The 7 Pillars of Zero Trust
Organizations are increasingly adopting a Zero Trust model to improve their cybersecurity and cyber resilience. This paper explains what Zero Trust is, its key benefits and challenges, and the seven pillars of a Zero Trust implementation.
What is Zero Trust?
Traditional cybersecurity strategy was based on perimeter-based framework: The key focus was to prevent malicious entities from entering the network. Users, processes, devices, and other entities within the perimeter, on the other hand, were granted broad access to IT resources. The term “we have a rather flat network” was used to describe that everyone inside the perimeter could see and access everything (or almost everything), and no internal boundaries were set up.
However, the distinction between in-network and out-of-network entities has become increasingly blurred over the years due to factors like remote work, bring-your-own-device (BYOD) policies, and complex supply chains. Moreover, incident forensics have revealed that threat actors who breach a network, often by stealing or guessing legitimate user credentials, often lurk inside for weeks, months, or even years, stealthily moving laterally and escalating their rights until they can access sensitive systems or data. In addition, the owners of credentials themselves can do damage, either deliberately or through errors or negligence.
To address these realities, Zero Trust offers a new approach to cybersecurity, which is summarized as "never trust, always verify." In practice, Zero Trust includes a variety of security controls, including the following:
- Risk-based re-authentication — No user, process or other identity should be authenticated once and then given free rein to access IT resources — even if the initial access is confirmed via multi-factor authentication (MFA). Instead, the risk of each access request should be assessed based on a range of factors; if the risk exceeds a defined threshold, additional authentication should be required. Examples of factors include the time and location of the request, how the resources being requested are classified (such as public, secret or top secret), characteristics of the requesting device (such as software version details), and behavioral analytics regarding normal activity patterns for the entity
- Strict adherence to the least-privilege principle — In addition, Zero Trust requires that access be granted to only the resources needed to complete a particular task and should be time-limited. This limits the damage that any identity in the network can do, whether it is being used by its legitimate owner or has been compromised by an adversary.
- Close monitoring of activity — To ensure prompt detection of threats, Zero Trust requires continuous monitoring of activity across the IT infrastructure, including the actions of end users, admins, service accounts, devices and so on.
What are the 7 pillars of Zero Trust?
The Department of Defense (DoD) "Zero Trust Reference Architecture" lays out seven interlocking pillars for implementing Zero Trust principles:
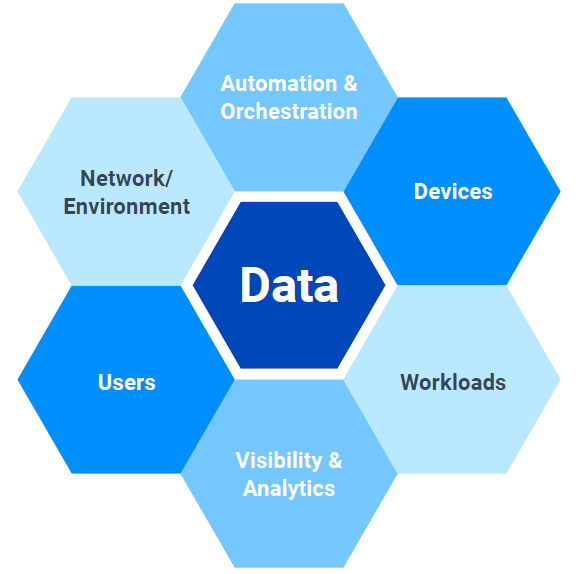
- Users — This area involves all processes related to authenticating user identities and managing their privileges. Examples include identity and access management (IAM), privileged access management (PAM), and multi-factor authentication.
- Devices — This pillar involves authenticating device identities and ensuring devices meet security standards, such as having up-to-date software and no non-approved components. Tools for device security include continuous diagnostics and mitigation (CDM) systems, mobile device management (MDM) solutions and trusted platform modules (TPMs).
- Network/Environment — This area involves isolating and controlling the network, including both on-site and off-site environments. Key network security strategies include fine-grained access permissions and micro- and macro-segmentation.
- Applications and Workload— This pillar includes all tasks performed by software. Proxy technologies can be useful here.
- Data — This area includes all data that the organization stores and processes. A comprehensive data management strategy includes controls like data access reviews to enforce least privilege and encryption to protect data that falls into the wrong hands.
- Visibility and Analytics — This pillar involves the analysis of network and system activity to detect threats. Relevant technologies include network and system activity logs, threat intelligence feeds, and SIEM tools.
- Automation and Orchestration — This area involves automating security processes such as threat detection and response to improve the speed and consistency of security policy implementation.
What is a Zero Trust architecture?
To implement the Zero Trust pillars, organizations need to build a Zero Trust architecture. NIST SP 800-207 “Zero Trust Architecture” details the key components:

In the center of the figure are the policy components:
- Policy engine (PE) — Gathers data about a request and uses enterprise policies to determine whether to approve the request
- Policy administrator (PA) — Takes an authentication decision from the PE and generates (or does not generate) credentials or tokens to allow a session
- Policy enforcement point (PEP) — Manages the connection between the requesting device and the private resource based on commands sent by the PA.
On the left and right sides are the data sources that feed the PE:
- Continuous diagnostics and mitigation (CDM) system — Gathers information on the characteristics of the requesting device
- Industry compliance system — Encodes policy rules to help ensure compliance with applicable regulations such as FISMA or HIPAA
- Threat intelligence feeds — Provides information about attacks or vulnerabilities relevant to the access control process
- Network and system activity logs — Records information about events within the network to improve threat detection and measure anomalous behavior
- Data access policies — Defines the fundamental rules which determine which subjects are permitted to access a given resource at a given time
- Security information and event management (SIEM) system — Gathers and analyzes data from various sources to identify security threats
- Identity management system — Manages the identity records for accounts requesting access to resources
What are the challenges in implementing Zero Trust?
The key challenges in implementing a Zero Trust model include the following:
- Migrating from legacy systems — Most organizations cannot implement Zero Trust from the ground up; instead, they must gradually replace existing systems and processes with Zero Trust alternatives. Throughout the migration period, they need to maintain strong security by ensuring that old and new components work together smoothly.
- Building robust data sources — Another implementation challenge lies in collecting sufficient data to feed to the PE to enable reliable authentication decisions. This requires detailed knowledge of enterprise assets, subjects and business processes.
- Securing policy components — To prevent disruption to authentication processes and therefore business operations, organizations need to protect the PE, PA and PEP. They should be placed in a secure environment or replicated to several environments. In addition, they should be carefully monitored, with any configuration changes logged and audited.
- Fostering user acceptance — Since Zero Trust requires minimizing permissions and requesting reauthentication for riskier access requests, users may experience frustration at the changes. To reduce security fatigue, be careful not to remove access rights that users actually need and require MFA only when it is warranted. More broadly, fostering a Zero Trust mindset by explaining the security benefits. It is also worth clearing up the misconception that "Zero Trust" means a lack of trust in employees as people; explain that it simply refers to not automatically trusting any device, system, user or other entity.
- Managing the right level of permissions – Minimizing permissions is not equal to zero permissions, users will still have a set of permissions once they are authenticated but should not get all the permissions that are available. A Microsoft report from 2023 highlights a risky gap between permissions granted and permissions used in the cloud, as identities use just 1% of the permissions granted to them. To handle that, make sure that a user's role(s) and the granted permissions for that role are well-managed and reduced to the minimum possible. In addition, having a process in place that allows for either just-in-time exceptions or an audited self-service way of assigning the needed right will make operations of zero trust easier.
Conclusion
Implementing a Zero Trust security model is not a quick and easy task, but the 7 Zero Trust pillars provide a solid foundation for identifying the tools and processes you need. The good news is that you don’t have to implement all of them to see the benefits: Each step in building out your Zero Trust architecture will enhance your cybersecurity and cyber resilience.
Click here to edit

