Identity Governance and Administration (IGA) Solution
that Works for You
Ensure the right users have access to the right things at the right time.
Enhance security and accountability by ensuring only the right people or machines have access to the appropriate resources at the correct time and for the intended reasons.
Minimize security risks by limiting access to sensitive data
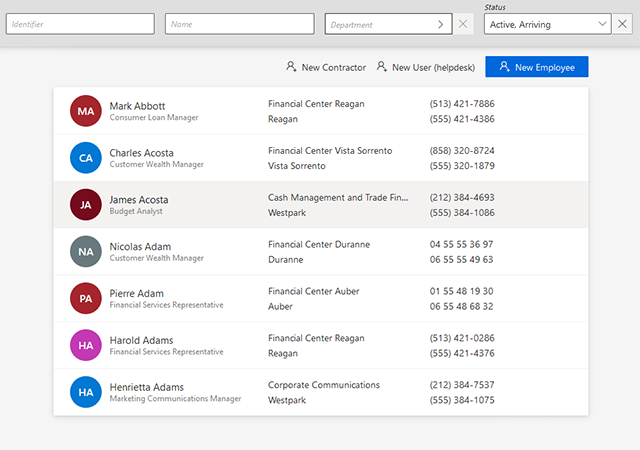
Access management often prioritizes technical user accounts over identities, sidelining valuable input from business users and burdening support. Empower business users to contribute to access management and governance, alleviating the workload of IT teams.
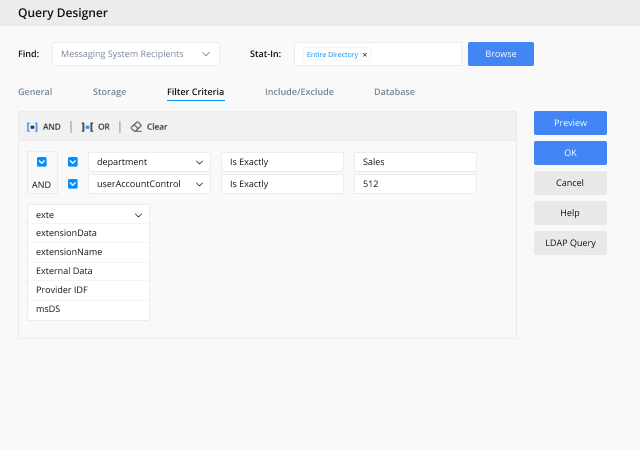
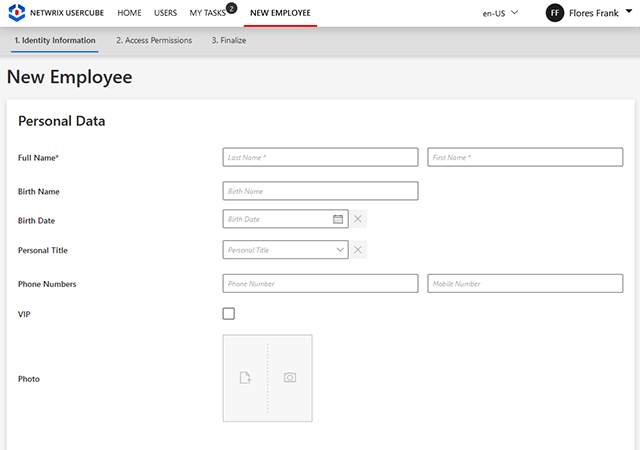
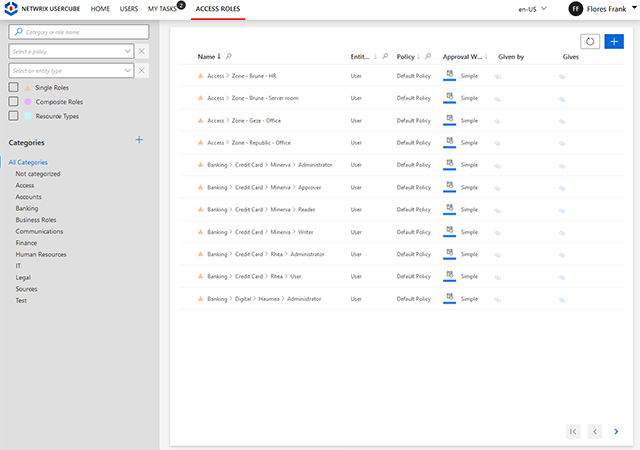
Enable granular policy implementation across diverse systems with customizable roles.
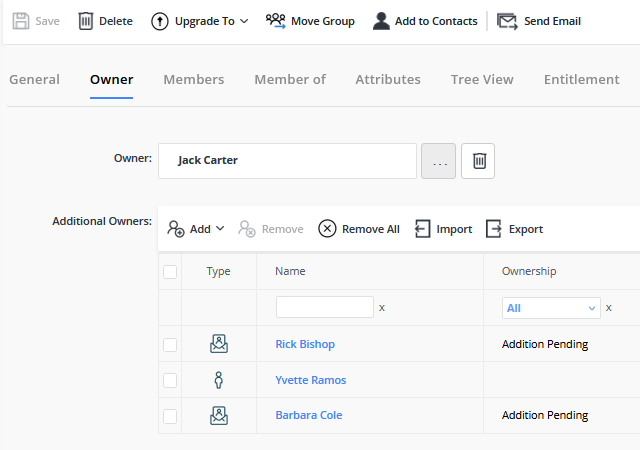
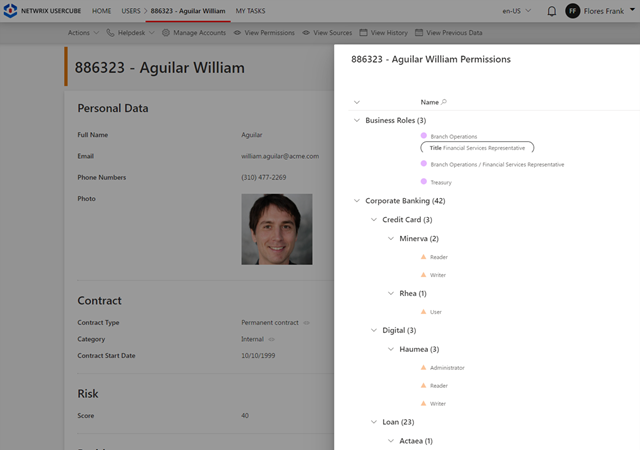
Implement robust policies with customizable roles in your identity management system. These roles, whether business or technical, offer granular control over capabilities and policy enforcement, while also enabling delegated control over objects from various systems.
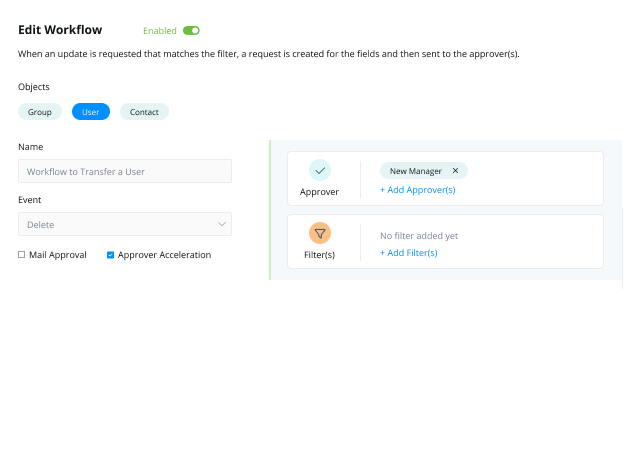
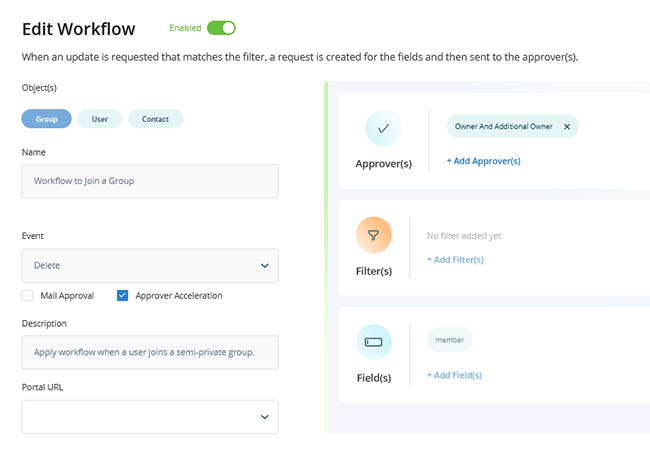
Build workflows that incorporate automated, human, and auditable processes.
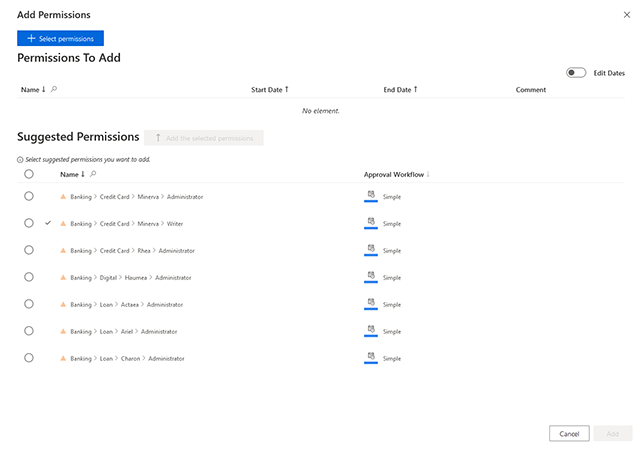
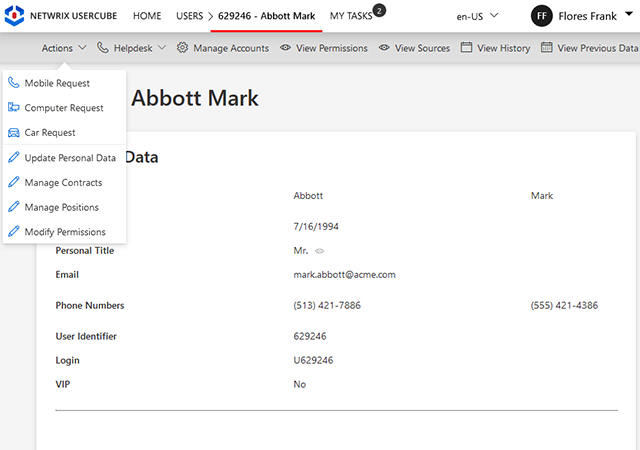
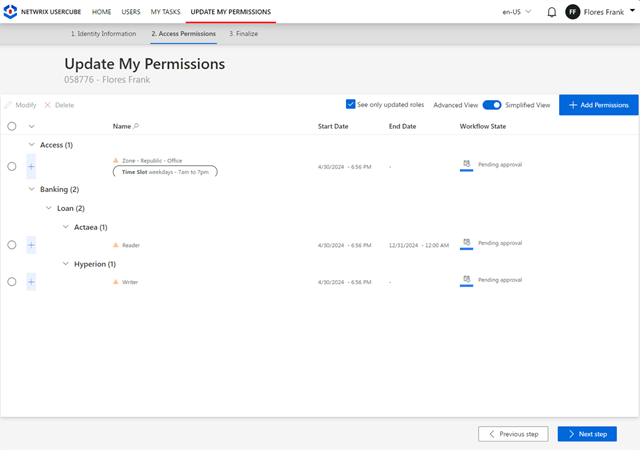
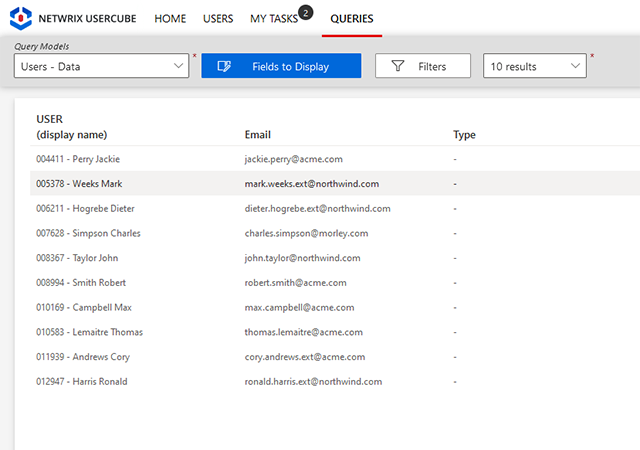
Empower users and their managers to request access through a self-service interface, sending requests for approval to relevant application owners or security officers. Streamline group management by allowing users to join or leave groups based on their roles, with oversight from business stakeholders.
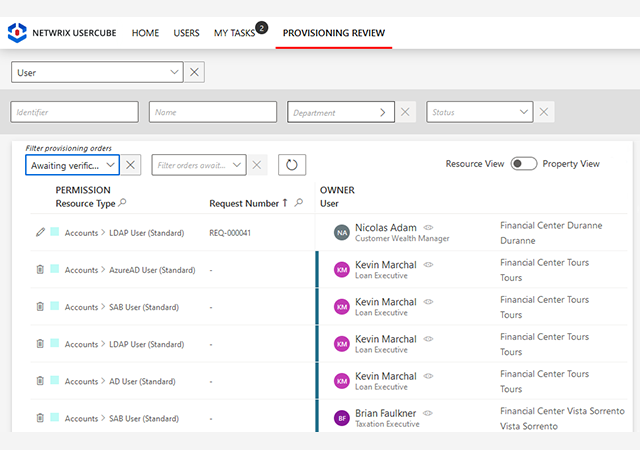
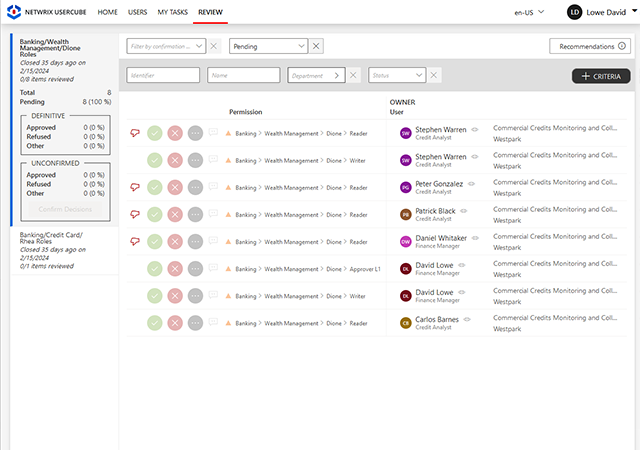
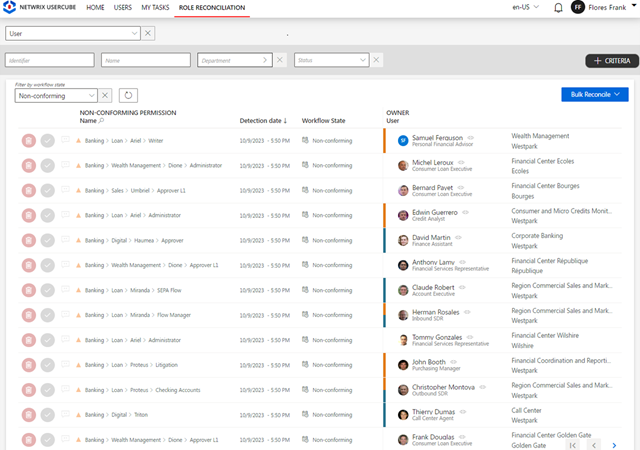
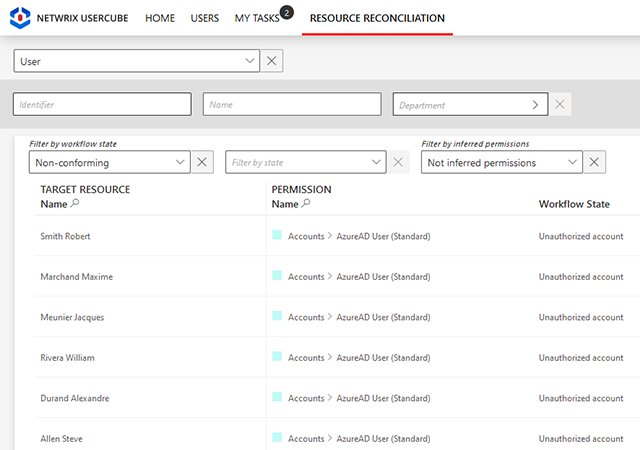
Thrill your auditors with automated attestation campaigns and compliance reports.
Maintain oversight of your identity governance and easily get the supporting data you need to prove compliance with an extensive set of customizable reports and an interactive requester to answer any question from an auditor.

Explore the Netwrix products that can help you secure identities with ease

Our approach ensures gradual organizational benefits through a phased deployment strategy, enabling you to maximize value as the deployment progresses.
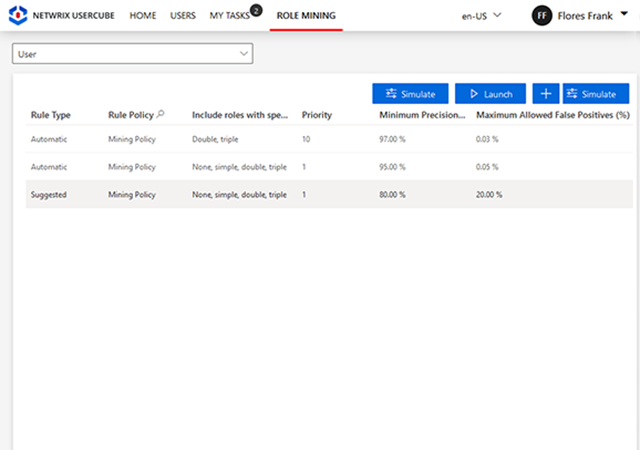
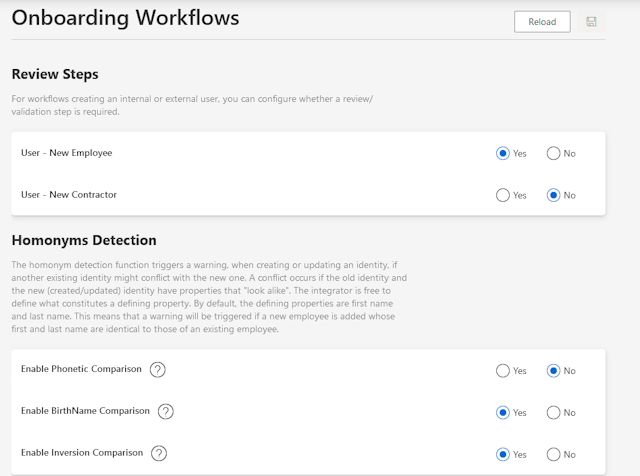
The solution can assist you at the outset by discovering and identifying identities and their misconfigurations. It also provides a means to control and manage your identities, and ultimately offers advanced identity governance capabilities for your entire set of human and non-human identities.
· It ensures that data access is restricted to authorized individuals.
· It supports internal controls and audit requirements to ensure compliance reporting integrity.
· It ensures proper access controls and segregation of duties to prevent fraud and errors.
· It supports compliance for NIST SP 800-53 and NIST Cybersecurity Framework (CSF) by providing a method for access control and identity management.
· It assists in meeting the requirements for an Information Security Management System (ISMS).
· It ensures that financial institutions protect customer information through proper access controls.
· It helps in managing the auditing of access to sensitive financial data.
We are dedicated to providing quick value on your IGA journey, helping you achieve organizational efficiencies swiftly and effectively.
Our 24-hour support team is made up of identity professionals who can help diagnose and identify problems you might be having and quickly present solutions to them.


_2.png)
_edit.png)