To register AD events you have to setup auditing first:
- Open the Group Policy Management console (gpmc.msc) on any domain controller in the target domain → Click Start → Go to Windows Administrative Tools (Windows Server 2016) or Administrative Tools → Choose Group Policy Management.
- Navigate to Domain Controllers. Right-click the effective domain controller’s policy and select Edit.
- In the Group Policy Management Editor, choose Computer Configuration → Go to Policies → Go to Windows Settings → Go to Security Settings → Go to Local Policies → Go to Audit Policy. Set the following audit policies:
- Audit account management: "Success"
- Audit directory service access: "Success"
- Audit logon events: "Success" and "Failure"
Alternatively, you can set Advanced audit policies: In the Group Policy Management Editor, expand Computer Configuration → Go to Policies → Go to Windows Settings → Go to Security Settings → Go to Advanced Audit Policy Configuration → Go to Audit Policies. Set the following audit policies:
- Account Management
- Audit Computer Account Management: "Success"
- Audit Distribution Group Management: "Success"
- Audit Security Group Management: "Success"
- Audit User Account Management: "Success"
- DS Access
- Audit Directory Service Access: "Success"
- Logon/Logoff
- Audit Logoff: "Success"
- Audit Logon: "Success"
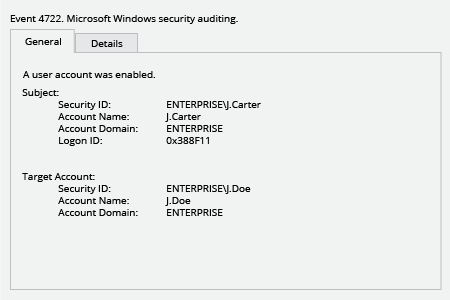
Each event type in log has its own Event ID. Below we're looking for “a user account was enabled” event.
- Right-click Start → Choose Event viewer.
- Click Windows logs → Choose the Security log.
- Click “Filter Current Log”.
- Specify event ID “4722” and click OK.
- Review the results.
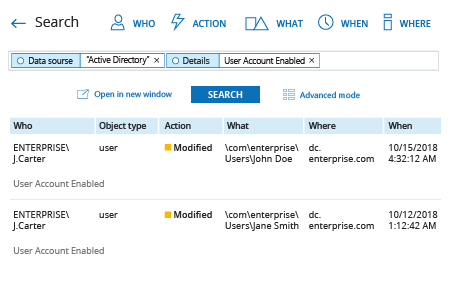
- Run Netwrix Auditor → Navigate to “Search” → Click on “Advanced mode” if not selected → Set up the following filters:
- Filter = “Data source”
Operator = “Equals”
Value = “Active Directory” - Filter = “Details”
Operator = “Contains”
Value = “User Account Enabled”
- Click the “Search” button and review your report.