Netwrix PingCastle: Entra ID & Active Directory Security Assessment Tool
Find and fix AD and Entra ID security gaps fast with a hybrid Active Directory security assessment tool that delivers clear insights and remediation guidance.
Read their Stories
Trusted by




































































Active Directory risk assessments made actionable
Trusted worldwide
Trusted by 45,000+ domains in 193 countries, our AD assessment tool delivers proven reliability and security at global scale.
Comprehensive coverage
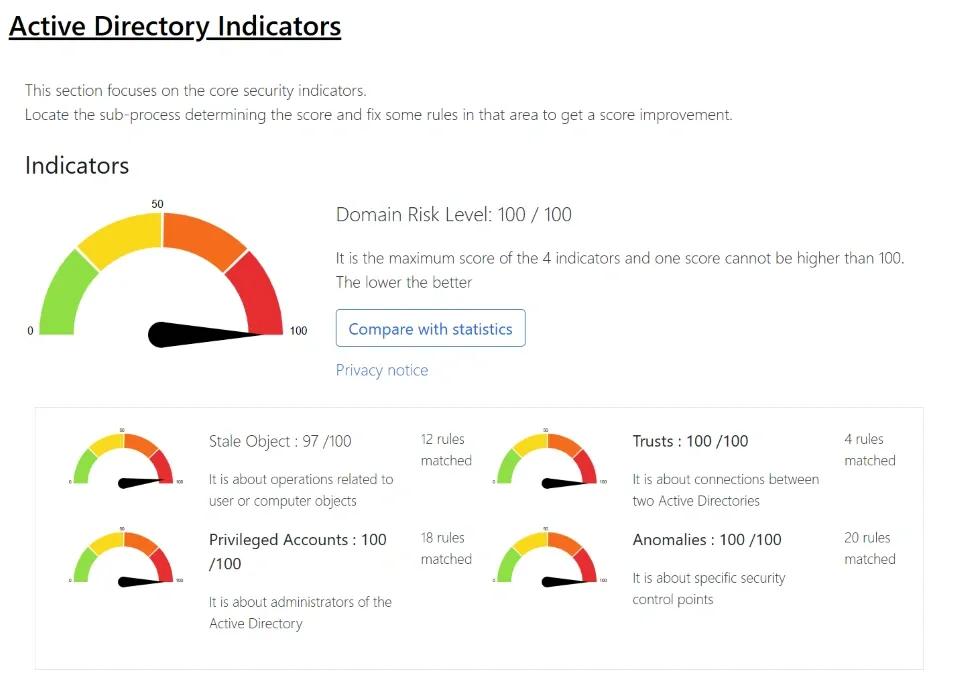
Detect 170+ hybrid identity risks to safeguard your environment with proactive insights.
Standards-based
Mapped to MITRE™ and ANSSI controls, our solution ensures compliance and validated protection for evolving threats.
Clear remediation guidance
Receive actionable steps to fix identified risks with immediate recommendations that strengthen your security position.
Now available in the cloud
Use PingCastle as part of the Netwrix 1Secure platform for simplified deployment and centralized risk management.
Capabilities
Actionable Active Directory security assessment insights that uncover security gaps, prioritize fixes, and strengthen your identity infrastructure across environments

Go further with Enterprise Edition
The free edition gives you fast visibility with manual scans. Enterprise adds scheduled assessments, risk remediation tracking, multi-domain coverage and more.
Solutions
Go beyond single-threat protection. Secure every angle with Netwrix solutions.
Trusted by professionals
Don’t just take our word for it






Let’s talk security
Active Directory security assessment FAQs
Have questions? We’ve got answers.
See PingCastle in action
PingCastle Datasheet