Netwrix Change Tracker: Software de Gerenciamento de Configuração de Segurança
Software de gerenciamento de configuração de segurança e integridade de arquivos que reforça sistemas, compara configurações e comprova conformidade.
Leia suas histórias
Confiado por





































































Erradique mudanças não autorizadas e fortaleça sua infraestrutura
Fortaleça sistemas críticos
Reforce as configurações de segurança em toda a sua infraestrutura com a nossa ferramenta de gerenciamento de configuração de segurança.
Detecção instantânea de alterações
Monitore alterações não autorizadas em tempo real com varredura avançada de integridade de arquivos e alertas instantâneos para resposta rápida.
Validação de mudanças em tempo real
As integrações de ITSM oferecem controle de mudança inteligente em circuito fechado e reduzem o ruído das mudanças que foram planejadas.
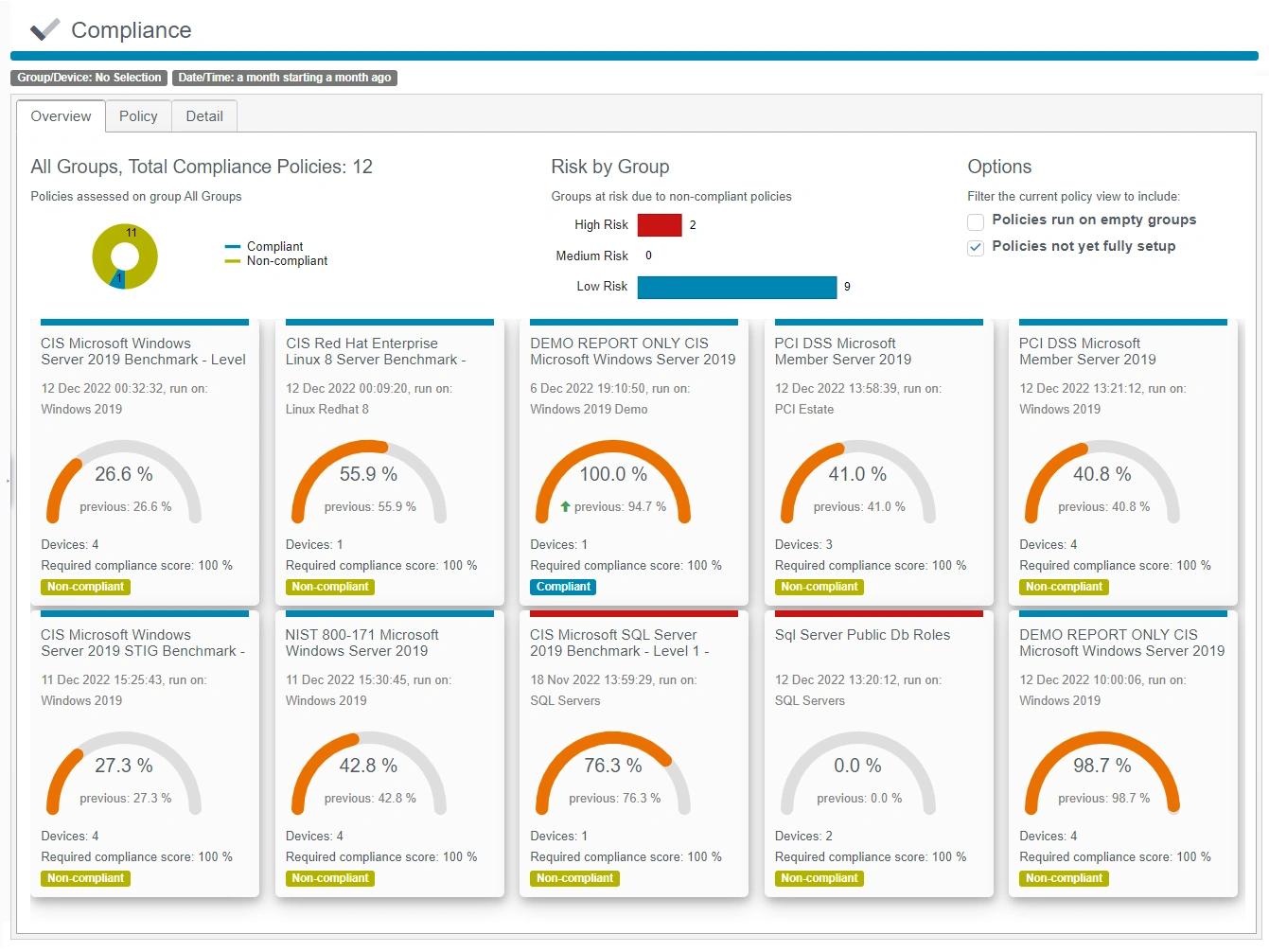
Atenda aos requisitos de conformidade
Passe em auditorias regulatórias facilmente com ferramentas completas de gerenciamento de configuração de segurança e relatórios automatizados.
Capacidades
Monitore, detecte e responda a alterações em toda a sua infraestrutura de TI com ferramentas completas de gerenciamento de configuração de segurança
Pronto para começar?
Soluções
Vá além da proteção contra uma única ameaça. Proteja todos os ângulos com as soluções da Netwrix.
Confiado por profissionais
Não aceite apenas a nossa palavra






