Protect Your Sensitive Data with Device Control Software
The everyday use of external peripherals like USB flash drives, Bluetooth devices, and other removable media may seem harmless, but they can be frequent culprits behind security breaches that can cause substantial damage to an organization. From data theft to non-compliance penalties, the repercussions can be severe. Both end-users and organizations must recognize these risks and implement robust preventive measures such as USB device management and controlling USB devices.
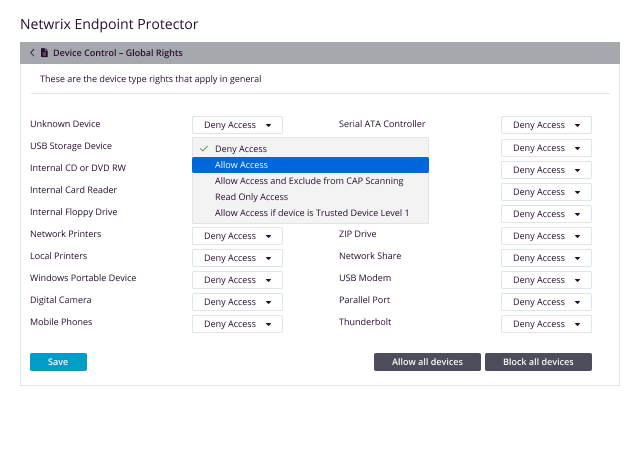
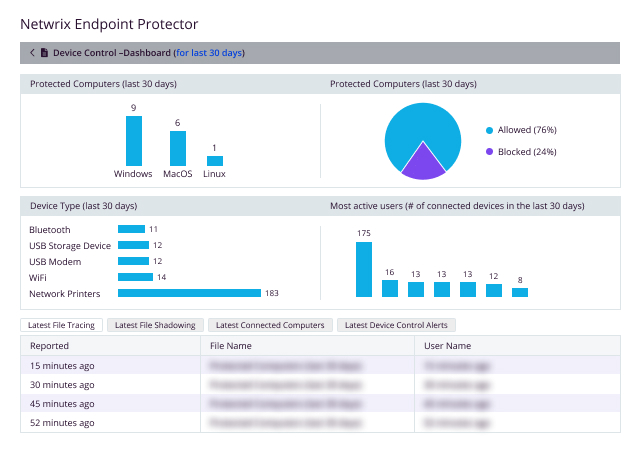
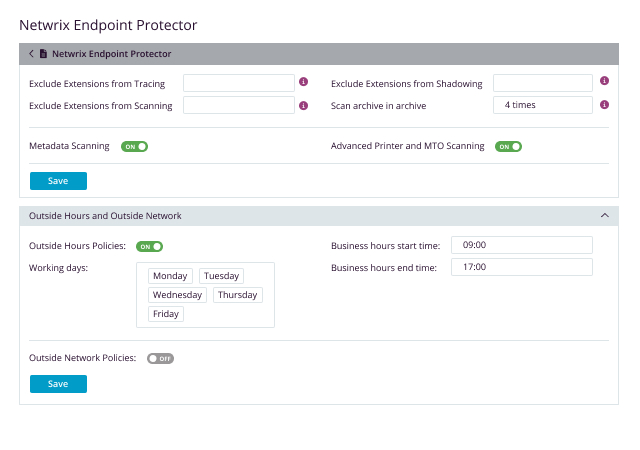
Lockdown, control, and monitor USB and peripheral ports to stop data theft and data loss
Gain full control of USB devices, Bluetooth, and peripheral ports
The centrally managed Device Control software solution enables access control and granular device control over device permissions, enabling full control of the USB ports and connected storage devices. This way, it prevents accidental or intentional data loss and transfers, while enabling endpoint protection against the spread of USB malware, BadUSB attacks, or viruses. With Netwrix Endpoint Protector Device Control Software, businesses can centralize user access management and customize access permissions for removable media connections.
Multiple deployment options