Netwrix Change Tracker: Software de gestión de configuración de seguridad
Software de gestión de la integridad de archivos y configuración de seguridad que endurece sistemas, compara configuraciones y demuestra cumplimiento.
Lee sus historias
Confiado por





































































Erradique los cambios no autorizados y fortalezca su infraestructura
Fortalecer sistemas críticos
Fortalezca las configuraciones de seguridad en toda su infraestructura con nuestra herramienta de administración de configuración de seguridad.
Detección instantánea de cambios
Monitoree cambios no autorizados en tiempo real con escaneo avanzado de integridad de archivos y alertas instantáneas para una respuesta rápida.
Validación de cambios en tiempo real
Las integraciones de ITSM proporcionan un control de cambios inteligente y cerrado y reducen el ruido de los cambios que estaban planeados.
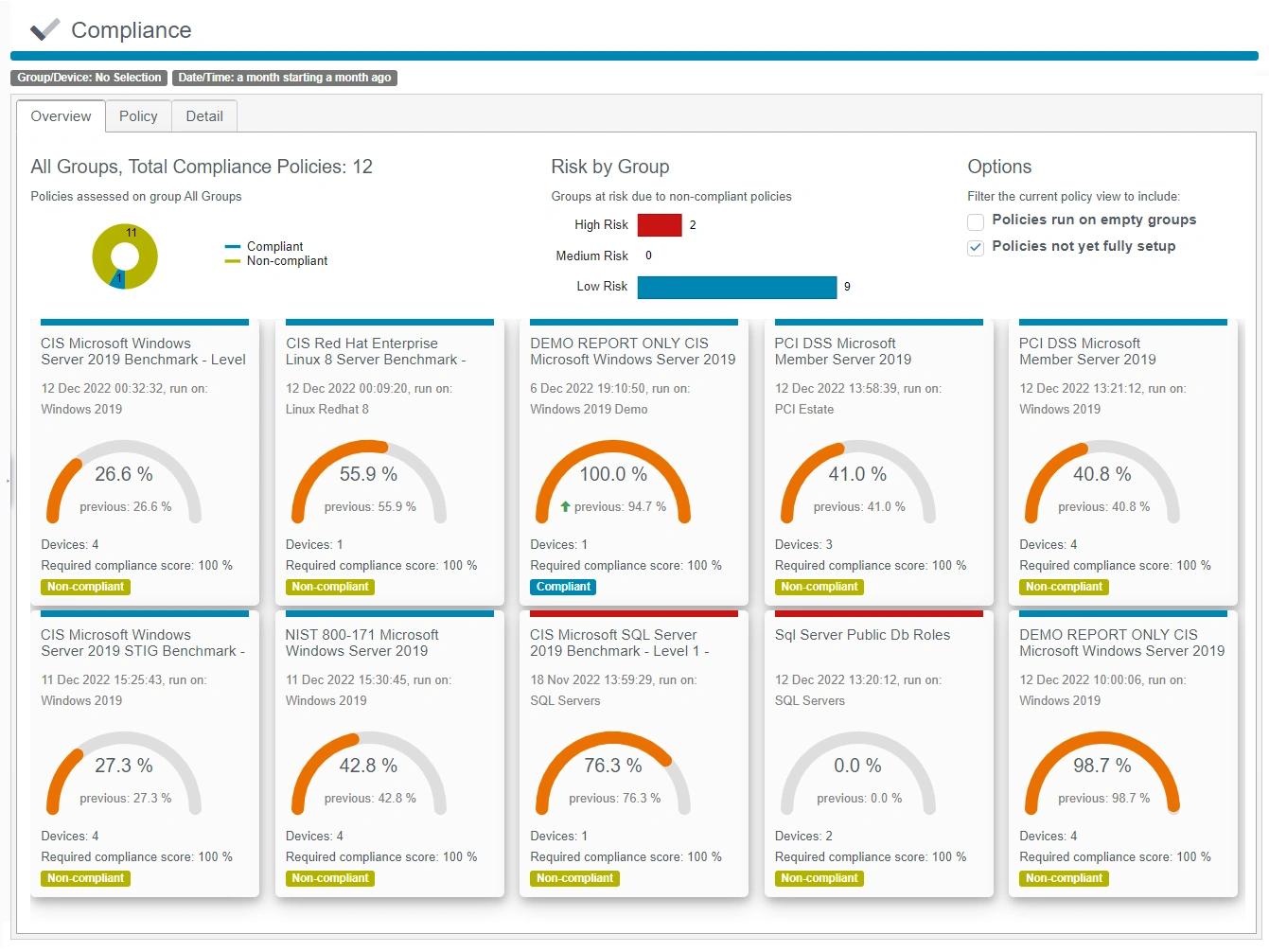
Cumpla con los requisitos de cumplimiento
Supere las auditorías regulatorias fácilmente con herramientas completas de gestión de configuración de seguridad e informes automatizados.
Capacidades
Supervise, detecte y responda a cambios en toda su infraestructura de TI con herramientas completas de gestión de configuración de seguridad
¿Listo para comenzar?
Soluciones
Vaya más allá de la protección contra amenazas únicas. Asegure cada aspecto con las soluciones de Netwrix.
Confiado por profesionales
No te conformes solo con nuestra palabra
Integraciones
Integraciones sin fisuras para una seguridad más inteligente
Ver todas las integraciones





