Zerologon Vulnerability Explained: Risks, Exploits and Mitigation
Zerologon is a Windows Server vulnerability (CVE-2020-1472) that lets attackers exploit a flaw in the Netlogon protocol to bypass authentication on a domain controller. This grants them full administrative control of an entire Active Directory domain in minutes.
Attribute | Details |
|---|---|
|
Attack Type |
Zerologon (CVE-2020-1472) – Privilege Escalation via MS-NRPC |
|
Impact Level |
Critical |
|
Target |
Businesses / Government / All organizations using Active Directory |
|
Primary Attack Vector |
Network (TCP session to Domain Controller) |
|
Motivation |
Financial Gain, Espionage, Disruption, Extortion |
|
Common Prevention Methods |
Timely patching, MFA, Netlogon secure channel enforcement, EDR, SIEM, monitoring for anomalous account changes |
Risk Factor | Level |
|---|---|
|
Potential Damage |
Extremely High |
|
Ease of Execution |
High |
|
Likelihood |
High |
What is Zerologon?
Zerologon is a critical Windows Server vulnerability (CVE-2020-1472). It stems from a flaw in Microsoft’s Netlogon Remote Protocol (MS-NRPC), where the AES-CFB8 encryption uses a fixed, all-zero initialization vector. An attacker only needs basic network access to a domain controller’s Netlogon service (for example, through a VPN connection or a compromised internal machine) in order to send crafted Netlogon messages that repeatedly force authentication to succeed. Once successful, they can:
- Impersonate a domain controller.
- Reset the DC’s machine-account password, even without needing any credentials.
- From there, they can escalate straight to Domain Admin and take over the entire Active Directory domain.
This attack can compromise an entire Windows domain in minutes, which is why Microsoft assigned it CVE-2020-1472 with a CVSS score of 10.0 (Critical). The bug has been actively exploited by advanced threat groups and ransomware operators, like Ryuk, Black Basta, and Cuba. Patching this vulnerability isn't just a recommendation; it's absolutely critical.
How Does Zerologon Work?
Let’s look at each step in the Zerologon attack, understanding how an attacker moves from gaining basic network access to compromising a domain controller.
1. Establish a TCP session to the target DC
The attacker needs network access to a domain controller’s Netlogon service (TCP/445). They often gain it through phishing, stolen VPN credentials, or lateral movement from a compromised internal host.
2. Initiate an unsecured Netlogon channel
The attacker exploits a cryptographic weakness in Microsoft’s Netlogon Remote Protocol (MS-NRPC). Because the protocol’s AES-CFB8 encryption flaw that uses a fixed all-zero initialization vector (IV), the attacker repeatedly sends crafted Netlogon messages until one succeeds with a zeroed session key, causing the protocol to accept the session without proper authentication. In other words, the protocol fails to validate the session securely.
Each crafted request has roughly a 1-in-256 chance of success, so a script can achieve authentication within seconds.
3. Disable signing & sealing
After the handshake, the attacker turns off message signing and encryption. This ensures that subsequent Netlogon traffic, including password changes, travels in clear text.
4. Send NetrServerPasswordSet2
After creating an unauthenticated but (incorrectly) trusted Netlogon session, the attacker calls the NetrServerPasswordSet2 RPC function to reset the domain controller’s machine-account password to an empty string. In this way, the attacker takes ownership of the DC.
5. Leverage elevated privileges
Armed with domain controller privileges, the attacker can use tools like Mimikatz to perform a DCSync.
DCSync abuses the normal replication process that DCs use to keep their databases in sync. By impersonating another DC, the attacker requests the Active Directory database of password hashes, including those for service accounts and Domain Admins. With these hashes, the attacker can create or impersonate any account, maintain persistent access, and fully control the entire domain.
6. Optionally restore password
Some attackers reset the DC’s machine-account password back to its original value to avoid Zerologon detection while retaining access to stolen credentials.
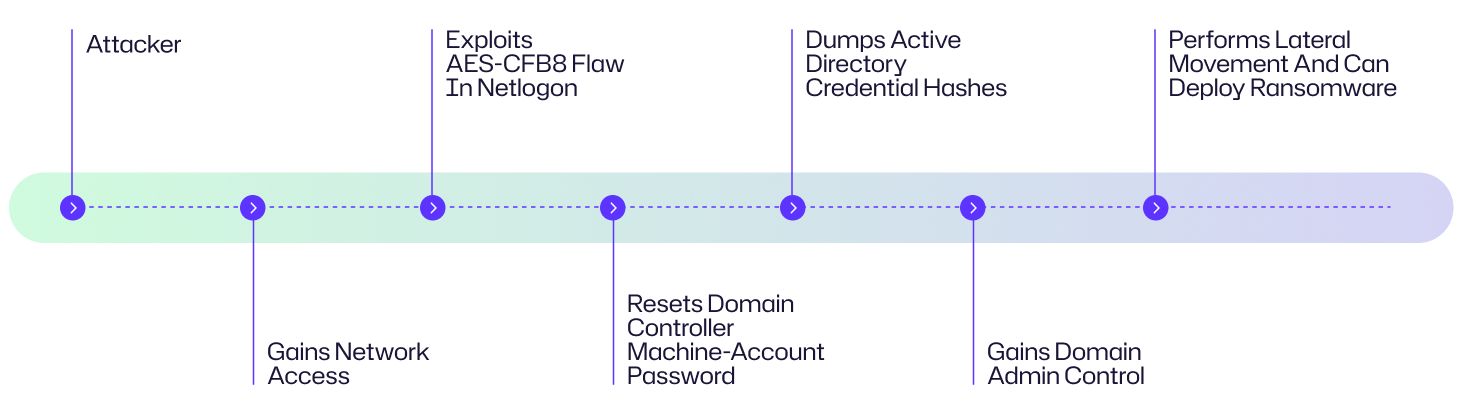
Attack Flow Diagram
The following example scenario can help you understand how a Zerologon attack may look in a real world situation.
At a mid-sized healthcare provider, a finance employee clicks a convincing phishing email, giving an attacker remote access to their workstation. From that foothold, the attacker scans the internal network and discovers an unpatched domain controller. Using the Zerologon vulnerability (CVE-2020-1472), the attacker establishes a trusted Netlogon session and resets the DC’s machine-account password to a blank value. With Domain Admin privileges now in hand, they run a DCSync attack to dump all Active Directory credential hashes, move laterally to patient-record servers, and deploy ransomware - locking down the organization’s IT operations within hours.
The diagram illustrates a typical Zerologon attack chain, from initial network foothold to complete domain compromise.
Examples of Zerologon Attacks
Since its disclosure in 2020, Zerologon has been exploited in multiple real-world breaches. Attackers have used this technique to carry out ransomware and APT operations against government, healthcare, and enterprise networks worldwide. Here are some actual cases.
Case | Impact |
|---|---|
|
Ryuk ransomware (2020) |
In late 2020, threat actors linked to Ryuk ransomware leveraged the Zerologon (CVE-2020-1472) vulnerability to encrypt entire Windows domains in under five hours. Victims included US hospitals and municipal governments. After gaining initial access, attackers exploited Zerologon to reset domain controller machine-account passwords, achieved Domain Admin privileges within minutes, and deployed Ryuk across entire networks. This led to widespread data encryption, operational disruption, and multimillion-dollar ransom demands. |
|
Cuba ransomware (2023) |
In 2023, the Cuba ransomware group used the Zerologon vulnerability (CVE-2020-1472) to deploy ransomware and exfiltrate data. Victims included critical infrastructure, financial services, and IT providers. After gaining initial access, they exploited Zerologon to reset domain controller machine-account passwords, obtained Domain Admin rights, and then deployed Cuba ransomware across networks. This led to encrypted systems, data theft, and double-extortion ransom demands, threatening to publish if ransom is not paid. |
|
Black Basta |
The Black Basta ransomware group combines Zerologon with other privilege escalation techniques for rapid takeover. After gaining initial access via phishing, social engineering, or unpatched software vulnerabilities s, the attackers elevate permissions using exploits like Zerologon and tools like Mimikatz. With domain-level control achieved, Black Basta affiliates exfiltrate sensitive data (often using rclone), disable defenses, delete backups, and encrypt systems for double-extortion. Victims include healthcare, manufacturing, and public services. As of 2024, the group has impacted over 500-700 organizations globally since its emergence in early 2022. |
|
Austin, Texas Municipal Network breach (2020) |
In mid-October 2020, the City of Austin realized that Russian state-sponsored hackers (reportedly the group “Berserk Bear”) had fully compromised the city’s wireless infrastructure, and that the attackers had been maintaining access to internal systems for months before detection. According to reports from the Microsoft Threat Intelligence Center, the attackers used exploits including Zerologon (CVE-2020-1472) to breach the network. City officials reported that critical systems were unaffected and no personal data was lost.in response, federal and state agencies, including CISA and the FBI, issued alerts and urged other municipalities to review their security and check for signs of compromise. |
Consequences of Zerologon Attacks
A Zerologon attack can wreak havoc on an organization. Once attackers gain Domain Admin access, the damage can drain financial resources and tarnish the company’s reputation.
Impact Area | Description |
|---|---|
|
Financial |
Direct costs include ransom payments, forensic investigations, emergency IT services, response and recovery expenses, and regulatory fees. Indirect costs can involve lost revenue from downtime, higher cyber-insurance premiums, and long-term investments in new security infrastructure. Public companies may also face a drop in stock value and increased cost of capital. |
|
Operational |
A compromised DC can bring down authentication services across the organization, such as logins for email, file shares, ERP, and cloud apps. It can cause domain-wide outages, halted business operations, and prolonged downtime for critical systems. When employees cannot access critical systems, production lines may stop and customer services (such as e-commerce or patient portals) can go offline for days or weeks. |
|
Reputational |
Customers, partners, and investors lose confidence when a company’s core security fails. Negative press coverage, social media backlash, and analyst downgrades can continue even after systems are restored, making it harder to win new business or keep existing clients. |
|
Legal/Regulatory |
Breaches that expose personal or regulated data (health records, financial data, government records) can trigger mandatory breach notifications and fines under GDPR, HIPAA, or CCPA. Organizations may also face lawsuits, shareholder suits, and scrutiny from regulatory bodies. |
Common Targets of Zerologon Attacks: Who is at risk?
Zerologon can threaten any organization running Active Directory, but some environments are more vulnerable than others, or tend to be more tempting for attackers.
|
Large Enterprises |
Large companies with extensive AD forests and many domain controllers often have to deal with elaborate patching and change-management processes. This makes it easier for attackers to find an unpatched DC and move laterally across the network. |
|
Government Agencies |
Public-sector institutions frequently depend on legacy systems and may have slower patch deployment cycles. Attackers count on these delays to exploit known flaws before updates are applied. |
|
Critical Infrastructure Providers |
Sectors like energy, healthcare, and transportation are high-value targets because even a brief outage can have major socio-economic and public-safety consequences. The greater the disruption, the higher the likelihood of a ransom payment. |
|
Educational Institutions |
Universities and school districts manage huge, diverse user bases, mixed device environments with unmanaged endpoints, and limited cybersecurity resources. This creates a broad attack surface that is hard to monitor continuously. |
|
Municipal and Local Governments |
These entities run with limited IT security and outdated technology. Incidents such as the Austin, Texas municipal network breach show how quickly attackers can exploit these gaps to disrupt essential services. |
|
Mixed-Platform Environments |
Organizations that connect Linux, macOS, or IoT devices to Active Directory may leave security gaps. If non-Windows systems are not fully patched or monitored, attackers can bypass security controls. |
Risk Assessment
Zerologon is a serious danger that earns the highest risk rating across the board. The vulnerability allows attackers to take over an organization’s entire AD environment with relative ease once they gain network access.
Microsoft and major security frameworks rate Zerologon (CVE-2020-1472) at the very top of their severity scales. This means that they consider Zerologon an urgent, high-impact vulnerability that requires immediate attention.
- Microsoft Security Advisory – Classified it as Critical, which is Microsoft’s highest severity rating.
- CVSS v3.1 Score – Assigned a 10.0 (Critical), the maximum possible score, reflecting its ease of exploitation and the potential for complete domain takeover.
- CISA / US Government – Added CVE-2020-1472 to the Known Exploited Vulnerabilities (KEV) Catalog and issued multiple emergency directives urging immediate patching.
Let us also consider some more risk factors:
Risk Factor | Level |
|---|---|
|
Potential Damage |
Extremely High A successful exploit grants full control of the domain controller, enabling full domain compromise, large-scale data theft, and rapid ransomware deployment. |
|
Ease of Execution |
High After gaining network access to the DC, attackers require minimal technical skills, as they can exploit Zerologon with publicly available proof-of-concept (PoC) scripts. |
|
Likelihood |
High The vulnerability has been actively exploited by ransomware groups and APT actors worldwide. |
How to Prevent a Zerologon Attack
To prevent a Zerologon attack, organizations should need a mix of timely patching, stronger authentication controls, and active monitoring.
Patch Immediately
Install Microsoft’s August 2020 and February 2021 security updates on every domain controller without delay.These patches close the Netlogon cryptographic flaw and enforce secure channel protections that stop the Zerologon exploit.
Enforce Secure RPC
Enforce secure RPC (Remote Procedure Call) connections by enabling the FullSecureChannelProtection registry key and corresponding Group Policy settings. This forces all Netlogon traffic to use encrypted, signed channels. This measure prevents attackers from downgrading the security of Netlogon connections, making it tough for them to manipulate or impersonate legitimate domain controller communications.
Restrict Non-Windows Devices
Segment or strictly control Linux, macOS, and IoT devices that authenticate to Active Directory, especially those that attempt to connect with elevated privileges or use weaker authentication methods. Unpatched or misconfigured non-Windows endpoints can undermine security controls.
Implement MFA
Enforce MFA, particularly for all privileged and service accounts. While Zerologon itself bypasses authentication, MFA acts as a vital defense after an initial compromise or for other types of attacks where credentials might be stolen. Extra verification greatly reduces the chance that stolen credentials alone can enable lateral movement or privilege escalation.
Monitor for Suspicious Activity
Track Event ID 4742 (computer account changes) and Netlogon connection events 5827–5831, which can reveal repeated failed authentications or unexpected password resets — all of which are early warning signs of an attempted exploit. By actively monitoring these and other relevant security events, organizations can quickly identify suspicious activities, detect attempted exploitations, and initiate an incident response to limit damage.
Netwrix Solutions - How Netwrix Can Help
For preventing Zerologon attacks, Netwrix's products like Netwrix Auditor can be instrumental. Auditor enable organizations to continuously monitor changes to critical settings and configurations within Active Directory, detect anomalous behaviors, and alert administrators to unauthorized changes or suspicious activity. By tracking deviations from baseline configurations and delivering real-time visibility, Netwrix Auditor helps organizations quickly spot and contain privilege-escalation attempts such as those enabled by Zerologon.
- Real-time Monitoring: Netwrix Auditor continuously audits changes to Active Directory, including domain controller configurations, security group membership, and Group Policy settings. It can send real-time alerts to administrators in the event of an unauthorized change or when critical settings are altered. In this way, admins can quickly investigate any changes that might indicate an attack.
- Anomaly Detection: Auditor’s User Behavior and Anomaly Detection (UBAD) engine uses machine learning to flag unusual account behaviors, such as sudden privilege escalations, repeated failed logons, or unexpected password resets, that could signal a Zerologon-style exploit.
- Compliance Reports: Auditor offers out-of-the-box compliance reports for frameworks like HIPAA, PCI DSS, and GDPR. These detailed reports help verify that security policies (such as timely patching, privileged-account management, and access-control changes) are strictly followed to detect and prevent unauthorized access.
Detection, Mitigation and Response Strategies
To shield your organization from a Zerologon attack, you need a layered approach: early detection of suspicious authentication attempts, rapid patching and hardening of domain controllers, and an incident response plan if compromise occurs.
Detection
For Zerologon attack detection, you should watch for specific signs of exploitation rather than just generic anomalies.
- Netlogon Debug Logs: Monitor for rapid NetrServerAuthenticate failures immediately followed by a success from the same IP.
- Packet Capture Analysis: Inspect network traces for Netlogon authentication attempts that use all-zero client credentials (00:00:00:00:00:00:00:00) returning STATUS_SUCCESS.
- Hash Analysis: Search for the well-known NTLM hash 31d6cfe0d16ae931b73c59d7e0c089c0 in the domain controller account history, which signals an empty password on the domain controller account.
- Event Log Monitoring: Windows Security Event ID 4742 is the log entry that records “A computer account was changed” in Active Directory. When you see this event with Logon Type: Anonymous (or “Anonymous Logon” as the caller), it means that someone without valid credentials successfully changed a computer-account object, indicating that a Zerologon exploitation has possibly occurred.
Mitigation
Organizations can mitigate the Zerologon risk by following certain practices, such as:
- Patch Promptly: Apply Microsoft’s August 2020 and February 2021 updates for CVE-2020-1472 to every domain controller.
- Enforce Secure RPC: Enable the FullSecureChannelProtection registry policy/setting and eliminate any policy exceptions. This forces all Netlogon traffic between domain members and domain controllers to use secure RPC with strong cryptographic authentication, blocking the all-zero credential trick used in the Zerologon exploit.
- Reduce Attack Surface: Disable or delete unused non-Windows machine accounts in Active Directory, enforce least-privilege group memberships, and turn off legacy protocols like SMBv1 and NTLMv1.
- Strengthen Identity Controls: Require multi-factor authentication (MFA) for all privileged accounts to limit impact in case of credential theft.
- Advanced Monitoring: Deploy EDR and SIEM solutions to detect anomalous authentication patterns in real time.
Response
If you suspect or confirm a Zerologon breach, act quickly and methodically:
- Isolate the Affected DC: Disconnect the compromised domain controller from the network to halt attacker activity. This includes unplugging physical network cables, blocking all network traffic to and from the DC, and disabling network interfaces.
- Reset Credentials: Change the DC’s machine account password to a long, random value.
- Rebuild Trust: Re-establish trust relationships for all affected machines and service accounts. You can use the Netdom command-line tool to reset the secure channel for each client and server, or use PowerShell scripts to automate the process.
- Rotate Privileged Secrets: Reset all administrative credentials, including the KRBTGT account, to invalidate stolen hashes and Kerberos tickets. The KRBTGT account is the "master key" for Kerberos in a domain. An attacker with its hash can create "golden tickets" to impersonate any user. As a best practice, reset the password for this account twice (with a full Kerberos ticket expiration cycle in between).
Perform Full Forensics: Conduct a thorough investigation to uncover persistence mechanisms, lateral movement, and any additional compromised assets. Look for things like unusual logon events, new administrative accounts, modified group memberships, and suspicious processes during forensics.
Industry-Specific Impact
While the Zerologon vulnerability threatens any organization running Active Directory, its may have different consequences depending on the sector. Here are examples of how it can affect critical industries.
Industry | Impact |
|---|---|
|
Healthcare |
Healthcare is an attractive target for attackers. With a ZeroLogon attack, bad actors can steal sensitive patient data, including electronic health records (EHRs). This not only compromises patient privacy but can also lead to HIPAA violations, which carry severe penalties. A breach almost definitely causes downtime that delays patient care or disrupts medical devices dependent on Active Directory authentication. And if the attacker encrypts critical systems, it can drastically disrupt hospital operations, medical device functionality, and access to patient information, which can adversely affect patient care. |
|
Finance |
In the finance sector, the consequences of a ZeroLogon attack can be crippling. By compromising a domain controller, attackers can gain access to credentials for multiple systems, from financial databases to trading platforms. This can lead to fraudulent transactions, data exfiltration, unauthorized access to customer financial data, and the manipulation of financial records. Financial institutions can also face costly regulatory penalties under PCI DSS and SOX followed by a loss of customer trust. |
|
Retail |
In the retail industry, attackers can compromise Point-of-Sale (POS) systems, stealing credit card data and other customer information. Additionally, they can deploy ransomware on supply chain networks, bringing logistics and inventory management to a halt. This could lead to a complete shutdown of business operations, significant financial losses, legal liabilities, and damage to brand reputation. |
Attack Evolution & Future Trends
Cybercriminals are getting smarter with Zerologon. They are automating attacks, using AI tools to quickly spot unpatched domain controllers, and zeroing in on old systems that cannot be updated. This means the gap between discovery and compromise is shrinking, so quick patching, constant monitoring, and tight network controls are critical.
Increased Automation
Attackers are now building Zerologon exploits right into automated ransomware toolkits and playbooks, enabling them to take over a domain in minutes. This automation means they can scan, break in, and move through the network much faster and with less technical skill than before. In many cases they strike before security teams even notice.
Tip for defenders: Focus on quick detection (Netlogon logs, packet captures) and automate patch management, so that remediation can keep pace with automated attacks.
Integration with AI-Driven Reconnaissance
Attackers are starting to pair automated scanning with AI to find vulnerable domain controllers faster. Their tools can spot clues in the network, predict which servers are unpatched or using legacy protocols, and select the highest-value domain controllers. AI even helps them choose the right timing and attack path, based on observed network behavior, making attacks more precise and harder to predict.
Tip for defenders: Improve network hygiene and monitoring. Feed EDR and SIEM with richer context so that your own analytics can spot and block these threats.
Continued Targeting of Legacy Systems
Legacy and air-gapped systems that no longer get vendor updates remain a favorite target. Attackers look for environments where exceptions or allow-lists exist for backward compatibility (for example, systems that rely on older Netlogon behaviors or unsupported OS builds). Once attackers breach those machines, they can use them as long-term footholds for repeated attacks.
Tip for defenders: If you cannot patch these systems, isolate them from the rest of the network, apply compensating controls (network segmentation, strict firewall rules, and jump servers), remove unnecessary protocols, and flag them as high-risk for strict monitoring.
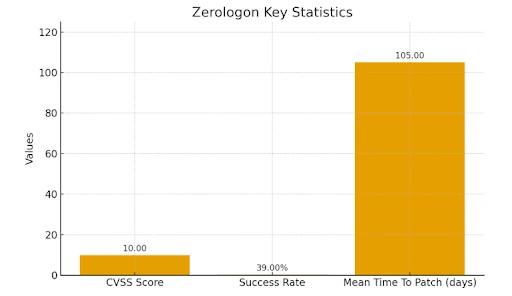
Key Statistics & Infographics
The Zerologon vulnerability (CVE-2020-1472) quickly became one of the most talked-about Windows threats because it is easy to exploit and can cause massive damage. These numbers show just how crucial it is to patch fast and stay ahead with strong, proactive defenses.
- CVSS ScoreThe vulnerability received the maximum CVSS base score of 10.0, reflecting its ease of exploitation, the ability to gain Domain Admin privileges without credentials, and the potential for complete domain compromise.
- Exploitation Success RateResearchers found that a single Zerologon attempt has about a 0.39% chance of success, meaning an attacker usually needs only around 256 tries to reset a domain controller’s machine password. Because these attempts can be scripted, compromise can occur in under a minute.
- Patch Adoption LagDespite Microsoft releasing patches in August 2020 and again in February 2021, industry studies show the average Mean Time to Patch (MTTP) for critical Windows vulnerabilities is 60 to 150 days post release. This lag gives attackers a wide window to exploit unpatched systems.
Here is a bar chart highlighting these statistics.
Final Thoughts
The Zerologon vulnerability was first uncovered in 2020 by security researcher Tom Tervoort from Secura. Microsoft released a critical patch on August 11, 2020 as part of its monthly Patch Tuesday updates. Once the fix was available, Secura published a detailed technical write-up with zerologon explained in September 2020, which brought more attention to the flaw and encouraged others to build public proof-of-concept exploits.
Zerologon is a reminder that a single overlooked flaw can endanger an entire Windows domain. Its ease of execution, critical impact, and slow patch adoption have added to its popularity, while emphasizing the need for timely patching, continuous monitoring, strong identity controls, and tested incident-response plans in place.
FAQs
Share on
View related cybersecurity attacks
Abusing Entra ID Application Permissions – How It Works and Defense Strategies
AdminSDHolder Modification – How It Works and Defense Strategies
AS-REP Roasting Attack - How It Works and Defense Strategies
Hafnium Attack - How It Works and Defense Strategies
DCSync Attacks Explained: Threat to Active Directory Security
Golden SAML Attack
Understanding Golden Ticket Attacks
Group Managed Service Accounts Attack
DCShadow Attack – How It Works, Real-World Examples & Defense Strategies
ChatGPT Prompt Injection: Understanding Risks, Examples & Prevention
NTDS.dit Password Extraction Attack
Pass the Hash Attack
Pass-the-Ticket Attack Explained: Risks, Examples & Defense Strategies
Password Spraying Attack
Plaintext Password Extraction Attack
Kerberoasting Attack – How It Works and Defense Strategies
Active Directory Ransomware Attacks
Unlocking Active Directory with the Skeleton Key Attack
Lateral Movement: What Is It, How It Works And Preventions
Man-in-the-Middle (MITM) Attacks: What They Are & How to Prevent Them
Why Is PowerShell So Popular for Attackers?
4 Service Account Attacks and How to Protect Against Them
How to Prevent Malware Attacks from Impacting Your Business
What is Credential Stuffing?
Compromising SQL Server with PowerUpSQL
What Are Mousejacking Attacks, and How to Defend Against Them
Stealing Credentials with a Security Support Provider (SSP)
Rainbow Table Attacks: How They Work and How to Defend Against Them
A Comprehensive Look into Password Attacks and How to Stop Them
LDAP Reconnaissance
Bypassing MFA with the Pass-the-Cookie Attack
Silver Ticket Attack
