NETWRIX PRIVILEGE SECURE FOR DISCOVERY (formerly SecureONE)
end administrative privilege sprawl
Thwart Cyberattacks by Removing Unmanaged Privileged Accounts
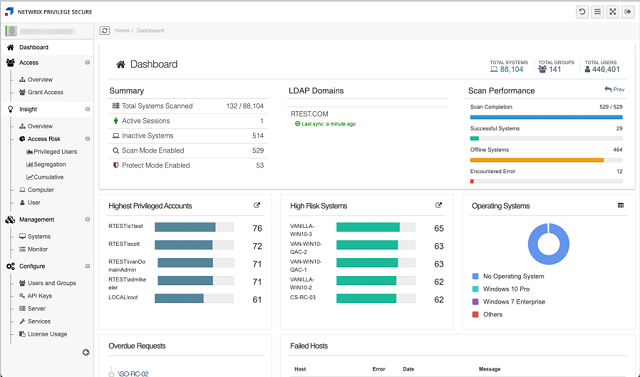
Real-time privileged account visibility
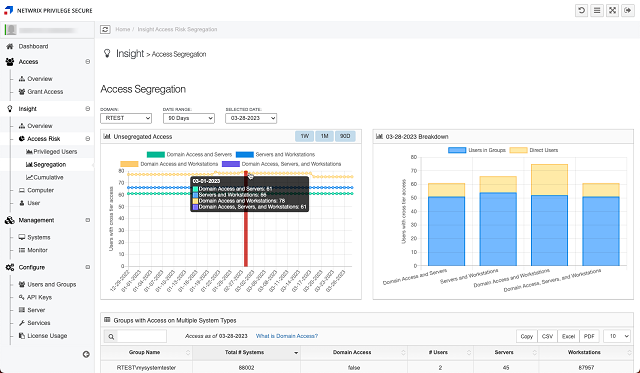
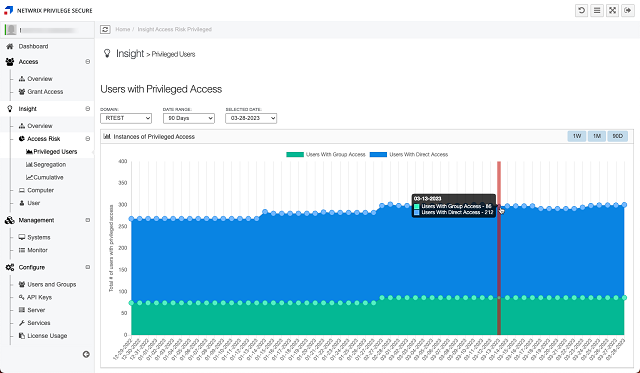
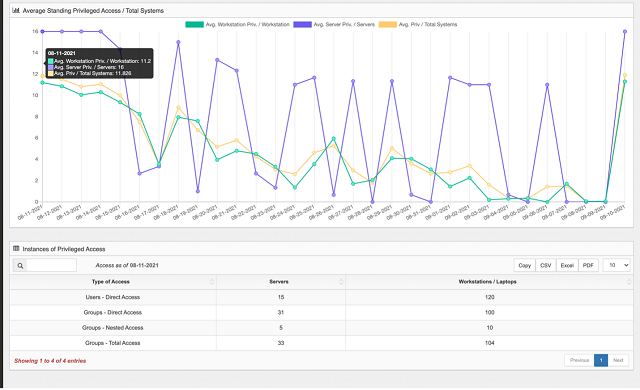
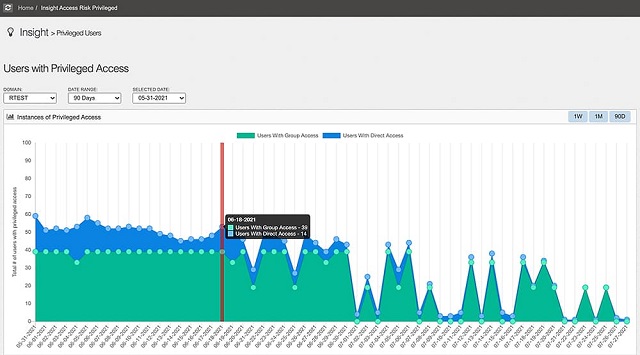
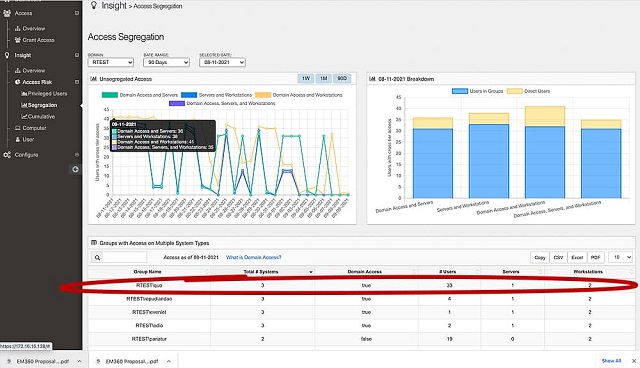
Privileged Access Risk Dashboards for Executives and Security Practitioners
Visualize, analyze, and reduce your privileged attack surface and stop lateral movement attacks
Stop Lateral Movement and Credential Theft
with Zero Standing Privilege
Netwrix Privilege Secure for Discovery thwarts attackers and malware by replacing privileged accounts
with just-in-time privileged access.
Zero Standing Privilege for all Endpoints
Remove unnecessary administrative accounts from all endpoints in a single click, slashing the risk of malware being installed or critical security settings being altered.
Just-in-Time Access
Grant admins exactly the access they need to specific endpoints, exactly when they need it and for only as long as required to complete the task.
Intelligent Session Capture
Access data about privilege user sessions through your EDR solution to enjoy context and alerts on suspicious activity such as downloading malware and accessing C&C sites.
Multi-factor Authentication
Netwrix Privilege Secure for Discovery is a single control point for all just-in-time access, making it simple to require multiple authentication factors before privileged access is granted.
Low friction Admin experience
Administrators use their own accounts, with no need for auxiliary accounts.
Attack Surface Visibility
Visualize, analyze and manage your attack surface with dashboards tailored to executives and IT pros.

DATASHEET
Netwrix Privilege Secure for Discovery (formerly SecureONE)
Find out more about how Netwrix Privilege Secure for Discovery can help you
stop privilege sprawl to slash security risks.
stop privilege sprawl to slash security risks.
Learn How Attackers Use Lateral Movement
Attacks don't begin at their destination. Attackers exploit weak points then use lateral movement to gain access to target systems and data.