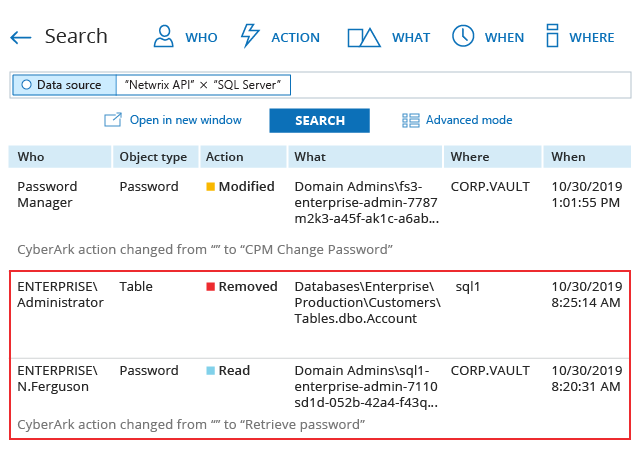
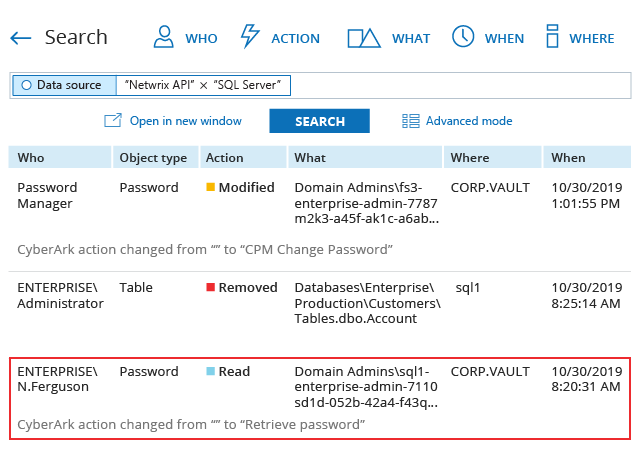
See the full list of Netwrix Auditor advantages and learn how you can
detect threats faster, prove compliance with less effort and enable your IT team to do more with less.
IGA vs Shadow IT : Comment reprendre le contrôle de vos accès en 2025 ?
29 April, 4am EDT
Register Now