Ataque de Kerberoasting – Como Funciona e Estratégias de Defesa
Kerberoasting é um ataque sofisticado de credenciais que explora vulnerabilidades na autenticação Kerberos dentro de ambientes Active Directory (AD). O objetivo principal é o roubo de credenciais e escalonamento de privilégios, levando a escalonamento de privilégios dentro de uma rede.
Atributo | Detalhes |
|---|---|
|
Tipo de Ataque |
Kerberoasting |
|
Nível de Impacto |
Alto |
|
Target |
Empresas, Governos |
|
Vetor de Ataque Primário |
Acesso Interno à Rede (via usuário de domínio comprometido) |
|
Motivação |
Roubo de Credenciais, Escalada de Privilégios, Espionagem |
|
Métodos Comuns de Prevenção |
Senhas Fortes, Criptografia AES, gMSAs, MFA, Auditoria de Tickets |
Fator de Risco | Nível |
|---|---|
|
Dano Potencial |
Muito Alto |
|
Facilidade de Execução |
Médio |
|
Probabilidade |
Médio a Alto |
O que é Kerberoasting?
Kerberoasting é um ataque baseado em credenciais no qual um adversário utiliza credenciais de domínio válidas para solicitar tickets de serviço Kerberos associados a Nomes de Entidade de Serviço (SPNs) do Active Directory. O atacante extrai então os hashes de senha criptografados desses tickets e os decifra offline, visando tipicamente senhas fracas ou facilmente previsíveis. O objetivo principal deste ataque é obter privilégios elevados dentro do AD, facilitando movimento lateral, persistência ou roubo de dados.
Como funciona o Kerberoasting?
Kerberoasting explora fraquezas inerentes no processo de autenticação Kerberos do Active Directory. Abaixo está uma análise detalhada de cada etapa envolvida na realização de um ataque de Kerberoasting.
1. Comprometer uma conta de usuário de domínio padrão
Os atacantes primeiro precisam de acesso a credenciais de usuário de domínio válidas, normalmente obtidas por meio de phishing, preenchimento de credenciais, exploração de vulnerabilidades ou pontos de apoio iniciais em endpoints comprometidos. Mesmo contas de usuário com baixos privilégios são suficientes para iniciar o ataque.
2. Enumere contas de serviço com SPNs
Uma vez dentro do domínio, os atacantes enumeram os Nomes de Principais de Serviço (SPNs) registrados em contas de serviço. A enumeração pode ser realizada usando ferramentas como scripts PowerShell, consultas LDAP ou ferramentas especializadas de enumeração como BloodHound. Contas de serviço com SPNs frequentemente possuem privilégios mais altos, tornando-as alvos ideais.
3. Solicitar tickets TGS do Kerberos
Com SPNs identificados, os atacantes usam suas credenciais de domínio válidas para primeiro obter um Ticket Granting Ticket (TGT) do Key Distribution Center (KDC). Esse TGT é então usado para solicitar legitimamente tickets do Kerberos Ticket Granting Service (TGS) para as contas de serviço alvo. Esses tickets TGS são criptografados com o hash da senha da conta de serviço e podem ser extraídos para quebra offline. Ferramentas como o GetUserSPNs do Impacket, ou scripts baseados em PowerShell, automatizam esse processo e são comumente usados em ataques de Kerberoasting.
4. Exportar ingressos
Os atacantes então exportam ou extraem esses tickets de serviço da memória ou armazenamento no sistema comprometido. Ferramentas de hacking populares como Rubeus e Mimikatz simplificam a extração e exportação desses tickets para um formato adequado para quebra offline.
5. Quebrar tickets offline
Os bilhetes TGS exportados contêm hashes criptografados de senhas de contas de serviço. Os atacantes tentam quebrar esses hashes offline usando ferramentas de quebra de senha como Hashcat, John the Ripper ou tabelas arco-íris pré-geradas. Senhas fracas podem ser rapidamente comprometidas, expondo credenciais em texto claro.
6. Use credenciais recuperadas para escalar privilégios
Uma vez que os atacantes conseguem quebrar os hashes e recuperar as credenciais em texto simples, eles podem usar essas credenciais para fazer login como contas de serviço privilegiadas. Isso concede privilégios elevados, possibilitando o movimento lateral pela rede, acesso a informações sensíveis e potencial persistência de longo prazo dentro do ambiente AD.
✱ Variante: Kerberoasting sem pré-autenticação
Contas de usuário com pré-autenticação desativada podem ser exploradas sem credenciais válidas
Em algumas configurações do Active Directory, a pré-autenticação pode estar desativada nas contas de usuário, o que significa que os atacantes não precisam de credenciais válidas para solicitar tickets Kerberos. Isso permite que os atacantes obtenham hashes criptografados sem primeiro comprometer uma conta de domínio existente.
Ferramentas como Rubeus permitem essa evasão sob certas configurações incorretas do AD
Os atacantes utilizam ferramentas como Rubeus, projetadas especificamente para explorar essa má configuração, solicitando diretamente tickets TGS sem autenticação prévia. Esta variante torna ainda mais fácil para os atacantes obterem acesso.
Diagrama de Fluxo de Ataque
O diagrama a seguir ilustra as etapas sequenciais de um ataque de Kerberoasting, começando com um invasor comprometendo uma conta de usuário de domínio e culminando na escalada de privilégios dentro do ambiente do Active Directory.
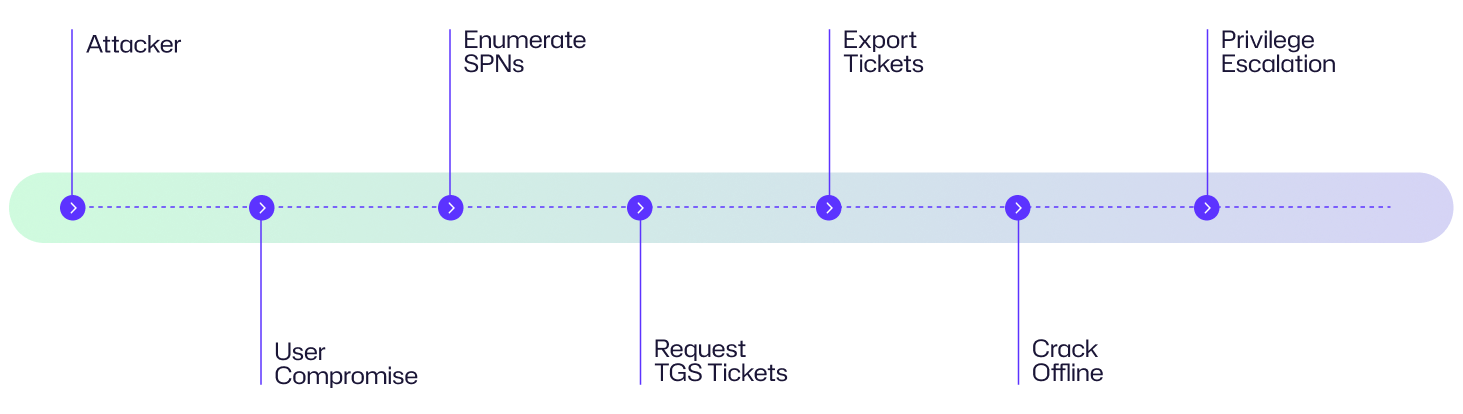
Aqui está a explicação do Kerberoasting do ponto de vista de uma organização.
Um atacante obtém acesso à rede da XYZ Corp comprometendo um usuário de domínio através de phishing. Uma vez dentro, eles enumeram contas de serviço com SPNs e solicitam tickets TGS do Kerberos. Utilizando ferramentas como Rubeus, eles exportam os tickets e quebram a senha fraca de uma conta de serviço offline. Com as credenciais obtidas, eles elevam seus privilégios, acessam dados sensíveis e se movimentam lateralmente, destacando os riscos de uma higiene de senhas deficiente e monitoramento inadequado em ambientes de AD.
Exemplos de Kerberoasting
A seguir são exemplos reais de grupos avançados de ameaças que utilizaram eficazmente o Kerberoasting como parte de suas cadeias de ataque.
Case | Impacto |
|---|---|
|
Akira Ransomware Group |
O Grupo Akira Ransomware comumente utiliza Kerberoasting para escalar privilégios e manter persistência em ambientes AD. Ao solicitar e extrair hashes de tickets de serviço para contas de serviço, eles quebram esses offline para recuperar credenciais, muitas vezes ganhando acesso a contas de alto privilégio. Essa tática permite que eles se movam lateralmente e aprofundem sua presença dentro da rede alvo. |
|
FIN7 |
FIN7, um grupo de ameaças motivado financeiramente, foi observado utilizando a técnica de quebra de TGS offline como parte de sua estratégia de coleta de credenciais. Esta técnica envolve a exploração do método de ataque Kerberoasting, visando especificamente contas de serviço em ambientes AD. Este método está alinhado com as táticas mais amplas da FIN7 de aproveitar ferramentas legítimas do sistema (como PowerShell, WMI e funções nativas do AD) para permanecer furtivo enquanto expande o acesso para roubo de dados ou implantação de ransomware. |
Consequências do Kerberoasting
Um ataque Kerberoast pode ter consequências graves e abrangentes para as organizações. Uma vez que os atacantes obtenham e descriptografem as credenciais de contas de serviço, eles podem elevar privilégios e mover-se lateralmente pela rede. Isso não só possibilita o roubo de dados e a interrupção do sistema, mas também expõe a organização a perdas financeiras, danos à reputação, penalidades legais e fiscalização regulatória.
Consequências Financeiras
Ataques de Kerberoasting bem-sucedidos podem dar aos atacantes acesso a contas privilegiadas, possibilitando o roubo de dados, fraude financeira ou implantação de ransomware. Isso frequentemente leva a perdas financeiras diretas, especialmente se os atacantes roubarem ou criptografarem dados críticos para o negócio. As organizações podem ser forçadas a pagar milhões em demandas de resgate para restaurar o acesso. Além disso, violações que envolvem o roubo de credenciais frequentemente acionam multas regulatórias, particularmente em indústrias reguladas como finanças e saúde.
Perturbação Operacional
Com acesso a credenciais privilegiadas, atores de ameaças podem desativar sistemas críticos, interromper serviços internos e interferir nas operações de TI. Isso pode resultar em uma paralisação generalizada, interrompendo funções empresariais como comunicação, processamento de dados ou atendimento ao cliente. O esforço de recuperação pode ser extenso e custoso, muitas vezes exigindo redefinições manuais, reconstruções de domínios comprometidos ou remediação completa do AD, o que prejudica significativamente a produtividade.
Dano à reputação
Um vazamento divulgado envolvendo Kerberoasting e comprometimento do AD envia uma mensagem clara de que a infraestrutura de identidade da organização estava vulnerável. A cobertura da imprensa, divulgações regulatórias ou dados vazados podem levar à perda de confiança do cliente, impactar a confiança dos investidores e prejudicar relacionamentos com parceiros ou fornecedores. Reconstruir essa confiança pode exigir esforços dispendiosos de relações públicas, alcance ao cliente ou oferecimento de serviços de proteção de identidade.
Impacto Legal e Regulatório
Ataques de Kerberoasting que levam à exposição de informações pessoais ou sensíveis podem colocar a organização em violação de regulamentos de proteção de dados como GDPR, HIPAA ou SOX. Órgãos reguladores podem impor multas pesadas, e indivíduos ou entidades afetadas podem buscar ação legal. Além disso, organizações podem estar sujeitas a investigações ou auditorias. Em setores regulados, incidentes repetidos podem até levar à revogação de licenças ou sanções.
Área de Impacto | Descrição |
|---|---|
|
Financeiro |
Roubo de credenciais, exfiltração de dados, ransomware |
|
Operacional |
Interrupções de rede, serviços paralisados |
|
Reputacional |
Erosão da confiança pública, rotatividade de clientes |
|
Jurídico |
Penalidades de conformidade, processos judiciais por violações de dados |
Alvos comuns de um Kerberoasting: Quem está em risco?
Contas de serviço com SPNs
Os SPNs permitem que o Kerberos associe uma instância de serviço a uma conta de logon, tornando essas contas recuperáveis por meio de solicitações de TGS. Contas de serviço criadas manualmente, especialmente aquelas com senhas fracas ou que não são rotacionadas, são alvos principais. Os atacantes podem solicitar ingressos TGS para essas contas e tentar quebrar as senhas offline.
Exemplos comuns incluem contas vinculadas ao SQL Server, IIS, SharePoint, Exchange e soluções de backup. Essas contas frequentemente executam serviços críticos e podem ter privilégios elevados, tornando-as especialmente valiosas.
Contas de Alto Privilégio
Contas com funções administrativas — como Domain Admins, Enterprise Admins ou Schema Admins — são alvos principais. Uma vez comprometidas, elas fornecem acesso irrestrito em todo o domínio. Essas contas também podem estar vinculadas a serviços legados ou tarefas agendadas, aumentando sua exposição.
Contas Utilizando Criptografia RC4
Contas configuradas para usar RC4_HMAC_MD5 são muito mais vulneráveis ao Kerberoasting. Este algoritmo de criptografia é mais rápido de ser quebrado em comparação com alternativas baseadas em AES. Infelizmente, muitos sistemas legados ainda usam RC4 por padrão ou exigem RC4 para compatibilidade, deixando essas contas expostas a ataques de força bruta offline ou ataques de dicionário.
Contas Obsoletas ou Não Monitoradas
Contas mais antigas que não estão mais em uso ativo ou aquelas marcadas com 'senha nunca expira' representam um risco persistente. Essas contas podem passar despercebidas, especialmente em ambientes grandes com má gestão do ciclo de vida da conta. Como os atacantes podem quebrar as credenciais no seu próprio ritmo offline, até mesmo uma conta inativa, mas ainda válida, pode se tornar um ponto de entrada para movimento lateral ou escalada de privilégios.
Avaliação de Risco
Compreender o risco representado pelo Kerberoasting é essencial para avaliar a postura de segurança geral de um ambiente AD.
Fator de Risco | Nível |
|---|---|
|
Dano |
Muito Alto
|
|
Facilidade de Execução |
Médio
|
|
Probabilidade |
Médio a Alto
|
Como prevenir Kerberoasting
Prevenir o Kerberoasting requer uma combinação de políticas de senha fortes, configurações de conta seguras e configurações de criptografia adequadas. O monitoramento proativo e os controles automatizados de conta fortalecem ainda mais as defesas contra esse vetor de ataque comum.
Higiene de Senhas & Contas
Uma vez que um ataque de Kerberoasting depende da quebra de senha offline, aumentar a complexidade da senha e limitar a idade da senha reduz diretamente a taxa de sucesso do atacante.
- Utilize Senhas Longas e ComplexasContas de serviço, especialmente aquelas com SPNs, devem usar senhas com pelo menos 25 caracteres, incluindo uma mistura de letras maiúsculas, minúsculas, números e caracteres especiais. O comprimento e a aleatoriedade reduzem significativamente a velocidade das tentativas de quebra por força bruta.
- Rotacione Senhas RegularmenteAs senhas das contas de serviço devem ser rotacionadas pelo menos anualmente, ou mais frequentemente em ambientes de alto risco. Isso limita o período de oportunidade para um atacante descobrir uma senha offline.
- Audite e aplique políticas de expiraçãoAudite regularmente a idade das senhas em todas as contas de serviço. Evite configurações com a opção “senha nunca expira”, o que torna as contas alvos persistentes. Aplique políticas de expiração rigorosas através de Group Policy ou ferramentas de identidade dedicadas.
- Use gMSAs ou dMSAsSubstitua contas de serviço gerenciadas manualmente por Group Managed Service Accounts (gMSAs) ou Distributed Managed Service Accounts (dMSAs). Essas contas gerenciam automaticamente as mudanças de senha, suportam credenciais complexas e reduzem o erro humano — diminuindo significativamente a exposição ao Kerberoasting.
Configuração de Criptografia
Configurar uma criptografia forte para autenticação Kerberos é crítico para mitigar os riscos de Kerberoasting, já que algoritmos de criptografia mais fracos como RC4 são muito mais fáceis de quebrar.
- Impor a criptografia AES de 128/256 bitsConfigure sistemas AD e associados a domínios para usar AES128_HMAC ou AES256_HMAC para criptografia de tickets Kerberos. Esses algoritmos são significativamente mais resistentes a ataques de força bruta do que RC4 e são suportados em ambientes Windows modernos.
- Desativar Manualmente o RC4Embora a Microsoft tenha descontinuado o RC4_HMAC_MD5, ele ainda pode estar habilitado para compatibilidade, especialmente em ambientes legados. Revise a Política de Grupo e as configurações de nível de conta para desativar explicitamente o RC4 onde for possível. Isso ajuda a garantir que os atacantes não possam solicitar tickets criptografados com cifras fracas.
- Atualize as senhas após mudanças na políticaAs configurações de criptografia vinculadas aos tickets Kerberos só têm efeito após a alteração da senha de uma conta. Portanto, após impor novas políticas de criptografia, é essencial redefinir as senhas das contas de serviço existentes.
Definição de Escopo de Conta
Limitar a exposição e as capacidades das contas de serviço é uma maneira proativa de reduzir a superfície de ataque disponível para Kerberoasting.
- Remova SPNs de Contas de UsuárioEvite atribuir Nomes de Principal de Serviço (SPNs) a contas de usuário padrão, pois isso as torna elegíveis para Kerberoasting. Em vez disso, use contas de serviço dedicadas ou Contas de Serviço Gerenciadas (gMSAs/dMSAs) para isolar as funções de serviço da identidade do usuário.
- Restringir a Logons Não InterativosConfigure contas de serviço para não permitir logons interativos usando Política de Grupo ou configurações de AD. Isso impede que atacantes usem credenciais comprometidas para login direto, limitando o movimento lateral após uma tentativa bem-sucedida de Kerberoasting.
- Limitar o Escopo de Acesso por Host e ServiçoRestrinja as permissões das contas de serviço especificamente para os hosts e serviços que elas suportam. Evite conceder privilégios desnecessários em todo o domínio. Aplicar o princípio do menor privilégio garante que, mesmo que uma conta de serviço seja comprometida, o impacto seja contido.
Privileged Access Management (PAM)
A implementação do Privileged Access Management (PAM) é um controle crítico para reduzir o risco e o impacto do Kerberoasting, assegurando como as contas privilegiadas são utilizadas, armazenadas e monitoradas.
- Armazene e Rotacione Credenciais PrivilegiadasUtilize uma solução de Privileged Access Management (PAM) para armazenar credenciais de contas de serviço e administrativas, eliminando senhas codificadas e gerenciamento manual. Essas ferramentas podem rotacionar automaticamente as senhas conforme um cronograma definido ou após cada uso.
- Monitore o Uso de Contas com Gravação de Sessão e Análise ComportamentalPlataformas de Privileged Access Management (PAM) oferecem monitoramento e gravação de sessão, permitindo que equipes de segurança auditem atividades privilegiadas em tempo real ou retrospectivamente. Análises comportamentais podem detectar anomalias como padrões de acesso incomuns, movimento lateral ou uso fora do horário comercial, que podem indicar atividades relacionadas a Kerberoasting.
Suporte Netwrix
A Netwrix oferece um forte suporte para defender contra ataques de Kerberoasting por meio de suas ferramentas de proteção do Active Directory e de identidade. Aqui estão os dois principais produtos da Netwrix que ajudam a prevenir ou detectar Kerberoasting.
Netwrix Access Analyzer
Esta ferramenta realiza varreduras ativas no AD para identificar contas de serviço vulneráveis ao Kerberoasting, especialmente aquelas com SPNs e configurações de criptografia fracas como RC4 ou DES. Um trabalho dedicado AD_KerberoastingRisk produz um painel de riscos claro com limites personalizáveis (por exemplo, sinalizando AES 128, senhas expiradas ou marcações de "senha nunca expira"), e destaca contas que precisam de remediação. Ao identificar contas de alto risco antes de um ataque ocorrer, as equipes de segurança podem proativamente reforçar as configurações das contas, atualizar senhas e desativar SPNs problemáticos.
Run Netwrix Access Analyzer for free and get a clear view of privilege exposure instantly.
Netwrix Threat Prevention
Netwrix Threat Prevention oferece monitoramento em tempo real e aplicação na fonte, em vez de depender apenas de logs do Windows. Pode detectar atividades suspeitas do Kerberos, como solicitações anormais de TGS ou atribuições de SPN a contas privilegiadas, e bloquear automaticamente tais ações ou emitir alertas em tempo real. Com políticas que impedem alterações de alto risco e alertas contextuais, ele interrompe tentativas de Kerberoasting em seu caminho e escala alertas para investigações adicionais.
Experimente Netwrix Threat Prevention e receba alertas imediatos sobre atividades arriscadas antes que elas impactem o seu negócio.
Estratégias de Detecção, Mitigação e Resposta
Ataques de Kerberoasting muitas vezes passam despercebidos até que danos significativos sejam causados. Uma defesa robusta requer mecanismos de detecção eficazes, protocolos de resposta rápida e estratégias de mitigação a longo prazo.
Detecção
Aqui estão algumas ótimas dicas para detectar Kerberoasting no início da cadeia de ataque.
- Monitore os IDs de Evento 4769 e 4770 para solicitações TGSO ID de Evento 4769 (solicitação TGS) e 4770 (renovação de ticket TGS) são indicadores chave da atividade Kerberos. Um aumento nos eventos 4769, especialmente de um único usuário consultando vários SPNs, pode indicar Kerberoasting.
- Sinalizar o Uso de Criptografia RC4 (Tipo 0x17)Os tickets Kerberos criptografados usando RC4_HMAC_MD5 (tipo 0x17) são muito mais fáceis de quebrar. Monitorar esse tipo de criptografia pode ajudar a identificar contas de alto risco ou tentativas ativas de explorar a criptografia fraca de tickets.
- Detectar Volumes ou Padrões Anormais de TGSVolumes incomuns de solicitações de TGS — especialmente visando várias contas de serviço em um curto período — podem indicar colheita de tickets. Monitorar tais anomalias é crítico para a detecção de Kerberoasting.
- Utilize Honeypots/Honeytokens para atrair atacantesImplante contas de serviço isca com SPNs e monitore tentativas de acesso. Qualquer interação com essas contas é um forte indicador de reconhecimento malicioso ou Kerberoasting.
- Configure UBA e SIEM para Análise de Linha de BaseUtilize plataformas de User Behavior Analytics (UBA) e SIEM para estabelecer um comportamento normal de solicitações Kerberos. Sinalize desvios dessa linha de base, como novos usuários solicitando tickets TGS ou atividades fora do horário comercial.
Resposta
A seguir estão algumas estratégias eficazes de resposta ao detectar Kerberoasting.
- Desative e redefina as contas afetadas imediatamenteSe uma conta Kerberoasted for identificada, desative-a e force uma redefinição de senha para evitar o acesso não autorizado contínuo.
- Revisar logs de AD para Movimento LateralExamine os logs em busca de sinais de uso indevido de contas, escalonamento de privilégios ou acesso a sistemas sensíveis. Concentre-se em eventos de login, alterações de membros de grupos e padrões de acesso a serviços.
- Invalidar Tickets Existentes e Forçar LogoutForce todos os usuários a se reautenticarem invalidando tickets Kerberos usando klist purge ou reiniciando serviços, garantindo que credenciais roubadas não concedam mais acesso.
Mitigação
As estratégias a seguir apoiam a mitigação eficaz do Kerberoasting.
- Implemente Princípios de Zero TrustAdote um modelo de Zero Trust onde nenhuma conta ou sistema é inerentemente confiável. Aplique o princípio do menor privilégio, validação contínua e segmentação de acesso para conter danos de ataques baseados em credenciais.
- Utilize Tecnologias de Engano (SPNs Isca)Crie SPNs falsos ou contas de serviço isca para detectar tentativas de varredura e Kerberoasting. Esses ativos de engano disparam alertas quando acessados, fornecendo um aviso prévio de comportamento malicioso.
Impacto Específico do Setor
O impacto de um ataque de Kerberoasting pode variar entre os setores, dependendo da natureza dos sistemas e dos dados em risco. Em setores como saúde, finanças e varejo, contas de serviço comprometidas podem levar a violações regulatórias, perdas financeiras e interrupção operacional.
Indústria | Impacto |
|---|---|
|
Saúde |
|
|
Finanças |
|
|
Varejo |
As redes de varejo geralmente utilizam contas de serviço para dar suporte a sistemas de ponto de venda (POS), controle de inventário e plataformas de comércio eletrônico.
|
Evolução dos Ataques & Tendências Futuras
O Kerberoasting está evoluindo com ferramentas mais robustas, automação e táticas avançadas. Enquanto a Microsoft reforça o Kerberos (por exemplo, com a descontinuação do RC4), os atacantes estão aprimorando sua capacidade de quebrar rapidamente os tickets e usá-los em cadeias de ataque complexas e de múltiplas etapas. Estar ciente dessas tendências é fundamental para uma defesa eficaz.
Desativação do RC4 no Windows 11 24H2 e Server 2025
A Microsoft está oficialmente descontinuando a criptografia RC4_HMAC_MD5 para Kerberos em lançamentos futuros como o Windows 11 24H2 e o Windows Server 2025. Essa medida reduz a exposição a ataques de força bruta offline, já que o RC4 é muito mais fácil de ser quebrado do que a criptografia baseada em AES. Embora isso represente uma grande melhoria de segurança, organizações que utilizam sistemas legados ainda podem estar em risco se não atualizarem as políticas de criptografia e rotacionarem as senhas após a atualização.
Ferramentas de quebra de GPU agora adivinham >100B senhas/seg
Ferramentas modernas de quebra de senhas baseadas em GPU (por exemplo, Hashcat, John the Ripper) agora podem ultrapassar 100 bilhões de tentativas por segundo, reduzindo drasticamente o tempo necessário para decifrar senhas fracas de contas de serviço. Combinadas com ataques de dicionário e tabelas de hash pré-calculadas, até senhas moderadamente complexas podem ser quebradas em minutos. Essa tendência torna imperativo para as organizações impor senhas muito longas e complexas, especialmente em contas com SPNs, e detectar e limitar o uso de RC4.
Uso de IA + automação em ferramentas de cracking
Os atacantes estão começando a incorporar IA e automação em fluxos de trabalho de quebra de senhas. Modelos de aprendizado de máquina podem prever padrões de senha, adaptar estratégias de cracking com base em sucessos anteriores e até identificar convenções de nomenclatura em contas empresariais. Plataformas de automação agilizam o processo de extração de tickets, análise de hashes e força bruta de credenciais, tornando os ataques mais rápidos e escaláveis. Isso aumenta a ameaça representada até mesmo por atores menos sofisticados que usam ferramentas pré-construídas.
Kerberoasting é cada vez mais utilizado em cadeias de ataque multi-estágio
Kerberoasting é agora frequentemente utilizado como parte de intrusões multi-estágio. Após decifrar uma conta de serviço, os atacantes podem:
- Crie Golden Tickets para acesso persistente ao domínio.
- Use Overpass-the-Hash para se passar por contas sem conhecer a senha.
- Lance ataques Pass-the-Ticket para se mover lateralmente entre sistemas.
Esses ataques encadeados frequentemente burlam métodos de detecção padrão e exigem correlação avançada entre eventos de autenticação.
Estatísticas Principais & Infográficos
Aqui está um gráfico de barras resumindo as principais estatísticas relacionadas a Kerberoasting e riscos de segurança de credenciais. O gráfico destaca áreas onde as organizações são mais vulneráveis, incluindo higiene de senhas, práticas de gerenciamento de contas e o rápido avanço da tecnologia de cracking.
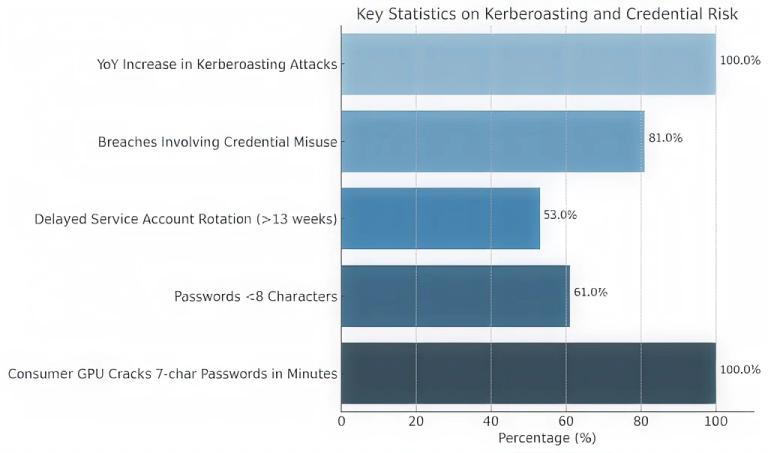
Aumento de 100% ao ano em ataques de Kerberoasting (IBM X-Force 2023)
De acordo com o IBM X-Force Threat Intelligence Report 2023, os ataques de Kerberoasting dobraram de um ano para o outro, mostrando um aumento de 100% na atividade observada em comparação com o período de relatório anterior. Esse aumento acentuado reflete a crescente popularidade do Kerberoasting entre atores de estados-nação e grupos cibernéticos devido ao seu:
- Perfil de detecção baixo (usa o protocolo Kerberos nativo).
- Não é necessário ter privilégios elevados — qualquer usuário de domínio autenticado pode iniciar o ataque.
- Grande recompensa — credenciais de conta de serviço comprometidas frequentemente levam a um comprometimento no nível do domínio.
O relatório atribui esse crescimento a uma combinação de fatores, incluindo o uso crescente de frameworks de ataque automatizados, a facilidade de execução com ferramentas publicamente disponíveis como Rubeus e Impacket, e a falta de aplicação de senhas fortes em muitos ambientes.
81% dos incidentes envolvem uso indevido de credenciais
Esta estatística, amplamente citada em relatórios do setor como o Data Breach Investigations Report (DBIR) da Verizon, destaca o papel crítico das credenciais comprometidas nos ciberataques modernos. Especificamente, 81% dos vazamentos de dados envolvem o uso indevido de nomes de usuário, senhas ou outras formas de acesso à identidade — seja por roubo, phishing, adivinhação ou quebra. Note que:
- O Kerberoasting apoia diretamente o uso indevido de credenciais.
- Uma vez que as credenciais estejam comprometidas, os atacantes podem se misturar com usuários legítimos, tornando a detecção difícil.
- Credenciais mal utilizadas frequentemente servem como ponto de entrada para ransomware, exfiltração de dados e acesso persistente.
53% das organizações atrasam a rotação de senha de contas de serviço por mais de 13 semanas
Uma pesquisa recente do setor descobriu que 53% das organizações esperam mais de 13 semanas (mais de três meses) para trocar as senhas de contas de serviço, e algumas não as trocam de forma alguma. Essas contas frequentemente possuem acesso elevado ou persistente a sistemas críticos (por exemplo, bancos de dados, backups, ERP), tornando-as alvos principais para ataques de Kerberoasting. Isso é importante porque:
- Senhas estáticas dão aos atacantes mais tempo para decifrar hashes de bilhetes de serviço offline usando ferramentas como Hashcat.
- Ciclos de vida longos de senhas frequentemente se correlacionam com as flags de “senha nunca expira”, aumentando a exposição.
- Os tipos de criptografia Kerberos estão vinculados às alterações de senha da conta. Sem uma rotação regular, algoritmos fracos como RC4 podem permanecer em uso, mesmo após atualizações de política.
Desafios Operacionais:
- As organizações frequentemente adiam a rotação de senhas devido ao medo de tempo de inatividade, falta de automação ou à indefinição sobre a responsabilidade das contas de serviço.
- O rastreamento e a atualização manuais são propensos a erros e difíceis de escalar em ambientes grandes.
Recomenda-se o uso de Group Managed Service Accounts (gMSAs) ou soluções de Privileged Access Management (PAM) para automatizar a rotação de senhas sem afetar a disponibilidade dos serviços.
61% usam senhas com menos de 8 caracteres
Apesar de anos de campanhas de conscientização sobre segurança, 61% dos usuários ou contas de serviço em ambientes corporativos ainda utilizam senhas com menos de 8 caracteres, conforme apontam auditorias internas e pesquisas do setor. Isso representa um risco significativo, especialmente no contexto do Kerberoasting.
- Senhas curtas têm menos combinações possíveis, tornando-as vulneráveis a ataques de força bruta e dicionário, principalmente quando criptografadas com RC4.
- Ferramentas modernas de quebra de senha, usando GPUs de nível doméstico, podem quebrar senhas com menos de 8 caracteres em segundos ou minutos.
- Muitas organizações não aplicam políticas de exigência de comprimento mínimo ou complexidade de senha em contas de serviço.
GPUs domésticas quebram senhas de 7 caracteres em minutos
As GPUs de consumo modernas, como as séries RTX da NVIDIA ou Radeon da AMD, tornaram a quebra de senhas offline altamente eficiente e acessível. Uma GPU de alto desempenho pode tentar bilhões de palpites de senhas por segundo, permitindo que ela faça força bruta em uma senha de 7 caracteres em apenas alguns minutos, especialmente quando a senha carece de complexidade.
Por que isso importa para o Kerberoasting:
- Quando os atacantes extraem hashes de tickets de serviço via Kerberoasting, eles podem quebrá-los offline sem alertar os defensores.
- Senhas de 7 caracteres, particularmente aquelas que usam apenas letras minúsculas ou palavras comuns, são facilmente derrotadas por ferramentas como Hashcat ou John the Ripper.
- Isso torna senhas fracas de contas de serviço um alvo de alto valor e uma vitória de baixo esforço para os invasores.
Considerações Finais
O Kerberoasting continua sendo uma das técnicas de ataque mais poderosas e furtivas direcionadas a ambientes de Active Directory — muitas vezes passando despercebida até que danos significativos ocorram.
Uma defesa eficaz exige uma abordagem holística que inclua padrões fortes de criptografia, higiene robusta de credenciais e monitoramento proativo.
Ao combinar proteção de identidade, análise comportamental avançada e táticas de engano como honeytokens e SPNs falsos, as organizações podem não apenas detectar tentativas de Kerberoasting precocemente, mas também interrompê-las antes que escalem.
Uma estratégia de defesa em camadas, guiada por inteligência, é essencial para se manter à frente dessa ameaça persistente.
FAQs
Compartilhar em
Ver ataques de cibersegurança relacionados
Abuso de Permissões de Aplicativos Entra ID – Como Funciona e Estratégias de Defesa
Modificação do AdminSDHolder – Como Funciona e Estratégias de Defesa
Ataque AS-REP Roasting - Como Funciona e Estratégias de Defesa
Ataque Hafnium - Como Funciona e Estratégias de Defesa
Ataques DCSync Explicados: Ameaça à Segurança do Active Directory
Ataque Golden SAML
Entendendo ataques Golden Ticket
Ataque a Contas de Serviço Gerenciadas por Grupo
Ataque DCShadow – Como Funciona, Exemplos Reais e Estratégias de Defesa
Injeção de Prompt do ChatGPT: Entendendo Riscos, Exemplos e Prevenção
Ataque de Extração de Senha NTDS.dit
Ataque Pass the Hash
Ataque Pass-the-Ticket Explicado: Riscos, Exemplos e Estratégias de Defesa
Ataque de Password Spraying
Ataque de Extração de Senha em Texto Simples
Vulnerabilidade Zerologon Explicada: Riscos, Explorações e Mitigação
Ataques de ransomware ao Active Directory
Desbloqueando o Active Directory com o Ataque Skeleton Key
Movimento Lateral: O que é, Como Funciona e Prevenções
Ataques Man-in-the-Middle (MITM): O que São & Como Preveni-los
Por que o PowerShell é tão popular entre os atacantes?
4 ataques a contas de serviço e como se proteger contra eles
Como Prevenir que Ataques de Malware Afetem o Seu Negócio
O que é Credential Stuffing?
Comprometendo o SQL Server com PowerUpSQL
O que são ataques de Mousejacking e como se defender contra eles
Roubando Credenciais com um Provedor de Suporte de Segurança (SSP)
Ataques de Rainbow Table: Como Funcionam e Como se Defender Contra Eles
Um Olhar Abrangente sobre Ataques de Senha e Como Impedi-los
Bypassando MFA com o ataque Pass-the-Cookie
Ataque Silver Ticket
