Verständnis von Golden Ticket-Angriffen
Ein Golden Ticket-Angriff ermöglicht es einem Angreifer, ein Kerberos Ticket Granting Ticket (TGT) mit dem KRBTGT-Schlüssel zu fälschen, um unbegrenzten, dauerhaften Zugriff auf eine Active Directory-Domäne zu erhalten.
Attribut | Details |
|---|---|
|
Angriffsart |
Golden Ticket Attack |
|
Auswirkungsgrad |
Kritisch |
|
Ziel |
Unternehmen, Regierung, Alle großen Organisationen |
|
Primärer Angriffsvektor |
Diebstahl von Anmeldeinformationen, Netzwerkausbeutung |
|
Motivation |
Spionage, Datendiebstahl, finanzieller Gewinn, Störung |
|
Gängige Präventionsmethoden |
KRBTGT Password Rotation, Credential Guard, Least Privilege, AD Hardening, Monitoring |
Risikofaktor | Level |
|---|---|
|
Möglicher Schaden |
Kritisch |
|
Einfachheit der Ausführung |
Hart |
|
Wahrscheinlichkeit |
Mittel |
Was ist ein Golden Ticket Angriff?
Denken Sie darüber nach, was das Goldene Ticket in Charlie und die Schokoladenfabrik bedeutete - uneingeschränkter Zugang zu allem, ohne Fragen zu stellen. Bei einem Golden Ticket-Angriff in der Cybersicherheit erhalten Hacker genau diese Art von VIP-Pass für Ihr gesamtes Netzwerk.
Hier wird ein Golden Ticket-Angriff erklärt. Ein Golden Ticket-Angriff ist eine Kerberos-Ausnutzungstechnik, bei der ein Angreifer den KRBTGT-Kontohash aus Active Directory verwendet, um Ticket Granting Tickets (TGTs) zu fälschen. Dies ermöglicht es ihnen, jeden Benutzer, einschließlich der Domänenadministratoren, zu imitieren und uneingeschränkten, langfristigen Zugang zu allen Domänenressourcen zu erhalten.
Angreifer verwenden häufig Tools wie Mimikatz oder Impacket, um den KRBTGT-Hash zu extrahieren und diese gefälschten Tickets zu generieren. Da die gefälschten TGTs kryptografisch gültig sind, wird das Key Distribution Center (KDC) ihnen vertrauen, selbst wenn Passwörter geändert werden - was eine grundlegende Schwäche im Kerberos-Protokoll aufzeigt.
Domänencontroller können diese gefälschten Tickets nicht von legitimen unterscheiden, daher markieren traditionelle Authentifizierungsprotokolle sie nicht als verdächtig. Die Bereinigung ist nicht so einfach wie das Ändern eines Passworts; Sie müssen den KRBTGT-Schlüssel auf jedem Domänencontroller zweimal rotieren, um die Fähigkeit des Angreifers, gefälschte Tickets zu erstellen, vollständig zu unterbinden.
Das Kerberos-Protokoll: Wie funktioniert es
- Ein Benutzer meldet sich an und sendet einen mit seinem Passwort-Hash verschlüsselten Zeitstempel an das Key Distribution Center (KDC) zur Vorauthentifizierung.
- Der KDC verfügt über einen gespeicherten Hash des Benutzerpassworts. Er verwendet ihn, um den Zeitstempel zu entschlüsseln, und wenn dieser gültig ist, authentifiziert er den Benutzer.
- Der KDC stellt ein TGT aus, das mit dem Hash des KRBTGT-Kontos verschlüsselt ist (standardmäßige Gültigkeit beträgt 10 Stunden).
- Mit dem TGT kann der Benutzer Zugriff auf mehrere Domänendienste anfordern, ohne sich erneut zu authentifizieren.
- Für jede Dienstanforderung stellt der Ticket-Granting Server (TGS) des KDC ein Dienstticket aus, das mit dem Hash des Dienstkontos signiert ist und eine direkte Verbindung zum Zielserver ermöglicht.
Wie nutzen Angreifer es aus?
Bei einem Golden Ticket-Angriff umgehen Angreifer das KDC, indem sie ihre eigenen TGTs generieren, um auf Domänenressourcen zuzugreifen. Um dieses TGT zu erstellen, benötigen sie:
- Der vollqualifizierte Domänenname (FQDN) des Domains
- Die Sicherheitskennung (SID) der Domäne
- Der Benutzername des Kontos, das sie zu imitieren beabsichtigen
- Das Passwort-Hash des KRBTGT-Kontos
Wie funktioniert ein Golden Ticket-Angriff?
Ein Golden Ticket-Angriff entfaltet sich in einer Reihe von Schritten, die es einem Angreifer ermöglichen, die vollständige Kontrolle über eine Active Directory-Umgebung zu erlangen und zu behalten. Lassen Sie uns jede Phase betrachten.
1. Erstmaliger Kompromiss
Der Angreifer dringt zunächst in ein Netzwerk ein, meistens durch Phishing-E-Mails, das Ausnutzen ungepatchter Schwachstellen oder das Stehlen schwacher Anmeldeinformationen.
2. Privilege Escalation
Sobald sie im System sind, suchen Angreifer nach höheren Privilegien. Sie könnten zusätzliche Passwörter knacken, Fehlkonfigurationen ausnutzen oder Schwachstellen zur Privilegienerweiterung missbrauchen, bis sie Domänen-Admin-Rechte oder Replikationsrechte auf einem Domain Controller erlangen. Dies sind mächtige Rollen, die ihnen direkten Zugriff auf Active Directory-Daten gewähren.
3. KRBTGT-Hash-Extraktion
Ausgestattet mit diesen Rechten verwendet der Angreifer bösartige Tools wie Mimikatz und die DCSync-Technik, um den Passworthash des KRBTGT-Kontos zu stehlen — den kryptografischen Schlüssel, der jedes Kerberos TGT signiert und das Fälschen neuer TGTs ermöglicht. Sie erfassen auch die Security Identifier (SID) der Domäne.
4. Ticketfälschung
Mit dem gestohlenen KRBTGT-Passworthash kann ein Angreifer ein gefälschtes TGT (Golden Ticket) für einen beliebigen Benutzer erstellen (häufig ein Konto mit hohen Privilegien). Angreifer können benutzerdefinierte Privilegien festlegen und die Gültigkeitsdauer des TGT verlängern, was ihnen effektiv einen ‚goldenen‘ Generalschlüssel für die Domäne gibt.
5. Ticket Injection & Lateral Movement
Der Angreifer injiziert das gefälschte TGT in eine aktive Sitzung. Da das Ticket kryptografisch gültig ist, kann der Angreifer nun legitime Ticket-Granting Service (TGS)-Tickets anfordern, um sich seitwärts über Server, Datenbanken, Dateifreigaben und Anwendungen zu bewegen, ohne Passwortaufforderungen auszulösen.
6. Persistenz & Evasion
Diese gefälschten Tickets bleiben vertrauenswürdig, bis der KRBTGT-Schlüssel auf jedem Domänencontroller zweimal rotiert wurde. Das Zurücksetzen von Passwörtern oder das Deaktivieren von Konten wird nicht helfen, da der Angreifer weiterhin neue Tickets erstellen kann. Daher können sie durch unauffälliges Einmischen in den normalen Kerberos-Verkehr langfristigen Zugang erhalten.
Angriffsflussdiagramm
Der Golden Ticket-Angriff folgt einer vorhersehbaren Ereigniskette. Lassen Sie uns ein Beispielangriffsszenario betrachten und die Angriffsphasen visualisieren, um zu verstehen, wie ein Eindringling von einem anfänglichen Bruch zu einer vollständigen Kontrolle einer Active Directory-Umgebung gelangen kann.
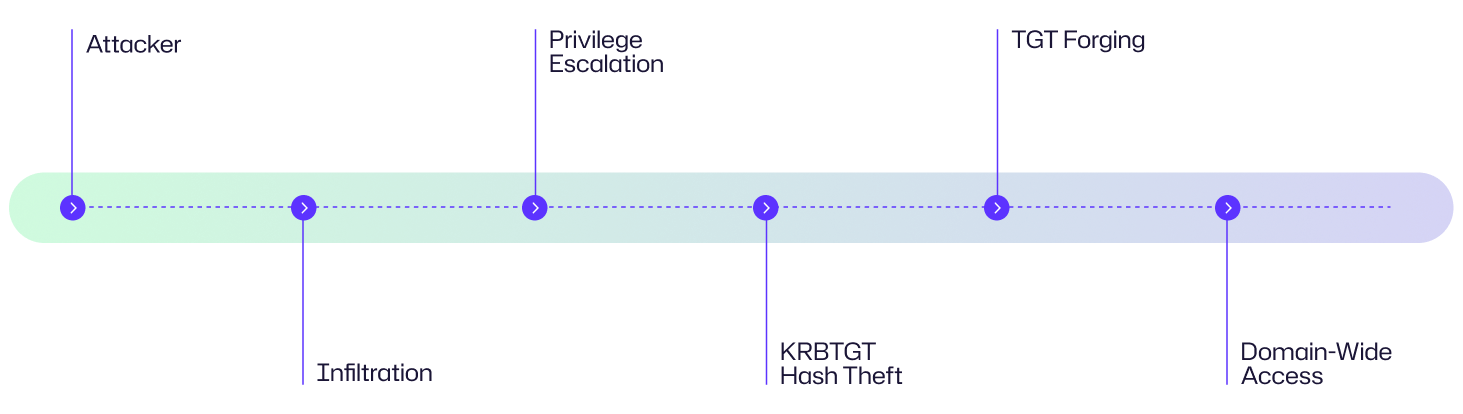
Stellen Sie sich einen regionalen Gesundheitsdienstleister vor, bei dem ein Mitarbeiter auf eine Phishing-E-Mail klickt und einem Angreifer so den ersten Zugang zum Netzwerk ermöglicht. Der Eindringling erhöht leise seine Privilegien, indem er eine falsch konfigurierte Dateifreigabe ausnutzt und schließlich Domain-Admin-Rechte erlangt. Mit Mimikatz extrahieren sie den KRBTGT-Hash, fälschen ihre eigenen Kerberos-Tickets und bewegen sich seitlich durch kritische Systeme, wie Patientenakten und Abrechnungsserver, ohne Passwortaufforderungen oder Sicherheitswarnungen auszulösen. Innerhalb von Stunden haben sie unbegrenzten, heimlichen Zugang zur gesamten Domäne.
Beispiele für einen Golden Ticket-Angriff
Golden Ticket-Angriffe wurden in realen Cyber-Spionagekampagnen eingesetzt, um langfristigen, unauffälligen Zugang zu hochwertigen Netzwerken zu erlangen. Die folgenden Fälle zeigen, wie verschiedene Bedrohungsgruppen diese Technik genutzt haben.
Fall | Auswirkung |
|---|---|
|
APT15 (Ke3chang) – Angriff auf britischen Regierungsdienstleister (2018) |
Im Jahr 2018 kompromittierte die mit China in Verbindung stehende Bedrohungsgruppe APT15 (auch bekannt als Ke3chang) einen britischen Regierungsauftragnehmer, der für hochsensible Projekte verantwortlich war. Nachdem sie einen ersten Zugang erlangt hatten, eskalierten die Angreifer ihre Privilegien zum Domain-Administrator und extrahierten den KRBTGT-Account-Hash aus Active Directory. Mit diesem Schlüssel generierten sie Kerberos Golden Tickets, die es ihnen ermöglichten, sich seitlich zu bewegen, vertrauliche Regierungsdaten zu sammeln und diese über einen längeren Zeitraum zu exfiltrieren. Die Untersuchung der NCC Group ergab, dass APT15 Mimikatz verwendete, um Anmeldeinformationen zu dumpen und Kerberos Golden Tickets zu generieren. Da Golden Tickets so lange vertrauenswürdig bleiben, bis der KRBTGT-Schlüssel auf allen Domänencontrollern zweimal rotiert wurde, behielten die Angreifer auch lange nach der Entdeckung des ersten Eindringens einen unauffälligen, dauerhaften Zugang. |
|
TA428 – Militärindustrielle Unternehmen in Osteuropa (2022) |
Im Jahr 2022 startete die mit China in Verbindung stehende Bedrohungsgruppe TA428 eine Cyber-Spionagekampagne gegen militärisch-industrielle Unternehmen und Regierungsinstitutionen in Osteuropa und Asien. Nachdem sie sich durch Spear-Phishing in Netzwerke eingeschlichen und Domänencontroller-Privilegien erlangt hatten, stahlen sie den KRBTGT-Kontohash und führten Kerberos Golden Ticket-Angriffe durch. Diese gefälschten Tickets gaben TA428 vollständige, langfristige Kontrolle über Opfer-Netzwerke, was umfangreiche Spionage und den Diebstahl großer Mengen sensibler militärischer Forschung, Verteidigungstechnologie-Daten und vertraulicher Kommunikation ermöglichte. |
|
Antlion – Finanzinstitutionen in Taiwan (2020–2021) |
Von 2020 bis 2021 hat die mit China verbundene Gruppe Antlion taiwanesische Finanzinstitutionen durch Spear-Phishing und maßgeschneiderte Schadsoftware infiltriert. Nachdem sie Zugang zum Domain-Controller erlangt hatten, stahlen sie den KRBTGT-Hash und starteten Kerberos Golden Ticket-Angriffe. Dies verschaffte ihnen anhaltenden, domänenweiten Zugriff auf kritische Finanzsysteme für Überwachung, Datendiebstahl, potenziellen Betrug und Sabotage. Laut Symantec verwendete Antlion unter anderem ein „Kerberos-Golden-Ticket-Tool basierend auf dem Mimikatz“. |
Folgen eines Golden Ticket-Angriffs
Ein erfolgreicher Golden Ticket-Angriff kann weitreichende und lang anhaltende Auswirkungen auf eine Organisation haben.
Einflussbereich | Beschreibung |
|---|---|
|
Finanziell |
Ein Golden Ticket-Angriff kann zu massiven finanziellen Kosten führen. Dies umfasst direkte Verluste durch finanziellen Betrug über manipulierte Systeme und regulatorische Strafen nach Gesetzen wie GDPR, HIPAA und SOX für Datenverletzungen und die Exfiltration sensibler Informationen. Organisationen stehen auch hohen Ausgaben für die Reaktion auf Vorfälle, forensische Untersuchungen und Sanierungsmaßnahmen gegenüber, zuzüglich zu Einnahmeverlusten durch Ausfallzeiten oder unterbrochene Dienstleistungen. In einigen Fällen können Angreifer auch Lösegeld- oder Erpressungszahlungen fordern. |
|
Operational |
Angreifer können kritische IT-Dienste wie Domain-Controller, Dateiserver und Geschäftsanwendungen stören. Dies kann zu einer verlängerten Ausfallzeit führen, die sich durch Lieferketten und Produktionszyklen zieht. Kompromittierte Zugriffskontrollen können weitreichendes administratives und operatives Chaos auslösen und sogar interne Systeme sabotieren, was die Wiederherstellung langsam und komplex macht. |
|
Reputations- |
Ein Sicherheitsvorfall dieses Ausmaßes untergräbt das Vertrauen von Kunden und Partnern, belastet langfristige Beziehungen und zieht negative Medienberichterstattung nach sich. Das Markenimage und der Marktruf der Organisation können leiden, während Investoren und Stakeholder die Prüfung intensivieren könnten, was die Bewertung des Unternehmens beeinflussen kann. |
|
Rechtliche/Regulatorische |
Organisationen sind in der Regel verpflichtet, Datenschutzverletzungen gemäß Datenschutzvorschriften wie der 72-Stunden-Regel der DSGVO zu melden. Sie können mit Klagen von betroffenen Kunden und Mitarbeitern sowie langfristigen Compliance-Prüfungen und Sanktionen von Aufsichtsbehörden konfrontiert werden. Bei schwerwiegenden Governance-Versäumnissen könnten sogar Führungskräfte persönlich haftbar gemacht werden. |
|
Verschlechterung der Sicherheitslage |
Da gefälschte Kerberos-Tickets legitim erscheinen, untergraben Golden Ticket-Angriffe die Wirksamkeit von Sicherheitskontrollen und Überwachungstools. Dies führt zu einer längeren Verweildauer des Angreifers, was die Erkennung und Reaktion auf Sicherheitsverletzungen erschwert. Die Integrität von AD könnte so stark beeinträchtigt werden, dass Organisationen einen vollständigen Neuaufbau der Umgebung in Betracht ziehen könnten. |
Häufige Ziele eines Golden Ticket-Angriffs: Wer ist gefährdet?
Einfach ausgedrückt, jede Organisation, die für den Benutzerzugang und das Identity Management auf AD angewiesen ist, könnte Ziel eines Golden Ticket-Angriffs sein. Angreifer bevorzugen Umgebungen, in denen ein einzelner Kompromiss weitreichenden und langfristigen Zugang zu kritischen Systemen und Daten gewähren kann. Zu den häufigen Zielen gehören möglicherweise:
|
Großunternehmen |
Unternehmen mit komplexen AD-Infrastrukturen und mehreren Domänencontrollern bieten eine breite Angriffsfläche. Hinzu kommen Organisationen mit zahlreichen privilegierten Konten und veralteten Systemen, die in der Regel eine schwache Netzwerksegmentierung und veraltete Sicherheitskontrollen aufweisen. Dies erleichtert es Angreifern, Tickets zu fälschen und sich seitlich zu bewegen, ohne entdeckt zu werden. |
|
Regierungsbehörden |
Regierungsbehörden verfügen über umfangreiche interne Netzwerke, die hochsensible Informationen enthalten, von Verteidigung und Geheimdiensten bis hin zu Daten der Strafverfolgung. Ein Golden Ticket-Angriff bietet dauerhaften Zugriff, um Motive wie Spionage, Überwachung und die Exfiltration von klassifiziertem Material zu bedienen. |
|
Finanzinstitute |
Banken und Finanzdienstleister verlassen sich stark auf AD, um interne Systeme zu sichern und Benutzer zu authentifizieren. Durch das Fälschen von Kerberos-Tickets können Angreifer verdeckten Zugang erhalten, um betrügerische Transaktionen durchzuführen, Finanzunterlagen zu manipulieren und hochwertige Kunden- und Zahlungsdaten zu stehlen. |
|
Gesundheitsorganisationen |
Krankenhäuser und Gesundheitsnetzwerke verwalten große Mengen an geschützten Gesundheitsinformationen (PHI) und sind auf AD angewiesen, um den Zugriff auf EMR-Systeme (elektronische Krankenakten), kritische medizinische Geräte und Patientendaten zu steuern. Diese Konzentration sensibler Informationen und die Notwendigkeit, Systeme rund um die Uhr am Laufen zu halten, machen Gesundheitsorganisationen zu attraktiven Zielen für Golden Ticket-Angriffe. |
|
Einzelhandelsketten |
Einzelhändler verwenden normalerweise AD, um Kassensysteme (POS), Lieferkettennetzwerke und Kundendatenbanken zu verwalten. Angreifer können gefälschte Tickets ausnutzen, um Transaktionen zu manipulieren, Zahlungskarteninformationen abzugreifen und Inventar und Logistik in großem Maßstab zu stören. |
|
Managed Service Providers (MSPs) und IT-Dienstleistungsunternehmen |
MSPs erhalten privilegierten Zugang zu Kundenumgebungen, was sie zu einem attraktiven 'One-to-Many'-Gateway macht. Wenn das AD eines MSP kompromittiert wird, können Angreifer in Kundennetzwerke eindringen, was die Auswirkungen über Organisationen hinweg vervielfacht. |
|
Organisationen mit Hybrid- oder Cloud-integriertem AD |
Unternehmen mit hybriden AD-Konfigurationen, wie On-Premises AD synchronisiert mit Microsoft Entra ID, haben oft komplexe Vertrauensbeziehungen und Replikationspfade. Wenn die Cloud-Connectoren falsch konfiguriert oder nicht gut gesichert sind, erweitern sie die Angriffsfläche und erleichtern es Angreifern, Tickets zu fälschen und langfristigen Zugriff zu behalten. |
Risikobewertung
Die Kombination aus kritischer Auswirkung und mittlerer Wahrscheinlichkeit stuft Golden Ticket-Angriffe in die Kategorie hohes Risiko ein.
Risikofaktor | Level |
|---|---|
|
Möglicher Schaden |
Kritische Ein Kompromiss ermöglicht es dem Angreifer, sensible Daten zu exfiltrieren, Geschäftsabläufe zu stören und Ransomware zu verbreiten. Die Wiederherstellung erfordert den Neuaufbau der AD-Umgebung und das erneute Sichern aller Vertrauensbeziehungen, was zu erheblichen Ausfallzeiten und finanziellen Verlusten führt. |
|
Einfachheit der Ausführung |
Hard Angreifer benötigen Zugriff auf den Domain-Controller und Kerberos-Expertise, um den KRBTGT-Hash zu stehlen und gefälschte Tickets zu erstellen, was den Angriff technisch anspruchsvoll macht. |
|
Wahrscheinlichkeit |
Mittel Obwohl nicht so häufig wie Phishing, bleibt die Wahrscheinlichkeit moderat, da gut finanzierte, qualifizierte und hartnäckige Bedrohungsakteure Active Directory oder hybride Umgebungen mit langen Verweildauern ins Visier nehmen. |
Wie man Golden Ticket-Angriffe verhindert
Golden Ticket-Angriffe gehören zu den schwerwiegenderen Bedrohungen für AD-Umgebungen. Ihre Erkennung ist schwierig und die Wiederherstellung kostspielig. Um diese Angriffe zu verhindern, müssen Organisationen eine Kombination aus Technologie, Werkzeugen und Prozesskontrollen einsetzen.
Technische Maßnahmen
Einige technische Maßnahmen zur Verhinderung eines Golden Ticket-Angriffs sind:
- Setzen Sie das KRBTGT-Konto-Passwort regelmäßig zweimal zurück: Drehen Sie den KRBTGT-Schlüssel sicher zweimal über alle Domänencontroller, ein Prozess, der sorgfältig geplant werden muss, um zu verhindern, dass Authentifizierungsdienste unterbrochen werden. Hier ist die richtige Vorgehensweise - ändern Sie das KRBTGT-Passwort, warten Sie auf die Replikation und ändern Sie es dann erneut. Dies macht alle unter dem alten oder Zwischen-Hash erstellten gefälschten Tickets ungültig.
- Implementieren Sie strikten Least Privilege Access: Stellen Sie sicher, dass nur eine minimale Anzahl von Benutzern und Dienstkonten hohe Privilegien besitzen. Begrenzen Sie die Mitgliedschaft in privilegierten Gruppen wie Domain-Admins. Entfernen Sie übermäßige Admin-Rechte und vermeiden Sie es, unnötigerweise administrative Rechte über Grenzen von Forest/Domain hinweg zu vergeben.
- Verwenden Sie gestufte Administrationsmodelle zur Segmentierung des Zugriffs: Gestufte Administrationsmodelle unterteilen die IT-Verwaltung in separate 'Ebenen' oder Privilegienstufen, jede mit ihrem eigenen Satz an Konten und Werkzeugen.
- Stufe 0: Domain-Controller, AD-Forest-Level-Dienste und andere kritische Identitätsinfrastrukturen
- Stufe 1: Server und Anwendungen
- Stufe 2: Benutzerarbeitsplätze und Standard-Desktops
Mit diesem Ansatz führt ein Kompromiss auf einer niedrigeren Ebene nicht automatisch zu einem vollständigen Domain-Kompromiss.
H3. Sicherheitstools
Sicherheitstools können dabei helfen, einen Golden Ticket-Angriff zu verhindern.
- Setzen Sie EDR und Advanced SIEM ein, um Anomalien in der Nutzung von Kerberos-Tickets zu erkennen: SIEM-Lösungen erkennen verdächtige Kerberos-Aktivitäten in Echtzeit, indem sie Authentifizierungsereignisse, ungewöhnliche Ticketlaufzeiten, unerwartete Anmeldungen und abnormalen Dienstticketgebrauch verfolgen. Sie analysieren Windows-Sicherheitsprotokolle auf TGT/TGS-Ereignisse, korrelieren Daten im Netzwerk und lösen zeitnahe Warnungen aus. EDR ergänzt dies, indem es Endpunkte vor auf Speicher basierendem Diebstahl von Anmeldeinformationen schützt.
- Verwenden Sie Credential Guard / OS-Level Protections, um den Diebstahl von Anmeldeinformationen im Speicher zu blockieren: Technologien wie Microsoft Defender Credential Guard sind darauf ausgelegt, Anmeldeinformationen im Speicher zu schützen. Indem der Zugriff auf den LSASS-Speicher eingeschränkt und das Betriebssystem ordnungsgemäß gepatcht und aktualisiert wird, können Organisationen das Risiko von Angriffen wie Mimikatz Golden Ticket verringern.
Nicht-technische Maßnahmen
Einige nicht-technische Präventionsmaßnahmen umfassen Folgendes:
- Schulen Sie Mitarbeiter im Umgang mit Phishing und Social Engineering: Da viele anfängliche Sicherheitsverletzungen auf Kompromittierungen von Anmeldeinformationen zurückzuführen sind (Phishing, bösartige Anhänge oder Links), sollten Organisationen Sensibilisierungsprogramme für Mitarbeiter einführen, um diese Einfallstore zu schließen.
- Implementieren Sie Change Management und Audit-Prozesse: Führen Sie formelle Änderungskontrollen und Audit-Prozesse für alle Modifikationen an Privileged Accounts, Berechtigungen, Domänenrichtlinien usw. durch. Es ist am besten, Protokolle zu führen, diese regelmäßig zu überprüfen und das Prinzip der minimalen Rechtevergabe sowie die Funktionstrennung bei jeglichen Änderungen durchzusetzen.
Wie Netwrix helfen kann
Netwrix bietet Tools zur Stärkung der Active Directory-Sicherheit und zur schnellen Erkennung von Anzeichen eines Golden Ticket-Angriffs. Netwrix Threat Prevention verfügt über umfangreiche Möglichkeiten zu:
- Überwachen Sie kontinuierlich die Kerberos-Authentifizierung und lösen Sie Alarme bei verdächtigen Ticketaktivitäten aus, wie ungewöhnlich lange Ticketlaufzeiten oder gefälschte PAC-Daten.
- Der Golden Ticket analytic type erkennt Kerberos-Tickets, die die konfigurierte maximale Lebensdauer überschreiten, und generiert Alarme.
- Der Forged PAC analytic type erkennt Kerberos-Tickets mit modifizierten PACs (Privilege Attribute Certificates). Da Golden Tickets oft PAC fälschen oder manipulieren, um Privilegien zu erhöhen, ist dies ein direktes Signal.
- Detect privilege escalations and unauthorized changes to critical AD objects, helping security teams respond before attackers gain persistence. Threat Prevention provides templates for privilege escalation detection. You can convert a Privilege Escalation template into an active policy to monitor for unauthorized permission changes and when a non-admin account gains elevated rights.
- Bieten Sie Echtzeitüberwachung, Alarmierung und Blockierung von hochriskanten oder unbefugten Änderungen im Active Directory. Netwrix Threat Prevention’s Active Directory-Lösung überwacht alle Authentifizierungen (Kerberos und NTLM), Objektmodifikationen, Gruppenmitgliedschaften, GPO-Bearbeitungen, AD-Replikationen, LSASS-Modifikationen und mehr. Sie bietet detaillierte Audit-Trails (Vor- und Nachänderungswerte, wer die Änderung vorgenommen hat), die helfen, frühe Anzeichen von Missbrauch zu erkennen.
Strategien zur Erkennung, Minderung und Reaktion
Golden Ticket-Angriffe sind schwer zu erkennen und zu mitigieren, da die gefälschten TGTs kryptografisch gültig sind und mit dem echten KRBTGT-Schlüssel signiert wurden, sodass normale Kerberos-Überprüfungen sie als echt behandeln. Selbst wenn Benutzerkontenpasswörter zurückgesetzt werden, kann der Angreifer weiterhin gültige Tickets generieren, solange er den KRBTGT-Hash besitzt. Und es hinterlässt kaum Spuren, weil der Angreifer sich nicht mit dem Domain-Controller verbinden muss, um neue Tickets anzufordern. Stattdessen können sie auf ihrem eigenen Rechner gültige Tickets erstellen und diese bei Bedarf vorlegen, um auf Netzwerkressourcen zuzugreifen.
IT-Teams sollten nach Anomalien suchen, die auf gefälschte oder langfristige Tickets hinweisen.
Ungewöhnliche Ticket-Lebensdauern
Kerberos-Tickets haben normalerweise eine Standardlebensdauer von etwa 10 Stunden und sind für 7 Tage erneuerbar. Ein gefälschtes Golden Ticket könnte jedoch so konfiguriert werden, dass es Monate oder sogar Jahre gültig ist. Sicherheitsüberwachungstools wie Netwrix Threat Prevention oder ein SIEM können solche Tickets erkennen und Alarme auslösen, die darauf hinweisen, dass ein Angreifer versucht, Zugang zu behalten, ohne sich erneut zu authentifizieren.
Tickets für nicht existierende oder inaktive Konten
Wenn Sie sehen, dass Kerberos-Diensttickets (Ereignis-ID 4769) an Konten ausgestellt werden, die deaktiviert, gelöscht wurden oder seit Monaten inaktiv sind, deutet dies stark darauf hin, dass ein Angreifer die Kontrolle über den KRBTGT-Hash hat und Tickets fälscht, um dieses Konto zu imitieren.
TGT-Wiederverwendung nach KRBTGT-Passwortänderungen
Nachdem das Passwort des KRBTGT-Kontos geändert wurde, sollten alle zuvor ausgestellten Tickets ungültig werden. Wenn Sie erfolgreiche Anmeldungen oder Dienstanfragen feststellen, die Tickets verwenden, die vor der Passwortänderung ausgestellt wurden, bedeutet dies, dass gefälschte Tickets, die mit dem gestohlenen Hash signiert sind, immer noch funktionieren. Die Überwachung von Kerberos-Authentifizierungsereignissen, die sich auf eine alte Schlüsselversionsnummer (KVNO) beziehen, ist eine effektive Erkennungsmethode.
Kerberos-Protokollanomalien
Achten Sie auf Authentifizierungsanfragen, die von Endpunkten stammen, die normalerweise nicht mit Domain-Controllern interagieren, oder auf plötzliche Spitzen bei Kerberos-Ereignis-IDs (4768, 4769, 4771). Dies sind Windows-Sicherheitsprotokoll-Ereignis-IDs, die von einem DC (oder einem anderen Kerberos-Schlüsselverteilungszentrum) generiert werden, wenn Kerberos-Operationen stattfinden:
- Ereignis-ID 4768: Wird generiert, wenn ein Benutzer oder Computer ein TGT vom Key Distribution Center anfordert (erster Schritt der Kerberos-Authentifizierung).
- Ereignis-ID 4769: Wird protokolliert, wenn der Client ein Service-Ticket (TGS) anfordert, um nach Erhalt eines TGT auf einen bestimmten Dienst zuzugreifen.
- Ereignis-ID 4771: Zeigt an, dass die Kerberos-Vorauthentifizierung fehlgeschlagen ist, oft aufgrund eines falschen Passworts, Zeit-Synchronisationsproblemen oder möglichen Brute-Force-Angriffen.
Wenn Sie auch bemerken, dass TGTs wiederholt auf einem einzelnen Host oder von geografisch ungewöhnlichen IP-Adressen generiert werden, betrachten Sie dies als ein Zeichen von Ticketfälschung.
Nicht übereinstimmende Service Principal Names (SPNs)
Ein weiteres Warnsignal für gefälschte Tickets und laterale Bewegungen ist, wenn Sie Tickets bemerken, die auf Dienste verweisen, die Sie nicht ausführen, oder plötzlich versuchen, innerhalb kurzer Zeit auf mehrere nicht zusammenhängende Dienste zuzugreifen.
Installation von Mimikatz
Wenn Ihr Antivirenprogramm bösartige Software erkennt, wie beispielsweise Tools zum Auslesen von Anmeldeinformationen oder andere Hilfsprogramme nach einer Kompromittierung, kann dies ein indirektes Zeichen eines Golden Ticket-Angriffs sein.
Sofortige Reaktion
Wenn Sie einen Golden Ticket-Angriff vermuten, handeln Sie schnell:
- Setzen Sie das KRBTGT Account Passwort zweimal zurück: Dadurch werden alle vorhandenen gefälschten Tickets ungültig, wie bereits im Abschnitt Technische Maßnahmen besprochen.
- Isolieren Sie betroffene Systeme und Konten: Trennen Sie kompromittierte Hosts vom Netzwerk und deaktivieren Sie alle Konten mit verdächtigen Kerberos-Aktivitäten, um eine weitere seitliche Bewegung zu stoppen.
- Aktive Sitzungen widerrufen: Um Angreiferzugriff zu unterbinden, können Sie Logoffs erzwingen oder Werkzeuge wie klist purge oder PowerShell’s Revoke-ADAuthentication verwenden, um alle Kerberos-Sitzungen zu beenden.
- Bewahren Sie forensische Beweise: Sichern Sie Sicherheitsprotokolle, Speicherauszüge und Systemabbilder, bevor Sie mit der Bereinigung beginnen, um bei Untersuchungen und möglichen rechtlichen Schritten zu helfen.
- Stakeholder benachrichtigen: Informieren Sie umgehend Ihr Incident-Response-Team, das Management sowie rechtliche oder Compliance-Verantwortliche, damit diese die Kommunikation, regulatorische Anforderungen und mögliche Auswirkungen auf Kunden bearbeiten können.
Langfristige Milderung
Organisationen sollten zukünftige Risiken durch proaktive Kontrollen, wie die hier aufgeführten, reduzieren.
- Verbessern Sie die Active Directory-Hygiene: Begrenzen Sie die Anzahl der privilegierten Konten, wenden Sie das Prinzip der geringsten Rechte an und überwachen Sie die Mitgliedschaften der Domain Admins und Enterprise Admins. Sie sollten auch starke Passwortrichtlinien durchsetzen und veraltete oder ungenutzte Konten entfernen, um die Angriffsfläche zu reduzieren.
- Regelmäßige Threat Hunting: Planen Sie Jagden, die sich auf Kerberos-Anomalien konzentrieren, wie ungewöhnliche Ticketlaufzeiten, unerwartete Schlüsselversionsnummern (KVNOs) oder Anmeldeaktivitäten von atypischen Hosts. Kombinieren Sie die Analyse von Ereignisprotokollen mit Ihrem SIEM oder Tools wie Netwrix Threat Prevention, um verdächtige Muster zu identifizieren.
- Periodische Überprüfungen von Privileged Accounts: Überprüfen Sie alle Privileged Accounts (einschließlich Dienstkonten) mindestens vierteljährlich. Verifizieren Sie den Besitz, die Notwendigkeit und die Passwortrotation, insbesondere für das KRBTGT-Konto. Es ist am besten, Konten, die veraltet oder unnötig sind, zu deaktivieren.
Branchenspezifische Auswirkungen
Golden Ticket-Angriffe können jede Organisation stören, aber die Risiken und regulatorischen Konsequenzen variieren je nach Branche. Durch das Verständnis der branchenspezifischen Auswirkungen können Organisationen ihre Verteidigungsstrategien und Reaktionspläne optimieren.
Industrie | Auswirkung |
|---|---|
|
Gesundheitswesen |
Gesundheitsnetzwerke speichern große Mengen sensibler Patientendaten und sind auf eine kontinuierliche Systemverfügbarkeit angewiesen. Ein Golden Ticket-Kompromiss könnte elektronische Gesundheitsakten offenlegen, klinische Abläufe stören und zu HIPAA-Verstößen führen, was schwere Geldstrafen und Reputationsschäden zur Folge haben könnte. |
|
Finanzen |
Banken und Finanzdienstleister können schwerwiegende Konsequenzen erleiden, da Angreifer gefälschte Tickets verwenden können, um auf Kernbanksysteme zuzugreifen, unbefugte Überweisungen auszuführen und Transaktionen zu manipulieren. Solche Sicherheitsverletzungen können zu massiven finanziellen Verlusten, betrügerischen Kontobewegungen, ernsthaften Strafen unter SOX oder anderen Finanzvorschriften und einfachem Verlust des Kundenvertrauens führen. |
|
Einzelhandel |
Einzelhändler unterhalten komplexe Lieferketten und verfügen über umfangreiche Kundendaten, daher kann ein Golden Ticket-Angriff besonders schädlich sein. Angreifer können von Unternehmensnetzwerken auf Point-of-Sale-Systeme und Partnerumgebungen übergehen, was zu großangelegtem Diebstahl von Zahlungskartendaten, der Offenlegung von Kundenakten und kostspieligen PCI DSS-Compliance-Strafen führen kann. All dies kann den Betrieb stören und das Kundenvertrauen untergraben. |
Entwicklung von Angriffen & Zukunftstrends
Neue Technologien und sich ändernde Angreiferverhaltensweisen führen dazu, dass Golden Ticket-Angriffe automatisierter, unauffälliger und schwerer zu kontrollieren werden.
Zunehmender Einsatz von KI
Angreifer beginnen künstliche Intelligenz in ihre Arbeitsabläufe zu integrieren, um das Fälschen von Tickets und die laterale Bewegung zu automatisieren. KI-gesteuerte Skripte können schnell privilegierte Konten identifizieren, gültige Tickets erstellen und die Aktivität anpassen, um unentdeckt zu bleiben. Dies verkürzt die Zeit vom ersten Kompromiss bis zur vollständigen Kontrolle über das Domain.
Deepfake-getriebenes Social Engineering
Deepfake-Audio und -Video verleihen Phishing- und Pretexting-Angriffen eine neue Dimension. Angreifer können in Sprach- oder Videoanrufen Führungskräfte oder IT-Personal imitieren und Mitarbeiter dazu verleiten, Passwörter preiszugeben oder Mehrfaktorauthentifizierungsaufforderungen zu genehmigen. Nachdem sie die anfänglichen Zugangsdaten erlangt haben, können sie den benötigten Brückenkopf schaffen, um den KRBTGT-Hash zu stehlen und einen Golden Ticket-Angriff zu starten.
Aufstieg ausgeklügelter Ransomware-Gruppen
Fortgeschrittene Ransomware-Gruppen kombinieren jetzt Datei-verschlüsselnde Malware mit Golden Ticket-Techniken. Indem sie langanhaltende Kerberos-Tickets fälschen, können sie selbst nach der Entdeckung des anfänglichen Kompromisses durch IT-Teams einen unauffälligen Domain-Admin-Zugang aufrechterhalten. Dies ermöglicht es ihnen, Systeme erneut zu verschlüsseln, heimlich Daten zu stehlen und höhere Lösegeldforderungen zu stellen.
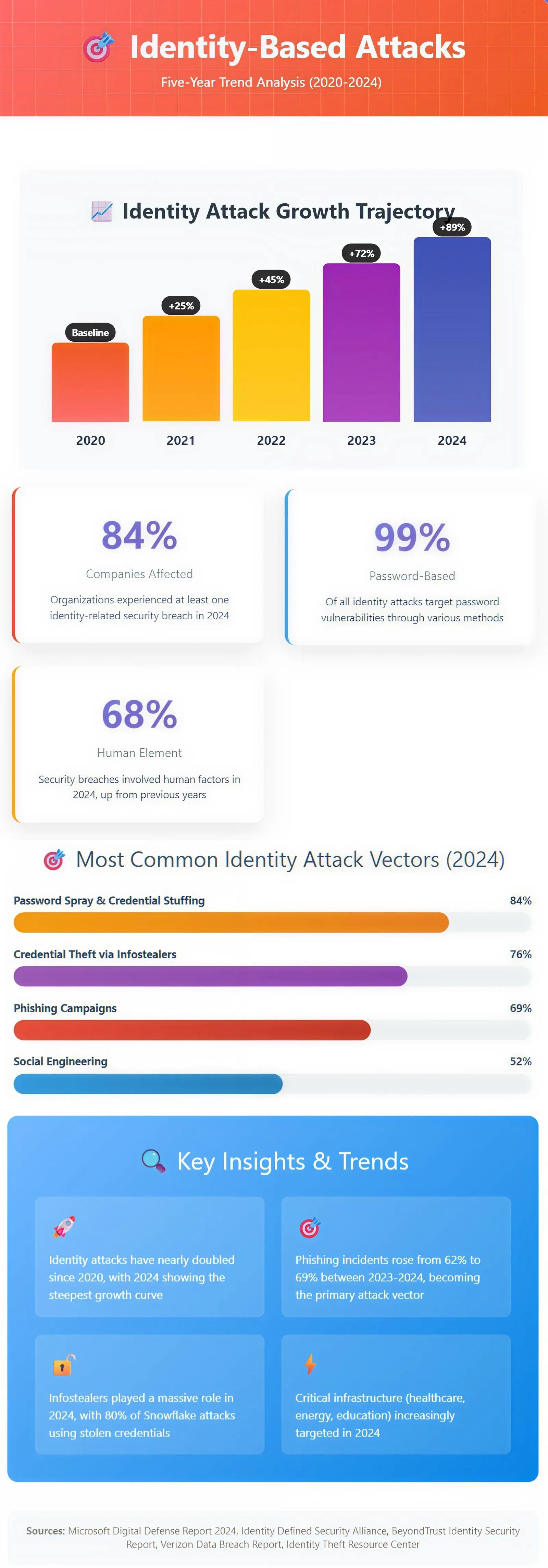
Wichtige Statistiken & Infografiken
Eine zunehmende Zahl von Belegen zeigt, dass Golden Ticket-Angriffe häufiger und unauffälliger eingesetzt werden. Google Cloud berichtet, dass die durchschnittliche Verweildauer (Zeit zwischen erstem Kompromiss und Entdeckung) bei vielen Arten von Angriffen von 16 Tagen im Jahr 2022 auf 10 Tage im Jahr 2023 gesunken ist.
Infografik: Trend von auf Identität basierenden Angriffen
Die folgende Infografik zeigt Trends bei identitätsbasierten Angriffen in den letzten fünf Jahren.
Quellen: Microsoft Digital Defense Report 2024, Identity Defined Security Alliance, BeyondTrust Identity Security Report, Verizon Data Breach Report, Identity Theft Resource Center
Abschließende Gedanken
Golden Ticket-Angriffe treffen das Herz Ihrer Active Directory-Sicherheit. Ihre Heimlichkeit, Hartnäckigkeit und Fähigkeit, traditionelle Sicherheitsmaßnahmen zu umgehen, machen sie zu einem potenziellen Albtraum für jede Organisation. Umfassende Sicherheit erfordert mehr als nur stückweise Verteidigung: Sie benötigt eine Strategie, die Prävention, kontinuierliche Erkennung und schnelle Reaktion kombiniert, um sich gegen eine Golden Ticket-Cybersicherheitsbedrohung zu verteidigen. Stärken Sie Ihre AD-Sicherheitslage noch heute mit Netwrix-Lösungen und bleiben Sie Angreifern, die ständig neue Ziele suchen, immer einen Schritt voraus.
FAQs
Teilen auf
Zugehörige Cybersecurity-Angriffe anzeigen
Missbrauch von Entra ID-Anwendungsberechtigungen – Funktionsweise und Verteidigungsstrategien
AdminSDHolder-Modifikation – Funktionsweise und Verteidigungsstrategien
AS-REP Roasting Attack - Funktionsweise und Verteidigungsstrategien
Hafnium-Angriff - Funktionsweise und Verteidigungsstrategien
DCSync-Angriffe erklärt: Bedrohung für die Active Directory Security
Golden SAML-Angriff
Angriffe auf Group Managed Service Accounts
DCShadow-Angriff – Funktionsweise, Beispiele aus der Praxis & Verteidigungsstrategien
ChatGPT Prompt Injection: Risiken, Beispiele und Prävention verstehen
NTDS.dit-Passwortextraktionsangriff
Kerberoasting-Angriff – Funktionsweise und Verteidigungsstrategien
Pass-the-Hash-Angriff
Pass-the-Ticket-Attacke erklärt: Risiken, Beispiele & Verteidigungsstrategien
Password-Spraying-Angriff
Angriff zur Extraktion von Klartext-Passwörtern
Zerologon-Schwachstelle erklärt: Risiken, Exploits und Milderung
Ransomware-Angriffe auf Active Directory
Active Directory mit dem Skeleton Key-Angriff entsperren
Laterale Bewegungen: Was es ist, wie es funktioniert und Präventionsmaßnahmen
Man-in-the-Middle (MITM)-Angriffe: Was sie sind & Wie man sie verhindert
Warum ist PowerShell so beliebt bei Angreifern?
4 Angriffe auf Dienstkonten und wie man sich dagegen schützt
Wie Sie Malware-Angriffe daran hindern, Ihr Geschäft zu beeinträchtigen
Was ist Credential Stuffing?
Kompromittierung von SQL Server mit PowerUpSQL
Was sind Mousejacking-Angriffe und wie kann man sich dagegen verteidigen
Diebstahl von Anmeldeinformationen mit einem Security Support Provider (SSP)
Rainbow-Table-Attacken: Wie sie funktionieren und wie man sich dagegen verteidigt
Ein umfassender Blick auf Passwortangriffe und wie man sie stoppt
LDAP-Aufklärung
Umgehen der MFA mit dem Pass-the-Cookie-Angriff
Silver Ticket Attack
