Introduction to Netwrix's Security Research
Jan 27, 2026
If you haven’t heard yet, Netwrix recently formed a dedicated in-house Security Research team on July 15, 2025. The team focuses on producing research across areas like identity, data security, AI, and cloud, while also translating publicly available research into practical improvements across our product portfolio so customers can benefit from it. Over the past six months, our Security Research team has been working closely with our R&D Engineering team to build a solution in Netwrix Threat Prevention 8.0 that helps defend against Active Directory Certificate Services (AD CS) attack paths, including the classic privilege escalation scenario where an attacker abuses a misconfigured certificate template to enroll and elevate access.
As a preview of what’s coming in Netwrix Threat Prevention 8.0, we’re introducing a new event type and policy option that helps block suspicious template enrollments, specifically when a UPN is being stamped into the SAN extension as part of a certificate request for example.
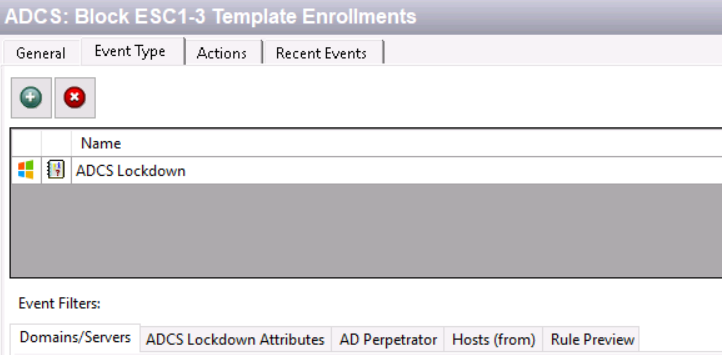
After enabling the ADCS Lockdown policy, the certificate template enrollment attempt, for example one initiated by Certify.exe, is now blocked.
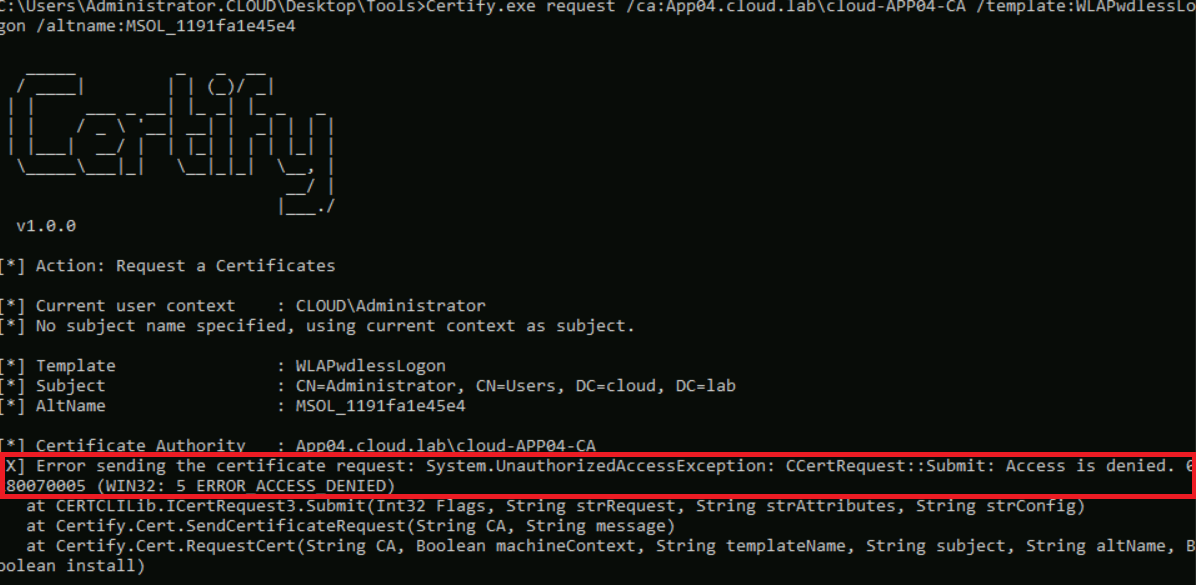
Another example we’ll be sharing in an upcoming public blog post is a case where our team identified an ESC1-style misconfiguration in a particular version of an MFA product that relied on an AD CS certificate template to enable passwordless logon for end users. Deploying this version of the product would introduce a serious AD CS attack path, allowing Authenticated Users to escalate to Domain Admin through the certificate template it relies on. This issue has been assigned a CVE, and it has been remediated in the updated version. In addition, we’ve collaborated with the PingCastle team to extend Entra ID assessment coverage. For PingCastle users, expect more updates and new capabilities in upcoming releases.
What’s coming in 2026?
Our focus in 2026 is to expand our research into attack paths that exist in virtualization platforms like vSphere ESXi, while also taking a deeper look at cloud components in Entra ID, such as Entra Agent ID for example, which is still in preview at the time of writing. Another focus area for us is creating more educational content around identity and data security. We’ll be publishing videos on our YouTube channel, covering how common attacks work, such as Kerberoasting, and how attackers abuse Active Directory to distribute ransomware. We’ll also be updating the Attack Catalog this year with new insights and additional coverage.
Share on
Learn More
About the author

