Password Spraying Attack
Password spraying is an attack technique in which an adversary attempts to compromise user accounts by trying to authenticate with a curated list of passwords that are either frequently used or likely to be used by their target. Password spraying can be conducted by an external adversary against any internet-facing system or SaaS application, or by an adversary that has gained a foothold within the network and is seeking to widen their access.
Frequent targets for password spraying include VPN servers, web-based email applications and single sign-on providers.
Unlike credential stuffing where an adversary is targeting specific users with previously compromised passwords, password spraying is about trying common or likely passwords against as many users as possible. Thus, many adversaries structure their attacks to avoid detection, perhaps trying only one password for each user account at a time or waiting some time between attempts.
Threat Summary
Target: Active Directory, Entra ID (formerly Azure AD)
Tools: SprayingToolkit, DomainPasswordSpray, MailSniper, RDPassSpray
ATT&CK® Tactic: Credential Access
ATT&CK Technique: T1110.003
Difficulty
Detection: Hard
Mitigation: Medium
Response: Low
Attack Tutorial: How a Password Spraying Attack Works
STEP 1: Perform external reconnaissance
Before conducting the password spray attack itself, an adversary must conduct reconnaissance to acquire a list of usernames (or email addresses, if the target uses them as usernames) that are likely to correspond to active users. Strategies include using open-source intelligence (OSINT) sources (such as Google searches, LinkedIn and Facebook) or purchasing a business directory. They may be able to discover the username format easily or may need to socially engineer an employee to reveal it.
In this example, the adversary has gathered the email addresses of employees to target.
PS> cat userlist.txt
Harry.Potter@stealthdefendlab.com
Hermione.Granger@stealthdefendlab.com
Ron.Weasley@stealthdefendlab.com
PS>
STEP 2: Conduct a password spraying attack
With the list of likely valid usernames, the adversary can begin their password spraying attack. Adversaries may conduct these attacks slowly to reduce the risk of detection. Tools such as the SprayingToolkit can automate the process of conducting the attack. In this example, the adversary attempts to authenticate to Office 365 hosted email using each of the email addresses combined with a weak (but common!) password.
Python> atomizer.py owa stealthdefendlab.com 'Spring2020' userlist.txt
�[34m[*]�[0m Trying to find autodiscover URL
�[32m[+]�[0m Using OWA autodiscover URL: http://autodiscover.stealthdefendlab.com/autodiscover/autodiscover.xml
�[34m[*]�[0m OWA domain appears to be hosted on Office365
�[34m[*]�[0m Using Office 365 autodiscover URL: https://autodiscover-s.outlook.com/autodiscover/autodiscover.xml
�[31m[-]�[0m Authentication failed: Harry.Potter@stealthdefendlab.com:Spring2020 (Invalid credentials)
�[31m[-]�[0m Authentication failed: Hermione.Granger@stealthdefendlab.com:Spring2020 (Invalid credentials)
�[32m[+]�[0m Found credentials: Ron.Weasley@stealthdefendlab.com:Spring2020
�[32m[+]�[0m Dumped 1 valid accounts to owa_valid_accounts.txt
STEP 3: Use the compromised accounts to gain further objectives
The adversary can use the compromised credentials to further their objectives. For example, they can use a compromised email account to conduct effective phishing, since not only will the sender be a real user account, but the attacker can study the messages in the mailbox to craft a strong pretext for the phishing emails.
In the example below, the adversary uses the compromised credentials to access Microsoft Teams and chat with a coworker, who readily opens the file they send — releasing malware on the coworker’s machine and enabling the adversary to pivot from a cloud to on-premises compromise.
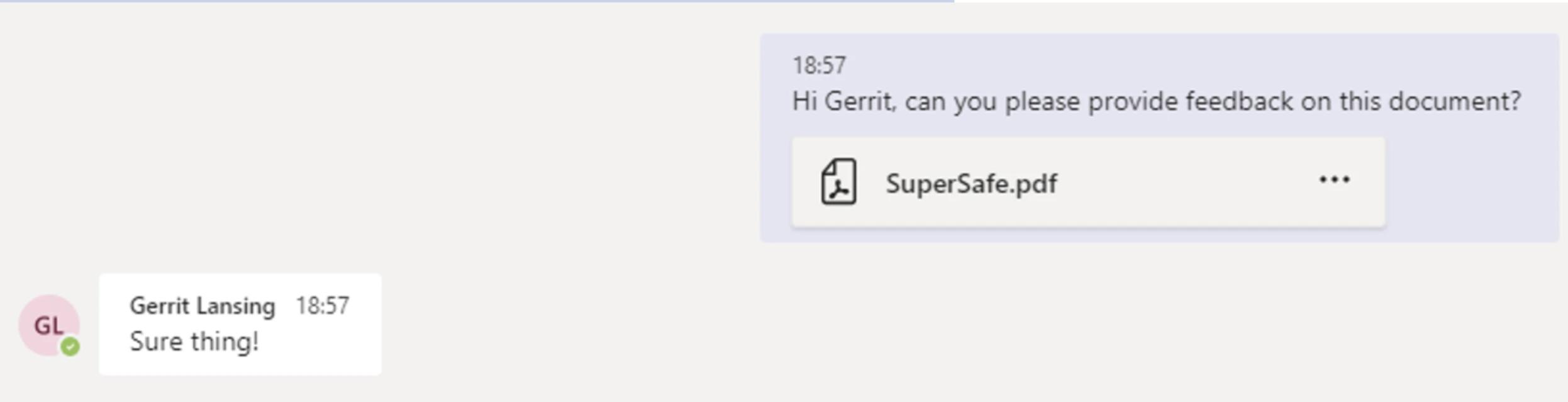
Detect, Mitigate and Respond
Detect
Difficulty: Hard
Detection of password spraying is relatively difficult: The large number of authentications and services that must be monitored results in large data sets that require complex analysis. Some service providers offer password spray detection and prevention in their own security controls, but it’s important to aggregate all applications and analyze authentication events for the signs and symptoms of password spraying — such as failed authentication attempts from the same source against multiple users.
Mitigate
Difficulty: Medium
Password spraying can be mitigated by adopting healthy authentication practices (good passwords and multi-factor authentication) and ensuring that your applications offer defenses against brute-force password attacks. NIST Special Publication 800-63B provides current guidance for strong authentication approaches and brute force defenses.
Respond
Difficulty: Low
When a suspected password spray attack is detected, take the following actions to block further activity and remediate any compromised accounts:
- Activate the incident response process and alert the incident response team.
- Block the source of the password spray at the network and/or application level to prevent future authentication attempts. If the password spray is from an internal machine, then it should be quarantined for investigation and eradication and recovery activities.
- Reset the password for any user whose password was compromised in the attack.
Share on
View related cybersecurity attacks
Abusing Entra ID Application Permissions – How It Works and Defense Strategies
AdminSDHolder Modification – How It Works and Defense Strategies
AS-REP Roasting Attack - How It Works and Defense Strategies
Hafnium Attack - How It Works and Defense Strategies
DCSync Attacks Explained: Threat to Active Directory Security
Group Managed Service Accounts Attack
Golden SAML Attack
What Is a Golden Ticket Attack? How It Works, Detection and Prevention
DCShadow Attack – How It Works, Real-World Examples & Defense Strategies
ChatGPT Prompt Injection: Understanding Risks, Examples & Prevention
NTDS.dit Password Extraction Attack
Kerberoasting Attack – How It Works and Defense Strategies
Pass the Hash Attack
Pass-the-Ticket Attack Explained: Risks, Examples & Defense Strategies
Plaintext Password Extraction Attack
Zerologon Vulnerability Explained: Risks, Exploits and Mitigation
Active Directory Ransomware Attacks
Unlocking Active Directory with the Skeleton Key Attack
Lateral Movement: What Is It, How It Works And Preventions
Man-in-the-Middle (MITM) Attacks: What They Are & How to Prevent Them
Why Is PowerShell So Popular for Attackers?
4 Service Account Attacks and How to Protect Against Them
How to Prevent Malware Attacks from Impacting Your Business
What is Credential Stuffing?
Compromising SQL Server with PowerUpSQL
What Are Mousejacking Attacks, and How to Defend Against Them
Stealing Credentials with a Security Support Provider (SSP)
Rainbow Table Attacks: How They Work and How to Defend Against Them
A Comprehensive Look into Password Attacks and How to Stop Them
LDAP Reconnaissance
Bypassing MFA with the Pass-the-Cookie Attack
Silver Ticket Attack
