Data Security Software Done Right
Launch In-Browser Demo
No need to deploy the product
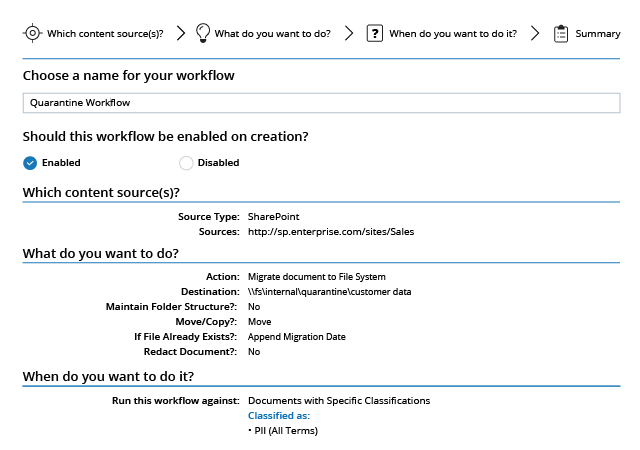
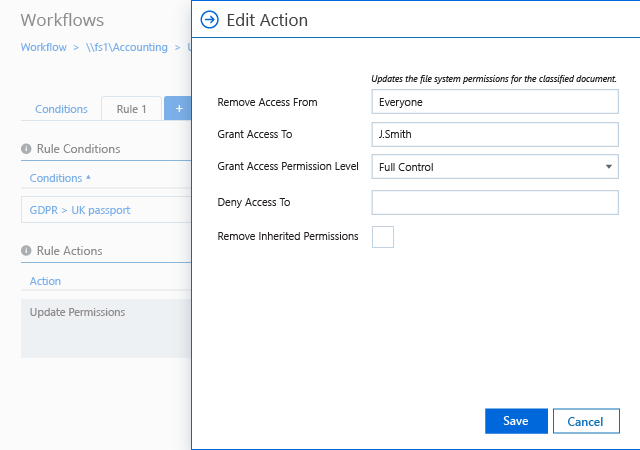
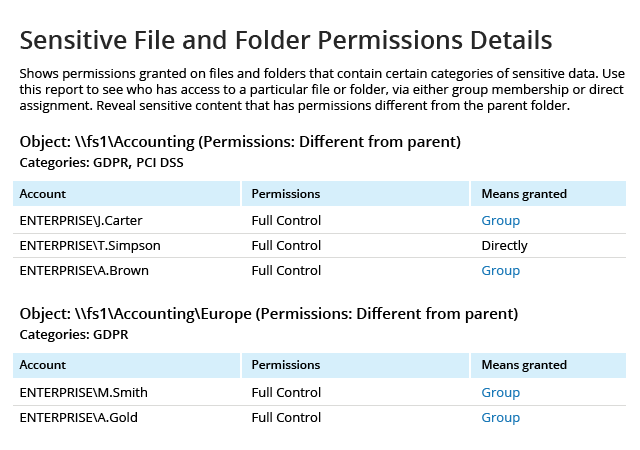
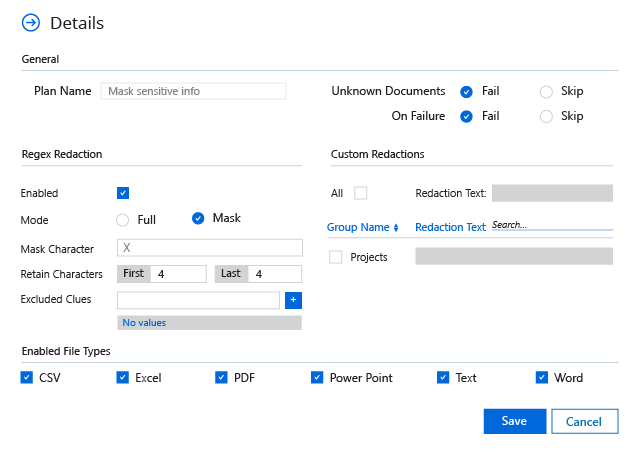
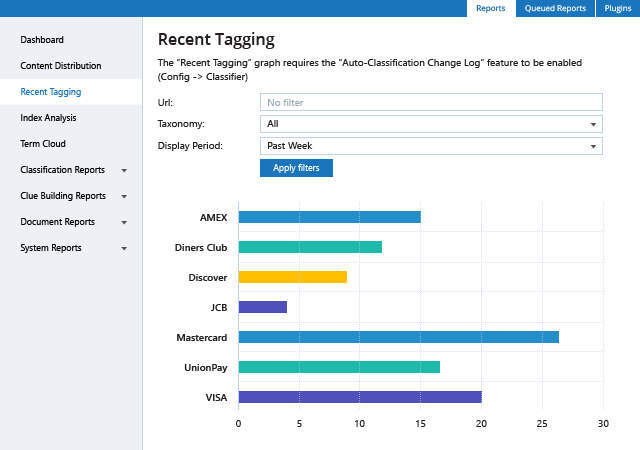
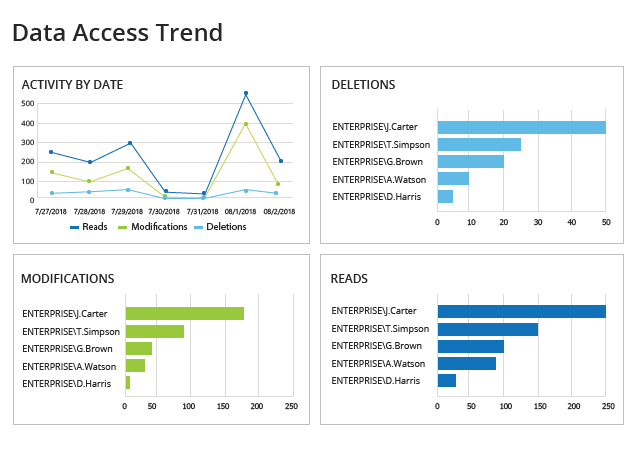
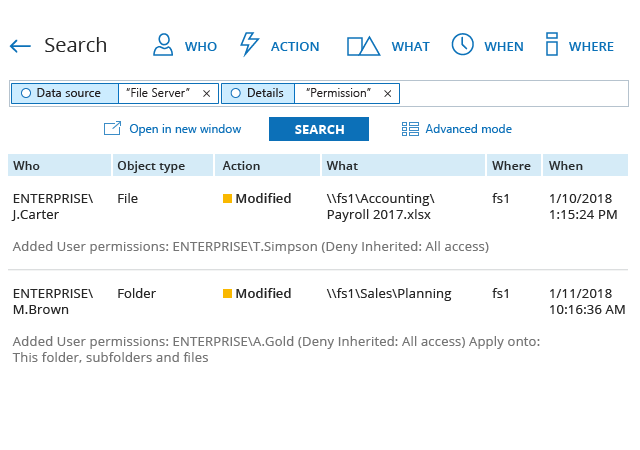
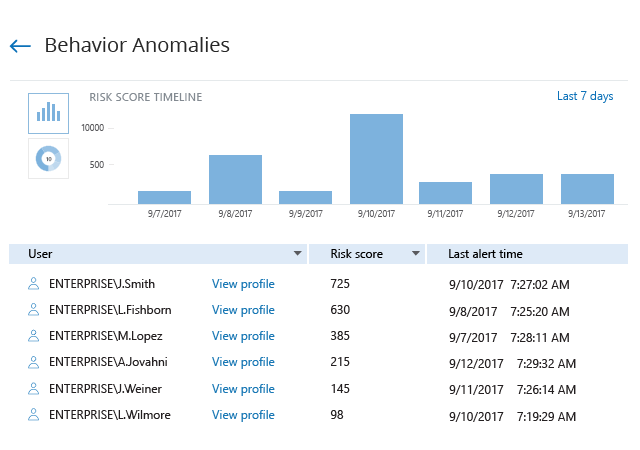
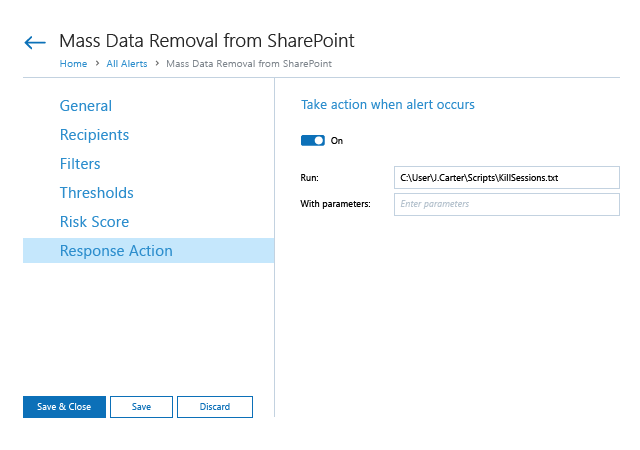
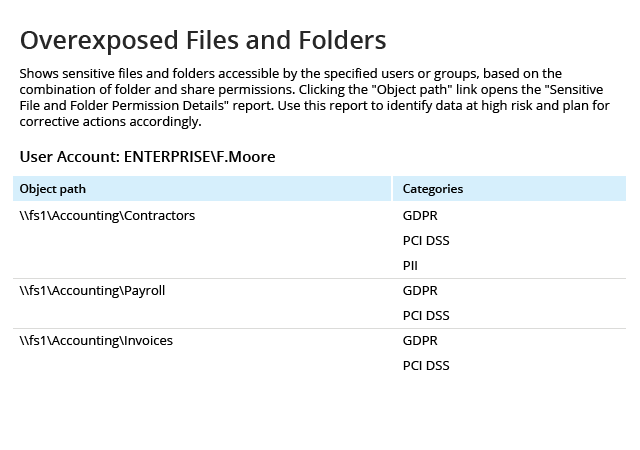
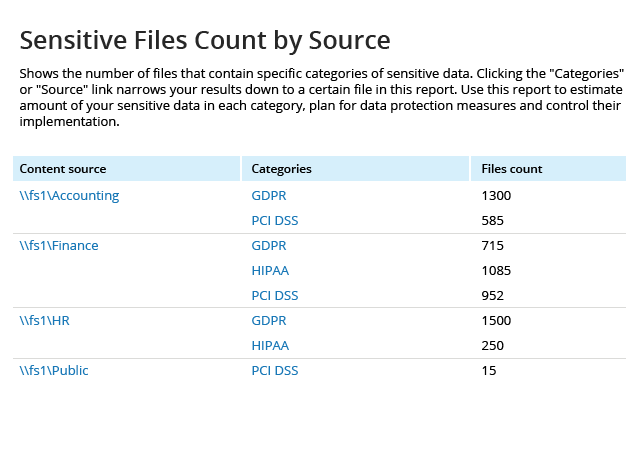
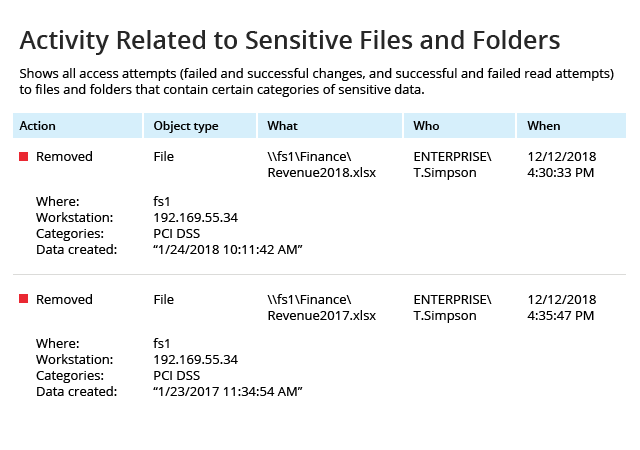
Spot security risks and safeguard sensitive data
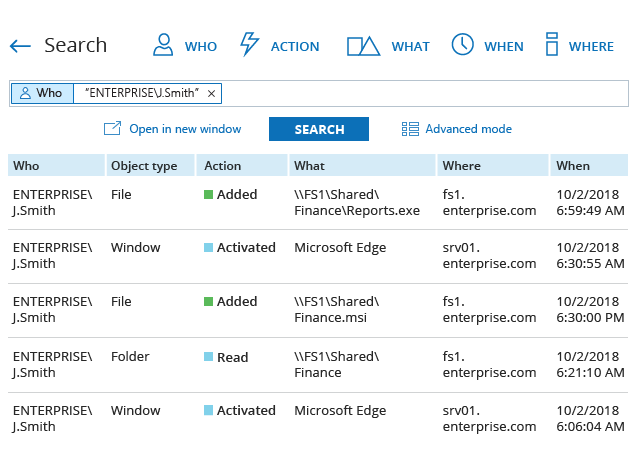
A data breach can happen to any organization. Netwrix solutions can help you uncover and reduce your risks around sensitive data by proactively mitigating its overexposure and helping you promptly detect policy violations and suspicious user behavior.
Netwrix Data Security
See the full list of advantages and learn how Netwrix solutions can help you address your most pressing information protection challenges.
Netwrix ROI Calculator
Measure the expected return of your data security investment and prove the value of Netwrix solutions to your leadership team with hard data.
customer success