Netwrix Auditor: O Software de Monitoramento NetApp
Acompanhe cada mudança e evento de acesso em seus sistemas de arquivos com monitoramento inteligente NetApp que transforma logs em insights acionáveis.
Leia suas histórias
Confiado por





































































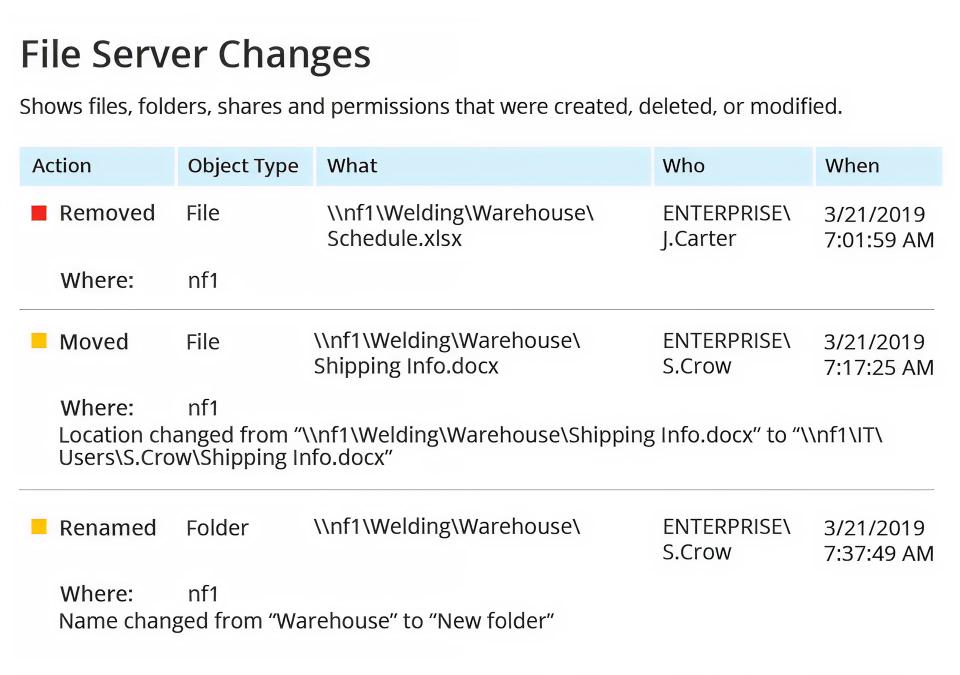
Uma ferramenta abrangente de monitoramento NetApp que trabalha de forma mais inteligente
Detectar ameaças à segurança dos dados
Obtenha visibilidade sobre alterações suspeitas e acesso a dados, comportamento anormal de usuários, direitos de acesso excessivos e mais.
Passe em auditorias com facilidade
Forneça relatórios mapeados para as regulamentações de conformidade mais comuns, incluindo PCI DSS, HIPAA, SOX, GLBA, FISMA/NIST, CJIS e GDPR.
Aumente a produtividade da equipe de TI
O software de monitoramento NetApp ajuda sua equipe de TI a detectar, investigar e remediar mudanças mais rapidamente para que possam se concentrar nas coisas que realmente importam.
Correlacione atividades entre sistemas
Correlacione a atividade da NetApp com outros sistemas para revelar a história completa sobre ataques ou comportamentos de ameaças internas.
Capacidades
Transforme a complexidade em inteligência com o software de monitoramento NetApp projetado para ambientes de armazenamento modernos
Pronto para começar?
Soluções
Vá além da proteção contra uma única ameaça. Proteja todos os ângulos com as soluções Netwrix.






