LDAP Reconnaissance
Reconnaissance is an important part of any successful attack. There are two key forms: initial or external reconnaissance that is performed before an adversary infiltrates an organization, and internal reconnaissance where they discover additional information and context about the organization’s environment.
LDAP reconnaissance is an internal reconnaissance technique attackers use to discover users, groups and computers in Active Directory. They use LDAP queries to increase their knowledge of the environment, which can help them find targets and plan the next stages of their attack. Because this technique is used by adversaries who have already infiltrated an organization, it is an internal (rather than external) reconnaissance technique.
Threat Summary
Target: Active Directory
Tools: BloodHound, PowerSploit, SharpHound, Spray
ATT&CK® Tactic: Discovery
ATT&CK Technique: T1087.002
Difficulty
Detection: Hard
Mitigation: Hard
Response: Medium
Performing Reconnaissance using LDAP
STEP 1: Obtain a foothold
Adversaries use a variety of techniques to gain a foothold in an organization’s IT environment, including phishing, watering hole and password spraying attacks. Here is how an adversary who has obtained a list of possible usernames can conduct a password spraying attack using Spray, a bash script made to perform password spray attacks on multiple platforms, against the organization’s virtual private network (VPN) server:
[attacker@machine ~]$ spray.sh -cisco vpn.org.com usernames.txt passwords.txt 1 35
Valid Credentials joed Summer2020
STEP 2: Perform reconnaissance using LDAP
The adversary uses the compromised credentials to authenticate to the VPN and gain network access, and then uses those same credentials to query Active Directory. They can enumerate Active Directory using the ActiveDirectory PowerShell module, or automate the discovery using tools like BloodHound and PowerSploit. In this example, the adversary uses PowerShell to look for possible passwords in users’ description attributes:
PS> Import-Module ActiveDirectory
PS> Get-ADObject -LDAPFilter "(&(objectClass=user)(description=*pass*))" -property * | Select-Object SAMAccountName, Description, DistinguishedName
SAMAccountName DescriptionDistinguishedName
-------------- ----------------------------
AlicePassword: P@ssw0rd123!CN=Alice,OU=Users,DC=domain,DC=com
PS>
STEP 3: Use information to further objectives
Using the credentials they have found, the adversary conducts further internal reconnaissance using tools like BloodHound and SharpHound, which assist with untangling complex webs of permissions. Using this information, the adversary can map out pathways to objectives, such as domain dominance.
The graphic below illustrates an example. Suppose an attacker gains the credentials for the user account Alice. That account has WriteDACL and WriteOwner permissions to the user Eve, which means Alice can grant herself access to Eve’s account. Eve has rights to reset the password of the account Bob, and Bob has permissions (granted through AdminSDHolder propagation) to modify the Domain Admins group. Therefore, finding Alice’s password was very valuable the adversary!
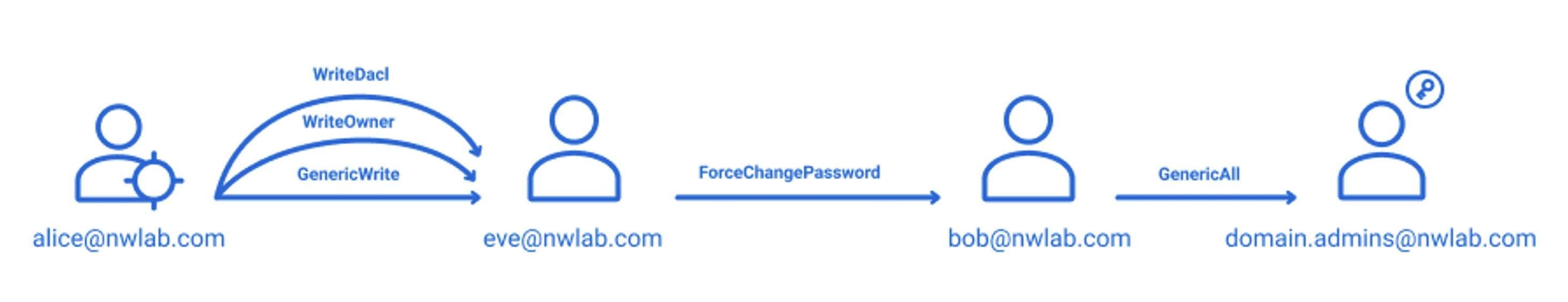
Result
After collecting data with SharpHound.exe -C All the adversary can load the data set into BloodHound to explore pathways to domain dominance.
Detect, Mitigate and Respond
Detect
Difficulty: Hard
The LDAP protocol is used frequently in Active Directory, so it is difficult to separate malicious queries from legitimate ones. Moreover, Active Directory does not provide a mechanism for logging the exact queries received; however, some degree of profiling and monitoring for access to specific attributes can be achieved using event 4662 in the subcategory Audit Directory Service Access.
Monitoring network traffic received by domain controllers for specific LDAP queries can help you detect adversary activity. The following table shows a small sampling of the kinds of queries that should be infrequent in normal operation but can provide strong signals of adversary activity:
Query | Information Collected |
|---|---|
|
(&(ObjectClass=user)(servicePrincipalName=*)) |
All user objects that have a ServicePrincipalName configured |
|
(userAccountControl:1.2.840.113556.1.4.803:=65536) |
Objects that have Password Never Expires set |
|
(userAccountControl:1.2.840.113556.1.4.803:=4194304) |
Objects that do not require Kerberos pre-authentication |
|
(sAMAccountType=805306369) |
All computer objects |
|
(sAMAccountType=805306368) |
All user objects |
|
(userAccountControl:1.2.840.113556.1.4.803:=8192) |
All domain controller objects |
|
(primaryGroupID=512) |
All Domain Admins using PrimaryGroupID |
Mitigate
Difficulty: Hard
Because LDAP plays an essential role in normal Active Directory operations, organizations cannot simply block its use. Instead, focus on mitigations that prevent infiltration in the first place: user awareness and training, endpoint compromise detection and response, phishing detection and prevention, email security, multi-factor authentication (MFA), and so on.
Respond
Difficulty: Medium
If LDAP reconnaissance is detected in the environment, activate the incident response process and alert the incident response team.
If an adversary’s presence is confirmed:
- Reset the password and disable the user account performing reconnaissance.
- Quarantine the source computer for forensic investigation and eradication and recovery activities.
Share on
View related cybersecurity attacks
Abusing Entra ID Application Permissions – How It Works and Defense Strategies
AdminSDHolder Modification – How It Works and Defense Strategies
AS-REP Roasting Attack - How It Works and Defense Strategies
Hafnium Attack - How It Works and Defense Strategies
DCSync Attacks Explained: Threat to Active Directory Security
Pass the Hash Attack
Understanding Golden Ticket Attacks
Group Managed Service Accounts Attack
DCShadow Attack – How It Works, Real-World Examples & Defense Strategies
ChatGPT Prompt Injection: Understanding Risks, Examples & Prevention
NTDS.dit Password Extraction Attack
Kerberoasting Attack – How It Works and Defense Strategies
Pass-the-Ticket Attack Explained: Risks, Examples & Defense Strategies
Password Spraying Attack
Plaintext Password Extraction Attack
Zerologon Vulnerability Explained: Risks, Exploits and Mitigation
Active Directory Ransomware Attacks
Unlocking Active Directory with the Skeleton Key Attack
Lateral Movement: What Is It, How It Works And Preventions
Man-in-the-Middle (MITM) Attacks: What They Are & How to Prevent Them
Why Is PowerShell So Popular for Attackers?
What is Credential Stuffing?
Compromising SQL Server with PowerUpSQL
What Are Mousejacking Attacks, and How to Defend Against Them
Stealing Credentials with a Security Support Provider (SSP)
Rainbow Table Attacks: How They Work and How to Defend Against Them
A Comprehensive Look into Password Attacks and How to Stop Them
Silver Ticket Attack
Bypassing MFA with the Pass-the-Cookie Attack
Golden SAML Attack
