netwrix Auditor’s Interactive Search saves you from having to painstakingly dig this information out of native audit logs. Quickly sift through your audit data and get answers, such as who deleted a financial document, who gave excessive permissions to a contractor or exactly how an administrator changed file access permissions. Plus, it’s easy to create custom reports and alerts based on your search criteria to stay aware of similar incidents in the future.
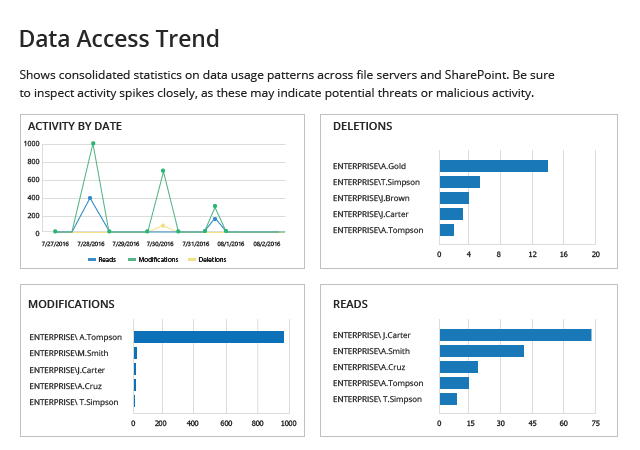
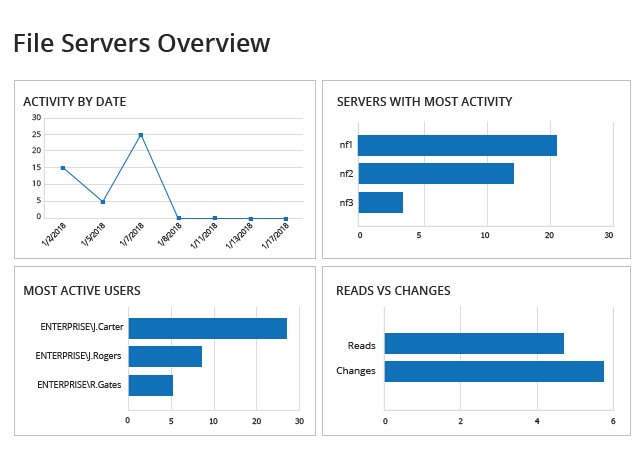
It’s easy to miss an important piece of information while crawling through the cryptic native logs. To spot unusual surges in user activity, you need a single-pane-of-glass view. Netwrix Auditor’s overview dashboard shows activity by date, along with the users who are most active, the file systems that are most frequently changed and the number of reads compared to the number of changes.
Even if you meticulously monitor your file servers, it can still be challenging to demonstrate to auditors that you are complying with specific regulatory requirements. With Netwrix, you can forget about spending time creating multiple reports to demonstrate your compliance. Simply provide auditors with ready-to-use compliance reports tailored to PCI DSS, HIPAA, GDPR, SOX, GLBA, FISMA/NIST and other common regulatory standards, so you can pass compliance audits faster and with less effort.
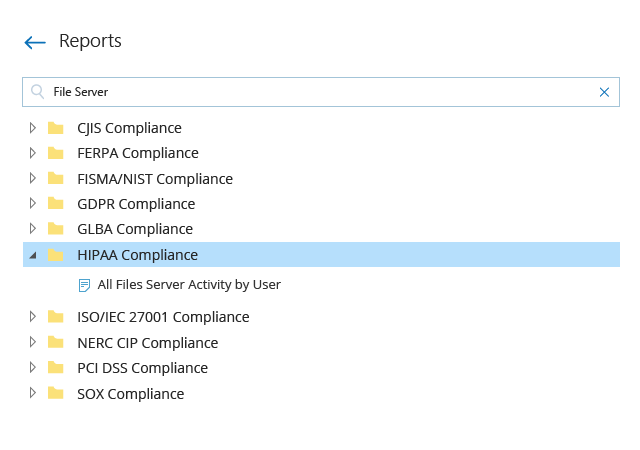
Even if you meticulously monitor your file servers, it can still be challenging to demonstrate to auditors that you are complying with specific regulatory requirements. With Netwrix, you can forget about spending time creating multiple reports to demonstrate your compliance. Simply provide auditors with ready-to-use compliance reports tailored to PCI DSS, HIPAA, GDPR, SOX, GLBA, FISMA/NIST and other common regulatory standards, so you can pass compliance audits faster and with less effort.
What else do I get with Netwrix Auditor
for NetApp?
With a RESTful API, Netwrix Auditor can be integrated with any ecosystem, so you can audit file storages and your other commercial or custom applications from a single place. Free, ready-to-use add-ons are available for many common applications, including SIEM solutions.
With a RESTful API, Netwrix Auditor can be integrated with any ecosystem, so you can audit file storages and your other commercial or custom applications from a single place. Free, ready-to-use add-ons are available for many common applications, including SIEM solutions.
With a RESTful API, Netwrix Auditor can be integrated with any ecosystem, so you can audit file storages and your other commercial or custom applications from a single place. Free, ready-to-use add-ons are available for many common applications, including SIEM solutions.
Routine tasks, like locking users that generated multiple failed access events, can distract you from more important duties. With Netwrix, you can automatically handle tasks like these by embedding scripts in alerts, which ensures a prompt response and saves you valuable time.
Routine tasks, like locking users that generated multiple failed access events, can distract you from more important duties. With Netwrix, you can automatically handle tasks like these by embedding scripts in alerts, which ensures a prompt response and saves you valuable time.
Routine tasks, like locking users that generated multiple failed access events, can distract you from more important duties. With Netwrix, you can automatically handle tasks like these by embedding scripts in alerts, which ensures a prompt response and saves you valuable time.
Native tools don’t provide an easy way to retain all audit data. Netwrix Auditor securely stores your audit trail in a two-tiered (file-based + SQL database) storage for more than 10 years, while enabling quick and easy access to the archived data for historic reviews and legal inquiries.
Native tools don’t provide an easy way to retain all audit data. Netwrix Auditor securely stores your audit trail in a two-tiered (file-based + SQL database) storage for more than 10 years, while enabling quick and easy access to the archived data for historic reviews and legal inquiries.
Native tools don’t provide an easy way to retain all audit data. Netwrix Auditor securely stores your audit trail in a two-tiered (file-based + SQL database) storage for more than 10 years, while enabling quick and easy access to the archived data for historic reviews and legal inquiries.
To ensure that your auditing process is secure, Netwrix Auditor empowers you to granularly assign the appropriate access rights to everyone who needs them, so you can be confident that only authorized personnel can view security analytics, export audit data and configure settings.
To ensure that your auditing process is secure, Netwrix Auditor empowers you to granularly assign the appropriate access rights to everyone who needs them, so you can be confident that only authorized personnel can view security analytics, export audit data and configure settings.
To ensure that your auditing process is secure, Netwrix Auditor empowers you to granularly assign the appropriate access rights to everyone who needs them, so you can be confident that only authorized personnel can view security analytics, export audit data and configure settings.

Learn more about how Netwrix Auditor for NetApp can help you streamline NetApp storage reporting, strengthen data security and prove compliance.

Get a convenient list of functionality of Netwrix Auditor for NetApp in a fill-in-the-blank format that streamlines comparing it with other NetApp monitoring products.
Deploy Netwrix Auditor wherever you need it
Download a free 20-day trial of Netwrix Auditor and deploy it on Microsoft Windows Server.
Download our virtual appliance and start using Netwrix Auditor without having to provision any hardware or software.
