Netwrix Endpoint Protector: Endpoint DLP and Device Control Solution
Protect every exit point with endpoint data loss prevention and device control. Discover, monitor, and secure sensitive data across Windows, macOS, and Linux.
Read their Stories
Trusted by





































































An industry-leading endpoint DLP solution that protects all exit points
Meet regulatory compliance requirements
Achieve regulatory compliance with CMMC, ISO 2700, PCI-DSS, NIST, and others by securing CUI, controlling removable storage, and protecting PII.
Multi-OS protection with full feature parity
Get full DLP feature parity across Windows, macOS, and Linux to protect sensitive data at every exit point across your endpoint environment.
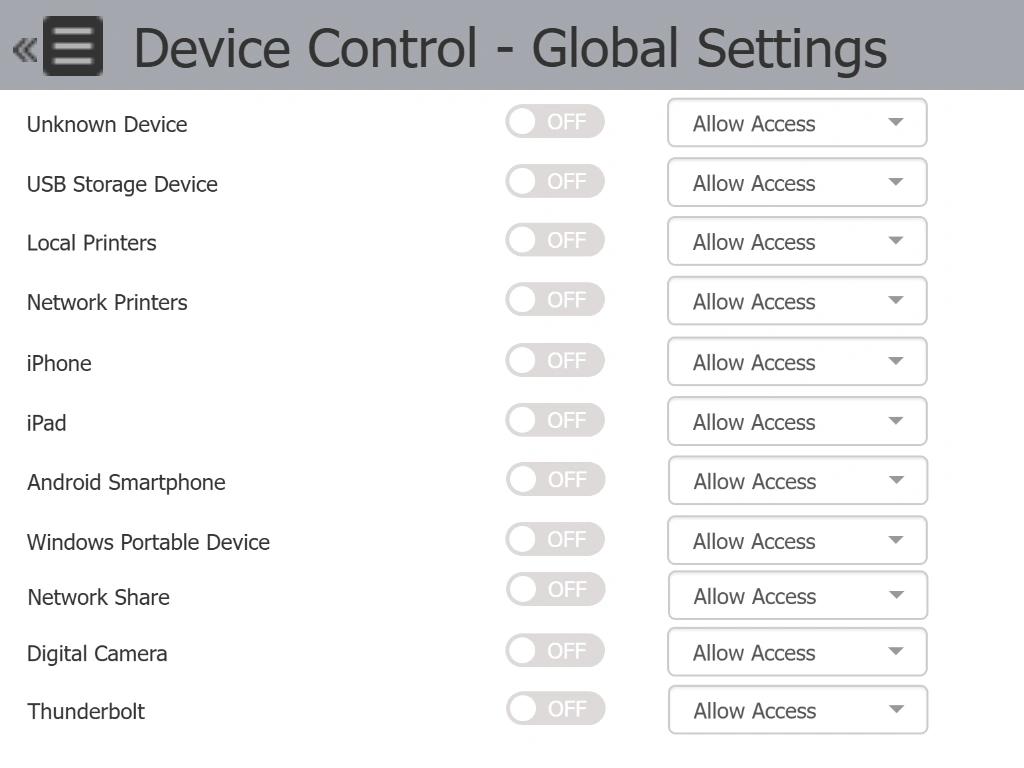
Protect against insider threats
Prevent data leakage and theft with granular DLP policies to secure devices, ports, apps, storage, printers, USBs, and more — even offline.
Secure PII and intellectual property
Protect source code, PII, and confidential data at rest and in motion by controlling transfers across apps, devices, and other exit points.
Capabilities
Complete endpoint DLP software that stops data loss with real-time monitoring and automated controls
Ready to get started?
Solutions
Go beyond single-threat protection. Secure every angle with Netwrix solutions.
Trusted by professionals
Don’t just take our word for it






