Shield Your Sensitive Data from Theft and Misuse with data at rest DLP Scanning
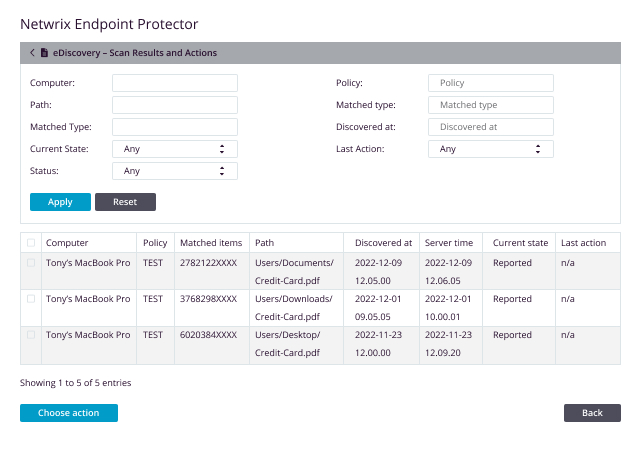
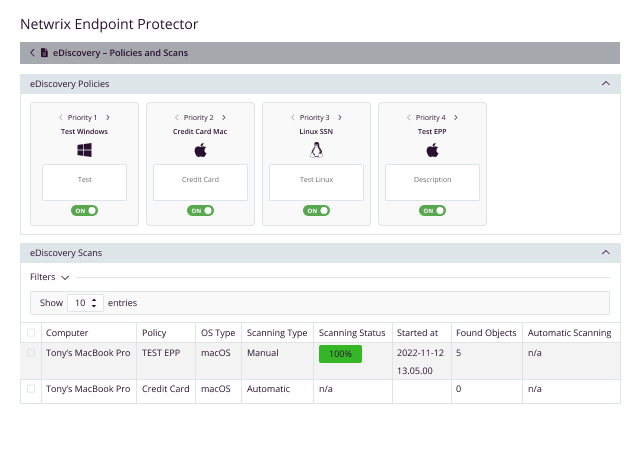
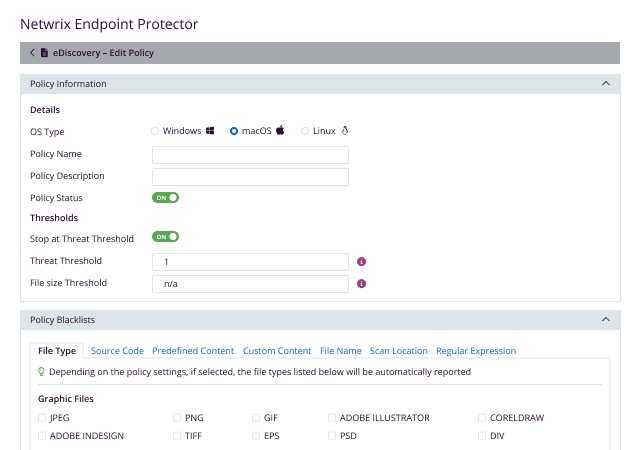
Netwrix Endpoint Protector's eDiscovery solution provides a robust and comprehensive approach to identifying and protecting sensitive data stored on endpoints across Windows, macOS, and Linux platforms. Its advanced content and contextual DLP scanning capabilities ensure that sensitive data is not overlooked, even when embedded within other files or compression techniques. With Common Criteria EAL2 certification, Netwrix Endpoint Protector eDiscovery DLP scanner demonstrates its commitment to the highest security standards, safeguarding your organization's valuable assets.
Main Features