Netwrix Auditor: Lo strumento di auditing per Active Directory
Semplifica l'audit di Active Directory con Netwrix. Rileva e risolvi i permessi rischiosi, i modelli di comportamento sospetti degli utenti e le modifiche alle policy.
Scopri come li abbiamo aiutati
Affidabile da





































































Uno strumento di auditing per Active Directory che scava più a fondo
Rileva minacce interne
Ottieni visibilità su tutti i cambiamenti di sicurezza e configurazione in AD e Group Policy, come l'escalation dei privilegi o attività anomale dell'amministratore.
Mitigare i rischi di AD
Valuta e risolvi le lacune di sicurezza legate all'assegnazione e gestione impropria dei privilegi degli account prima che possano essere sfruttate dagli attaccanti.
Superare le verifiche con facilità
Il nostro software di audit AD genera report preconfezionati e personalizzati per PCI DSS, HIPAA, SOX, GDPR e altri standard senza alcuna formattazione manuale necessaria.
Aumenta la produttività del team IT
Minimizza i tempi di inattività del servizio consentendo agli amministratori di scoprire rapidamente le cause principali dei problemi e di annullare le modifiche indesiderate.
Capacità
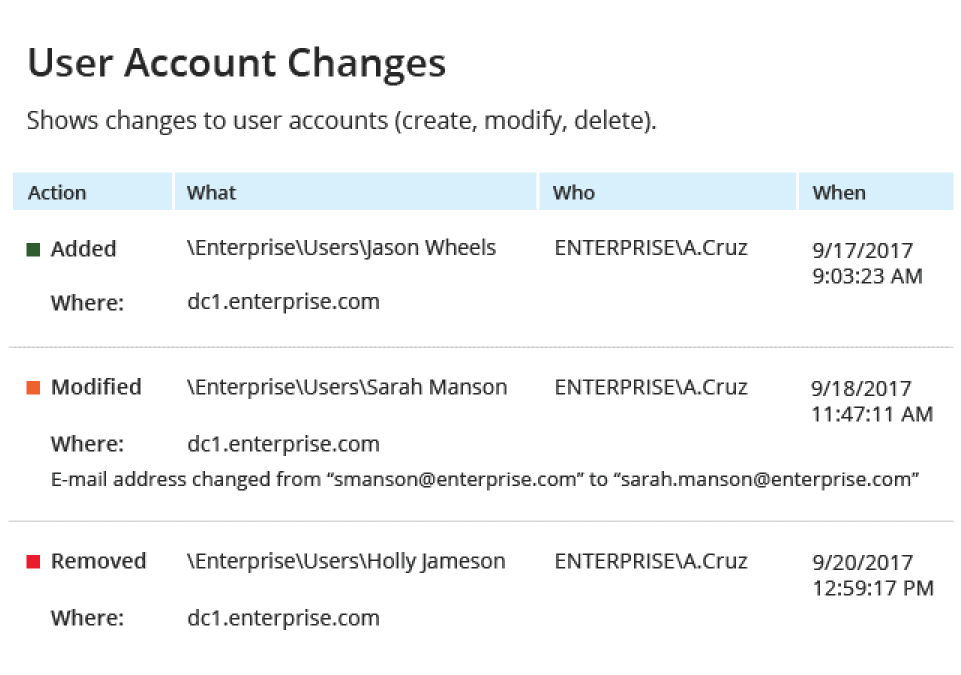
Proteggi il tuo Active Directory e le Group Policies con un monitoraggio AD unificato
Pronto per iniziare?
Soluzioni
Vai oltre la protezione da una singola minaccia. Assicura ogni aspetto con le soluzioni Netwrix.
Integrazioni
Integrazioni senza soluzione di continuità per una sicurezza più intelligente
Vedi tutte le integrazioni





