safe with usb encryption
Extend your USB security policies to cover data-in-transit with USB encryption software
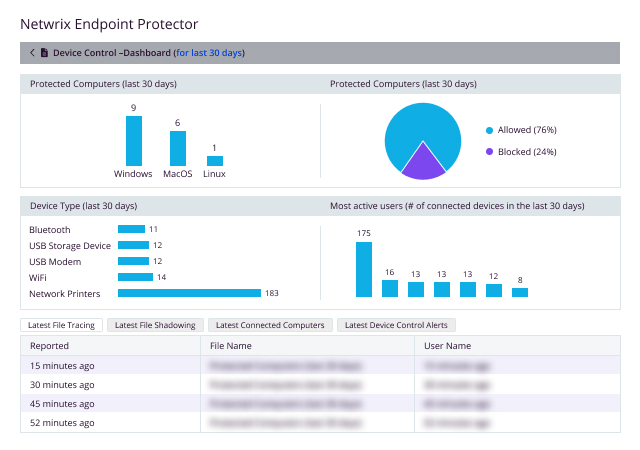
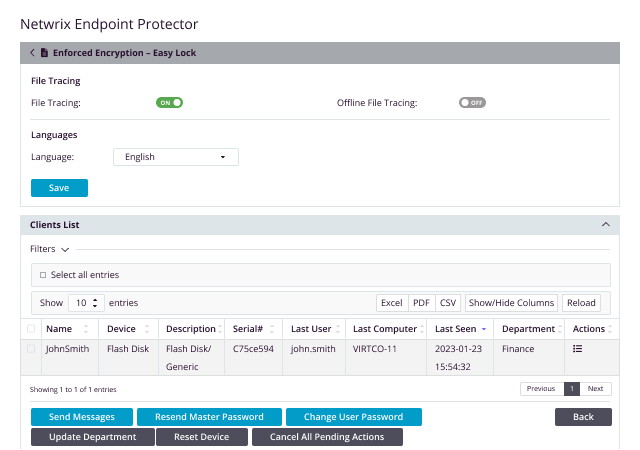
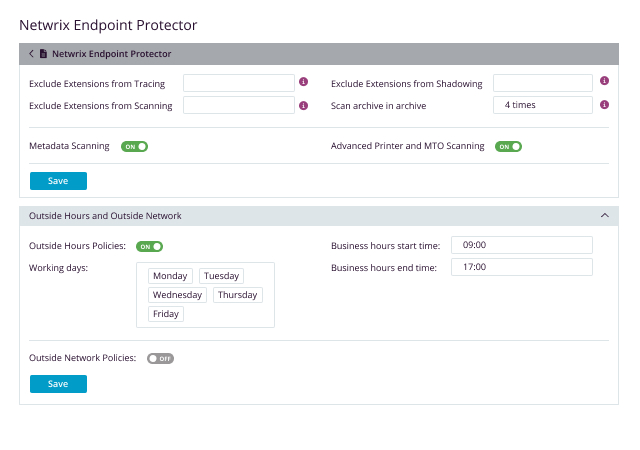
Encryption software for USB drives enhances your Device Control Policies. It replaces the need for expensive hardware-based solutions by automatically encrypting sensitive data being transferred to approved and trusted USB storage devices. Netwrix Endpoint Protector Enforced Encryption uses a FIPS 140-3 validated engine to ensure data being transferred to portable USB storage is protected from loss or theft.
Keep control of your sensitive data in transit and protect it from loss or theft
Multiple deployment options