Abusing Entra ID Application Permissions – How It Works and Defense Strategies
Abusing Entra ID (formerly Azure AD) application permissions is an advanced attack technique where adversaries exploit misconfigured or over-privileged application registrations, consent grants, and delegated/static credentials in Microsoft Entra ID to gain unauthorized access, escalate privileges, exfiltrate data, or maintain persistent access. The primary goal is to abuse legitimate app permissions to act on behalf of users or the tenant without needing traditional credential theft.
Attribute | Details |
|---|---|
|
Attack Type |
Entra ID application permission abuse |
|
Impact Level |
High |
|
Target |
Cloud tenants, SaaS consumers, enterprises, governments |
|
Primary Attack Vector |
Misconfigured app registrations, excessive consent, compromised app secrets/certs, OAuth flows |
|
Motivation |
Data exfiltration, lateral cloud-to-on-prem escalation, persistence, tenant takeover |
|
Common Prevention Methods |
Least-privilege app design, consent restrictions, certificate-based auth, conditional access, continuous consent/permission auditing |
Risk Factor | Level |
|---|---|
|
Potential Damage |
Very High |
|
Ease of Execution |
Medium |
|
Likelihood |
Medium to High |
What is Entra ID Application Permission Abuse?
Entra ID application permission abuse occurs when attackers leverage application-level permissions (application permissions, delegated permissions, admin consented scopes), misconfigured OAuth consent, leaked client secrets/certificates, or abused service principals to perform privileged actions in a tenant. Unlike password-based compromises, this technique uses legitimate platform mechanisms (OAuth tokens, app roles, Graph API calls) so malicious actions often appear as normal application activity.
How Does Application Permission Abuse Work?
Below is a step-by-step breakdown of typical techniques and stages attackers use to exploit Entra ID application permissions.
1. Gain an initial foothold
Attackers first obtain any foothold related to the target cloud tenant. Common entry points include phishing (to gain delegated user consent), compromised user accounts, leaked app client secrets from repos/config, stolen certificate/private key for an app, or abusing weak admin consent workflows.
2. Discover registered applications and permissions
Once inside, attackers enumerate service principals and application registrations to identify apps with high-privilege permissions (e.g., Application.ReadWrite.All, Directory.ReadWrite.All, Mail.ReadWrite, Group.ReadWrite.All). Enumeration can be done via Microsoft Graph queries, Azure AD portal access, or using delegated tokens to list enterprise apps and their granted scopes.
3. Identify exploitable consent and delegation paths
Attackers look for apps that were admin-consented, apps with overly broad delegated scopes, legacy endpoints that allow implicit grant, or poorly protected confidential client credentials (secrets/certificates). They specifically hunt for apps that allow background access (application permissions) which do not require a signed-in user.
4. Exfiltrate/steal app credentials or abuse consent
If client secrets or certificates are discoverable (in pipelines, repos, config files, or Key Vault with weak access), attackers extract them and exchange for tokens. In delegated-consent flows, attackers may trick privileged users into consenting to malicious app scopes (consent phishing). They may also leverage consent-granting features in multi-tenant apps.
5. Acquire tokens and perform privileged actions
Using stolen/abused credentials or granted consent, attackers request OAuth access tokens (application tokens for app permissions or delegated tokens on behalf of users) and call Microsoft Graph or other APIs to list users, read mail, download OneDrive files, modify directory objects, or create backdoors (new app registrations or custom roles).
6. Escalate, persist, and move laterally
With application permissions, attackers can create new service principals, add credentials, assign roles, or exfiltrate data at scale. Because app tokens can be valid for long periods and operations often look legitimate, attackers can maintain persistence and move from cloud to on-premises dependencies (e.g., syncing identity information, modifying hybrid connectors).
✱ Variant: Consent Phishing & Rogue Multi-Tenant Apps
Trick privileged users to grant broad permissions. Attackers host seemingly benign apps that request dangerous scopes and use social engineering to get admin or privileged users to consent. Once consented, the app can act tenant-wide. Rogue multi-tenant apps can be used to harvest admin consent from many tenants.
Abuse of legacy OAuth flows and implicit grants: Older OAuth flows or misconfigured redirect URIs can enable token theft or consent bypasses. Attackers exploit these to gain delegated tokens without interactive user flow protections.
Attack Flow Diagram
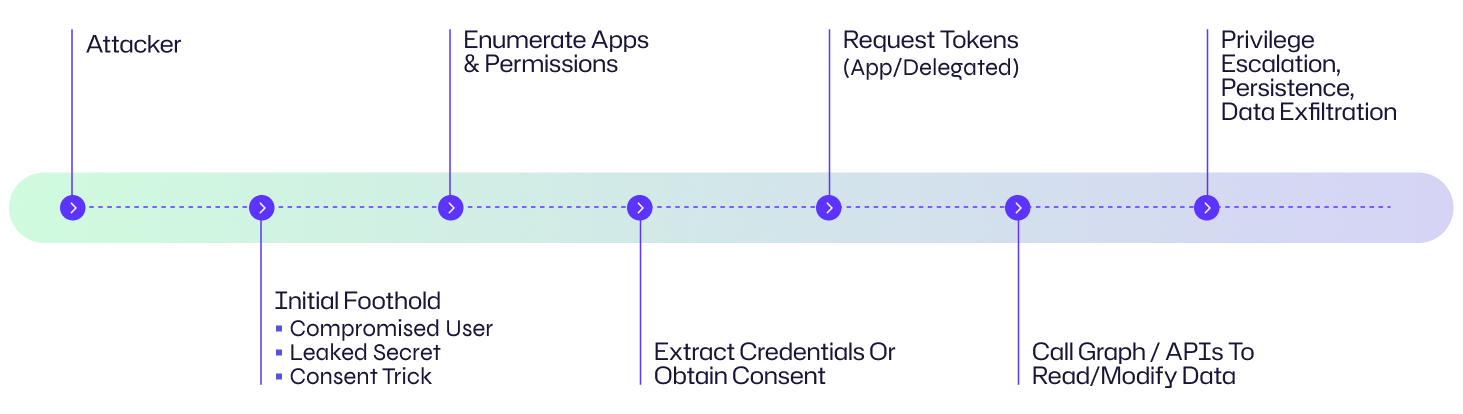
Example: Organization Perspective
Here is how this looks from an organization’s perspective: An attacker phishes an admin at Contoso Corp to consent to an app that appears to be a legitimate analytics tool. Once the app is admin-consented, the attacker exchanges the app credentials for application tokens and uses Microsoft Graph to enumerate mailboxes and download sensitive documents from OneDrive. They then register a secondary service principal with a long-lived certificate to retain access, enabling prolonged exfiltration and tenant modification.
Examples of Application Permission Abuse
Case | Impact |
|---|---|
|
OAuth Consent Phishing Campaigns |
Attackers have used consent phishing to gain tenant-wide application permissions, enabling mass mailbox access and data theft across multiple organizations. |
|
Leaked Client Secrets in Public Repos |
Several incidents show attackers discovering app secrets in public Git repositories or deployment artifacts, using them to mint tokens and access resources without ever touching user passwords. |
Consequences of Application Permission Abuse
Abuse of Entra ID application permissions can produce severe consequences: tenant compromise, mass data exfiltration, unauthorized creation of accounts and service principals, lateral movement into on-prem resources, and long-lived persistence that’s hard to detect.
Financial Consequences
Attackers can exfiltrate intellectual property, customer PII, or financial data leading to fraud, regulatory fines, ransom demands, or remediation costs (forensics, legal, notification). Cloud resource abuse (e.g., cryptomining) can also lead to unexpected bills.
Operational Disruption
Tampering with directory objects, group memberships, or identity synchronization can disrupt authentication flows, cause outages in critical apps, or force emergency rotations and reconfiguration of integrations.
Reputational Damage
Tenant compromises or data leaks tied to abused app permissions can erode customer trust, attract negative press, and damage partner relationships.
Legal and Regulatory Impact
Unauthorized exposure of regulated data (PHI, financial records) can trigger GDPR, HIPAA, or other compliance investigations, fines, and potential litigation.
Impact Area | Description |
|---|---|
|
Financial |
Data theft, fraud, cloud bill abuse |
|
Operational |
Broken auth flows, service outages |
|
Reputational |
Loss of customer confidence, brand harm |
|
Legal |
Regulatory penalties, lawsuits |
Common Targets of Application Permission Abuse: Who is at risk?
Over-Privileged Enterprise Applications
Apps granted Directory.* or tenant-wide Application permissions are high-value targets because they enable bulk operations across identities and resources.
Multi-Tenant or Customer-Facing Integrations
Third-party SaaS apps or multi-tenant apps that request broad scopes can be abused if an admin consents or if the app itself is malicious.
Leaky DevOps/CI Pipelines
Client secrets or certs accidentally committed to source control, stored in insecure storage, or accessible from CI logs make confidential clients vulnerable.
Legacy OAuth Configurations & Conditional Access Gaps
Apps using legacy auth flows, or tenants without strict Conditional Access policies (e.g., no MFA on consent, no admin consent workflows), are easier to exploit.
Stale or Unmonitored Service Principals
Old or orphaned app registrations with still-valid credentials are persistent attack vectors that attackers can crack at their leisure.
Risk Assessment
Risk Factor | Level |
|---|---|
|
Potential Damage |
Very High — tenant-wide compromise and mass data access possible. |
|
Ease of Execution |
Medium — requires reconnaissance plus either social engineering or discovery of credentials, but techniques and tooling are widely known. |
|
Likelihood |
Medium to High — many tenants still have consent workflows, leaked secrets, or permissive app registrations. |
How to Prevent Application Permission Abuse
Prevention is multi-layered: reduce blast radius, harden app auth, and minimize human consent errors.
App & Consent Hygiene
- Enforce least-privilege scopes: Only request the minimal Microsoft Graph scopes needed; prefer delegated over application permissions where possible.
- Use admin consent workflows: Require justifications and multi-approver admin consent for high-privilege apps.
- Restrict who can register or consent to apps: Limit app registration and admin consent to a small, vetted group.
- Review and remove unused apps: Regularly audit service principals and app registrations to delete orphaned or unnecessary ones.
Protect Credentials and Secrets
- Prefer certificate-based (asymmetric) authentication for confidential clients instead of client secrets. Certificates are less likely to be exposed and can be rotated safely.
- Store secrets in managed vaults (Azure Key Vault) with strict RBAC and managed identity access — never in source code or plaintext configs.
- Automate rotation of client secrets and certificates and enforce short lifetimes where operationally possible.
Conditional Access & Session Controls
- Require Conditional Access for app token issuance: Block risky sign-ins, require compliant devices, and enforce MFA for delegated flows where applicable.
- Use continuous access evaluation to revoke tokens when risky signals appear.
Application Design & Monitoring
- Design apps for least privilege and transparency: Implement consent-only features and granular scopes; document why each permission is needed.
- Log and monitor Graph API usage: Alert on unusual patterns (large mailbox downloads, mass user enumeration, creation of new apps/service principles).
- Restrict which apps can use application permissions via entitlement management and policy.
How Netwrix Can Help
Netwrix Identity Threat Detection & Response (ITDR) strengthens your defense against Entra ID application permission abuse by continuously monitoring for risky app registrations, abnormal consent grants, and suspicious Graph API activity. By detecting unauthorized privilege escalations early and automating response actions like alerting or revoking compromised permissions, Netwrix ITDR helps you minimize dwell time and reduce the blast radius of identity-driven attacks. With comprehensive visibility across hybrid Active Directory and Entra ID, organizations can enforce least privilege, secure high-risk service principals, and quickly investigate indicators of compromise - ensuring data security that starts with identity.
Detection, Mitigation and Response Strategies
Detection
- Monitor unusual Graph API patterns: spikes in Applications.ReadWrite.All, Users.ReadAll, or large file downloads.
- Alert on new app registrations and new credentials: notify when a service principal is created, credentials are added, or consent is granted.
- Track admin consent events and who approved them: flag unexpected admin consent from unusual locations or times.
- Detect anomalous token issuance: tokens requested by unknown clients or using old credentials should be investigated.
- Use deception: create decoy apps or service principals and watch for any access to them.
Response
- Revoke compromised credentials immediately: rotate client secrets, revoke certificates, and remove leaked credentials from all locations.
- Remove malicious app consent and disable offending service principals: remove permissions and disable the app to block further API access.
- Force token invalidation: invalidate issued refresh tokens and access tokens where possible and require reauthentication.
- Conduct a tenant-wide audit: review roles, group memberships, delegated permissions, and provisioning connectors for secondary impacts.
- Hunt for lateral artifacts: check for created accounts, role assignments, abnormal app registrations, or modified conditional access policies.
Mitigation
- Adopt Zero Trust for identity: continuously verify every request and limit what any app or identity can do.
- Use least-privilege automation: only allow automation and apps to access necessary resources and isolate high-risk tasks in dedicated, auditable service principles.
- Implement strong supply-chain controls: scan repos, CI pipelines, and deployment artifacts for leaked secrets and integrate secret scanning into PR checks.
Industry-Specific Impact
Industry | Impact |
|---|---|
|
Healthcare |
Compromise may expose PHI from cloud EMR systems or patient communications (email/OneDrive), violating HIPAA. |
|
Finance |
Attackers can access transaction data, customer PII, or payment systems integrated via OAuth, causing regulatory and financial fallout. |
|
Retail |
Exposure of customer data, loyalty program credentials, or supply-chain integrations can lead to fraud and compliance violations. |
Attack Evolution & Future Trends
- Consent phishing is maturing: social engineering combined with polished app pages increases admin consent success.
- Automation of app reconnaissance: tooling now scans tenants for high-risk apps, leaked creds, and devops secrets at scale.
- Long-lived non-interactive credentials remain attractive — certificate protection and rotation are becoming standard defenses.
- Cloud-to-on-prem identity bridges: attackers increasingly combine Entra ID abuse with hybrid sync connectors to extend reach into on-prem AD.
- AI-assisted reconnaissance: automated systems analyze tenant metadata to find the smallest path to high-impact permissions.
Key Statistics & Infographics
(Imagined metrics for emphasis — replace with your telemetry where available.)
• Large percentage of incidents involve leaked or mismanaged secrets in CI/CD.
• Consent phishing campaigns accounted for a notable portion of cloud compromises in recent years.
• Many organizations lack regular audits of app permissions and service principals.
Final Thoughts
Abusing Entra ID application permissions is powerful because it uses legitimate platform capabilities, making malicious activity blend with normal automation. The defense posture should combine preventive controls (least privilege, secret protection, consent governance), detection (Graph monitoring, alerts on app lifecycle events), and rapid response (credential revocation, consent removal). A programmatic, continuous approach to auditing app permissions paired with strict operational controls over who can consent or register apps will reduce the attack surface dramatically.
FAQs
Share on
View related cybersecurity attacks
Kerberoasting Attack – How It Works and Defense Strategies
AdminSDHolder Modification – How It Works and Defense Strategies
AS-REP Roasting Attack - How It Works and Defense Strategies
Hafnium Attack - How It Works and Defense Strategies
DCSync Attacks Explained: Threat to Active Directory Security
Golden SAML Attack
Silver Ticket Attack
Group Managed Service Accounts Attack
DCShadow Attack – How It Works, Real-World Examples & Defense Strategies
ChatGPT Prompt Injection: Understanding Risks, Examples & Prevention
NTDS.dit Password Extraction Attack
Pass the Hash Attack
Pass-the-Ticket Attack Explained: Risks, Examples & Defense Strategies
Password Spraying Attack
Plaintext Password Extraction Attack
4 Service Account Attacks and How to Protect Against Them
How to Prevent Malware Attacks from Impacting Your Business
What is Credential Stuffing?
Compromising SQL Server with PowerUpSQL
What Are Mousejacking Attacks, and How to Defend Against Them
Stealing Credentials with a Security Support Provider (SSP)
Rainbow Table Attacks: How They Work and How to Defend Against Them
A Comprehensive Look into Password Attacks and How to Stop Them
LDAP Reconnaissance
Bypassing MFA with the Pass-the-Cookie Attack
Understanding Golden Ticket Attacks
