Man-in-the-Middle (MITM) Attacks: What They Are & How to Prevent Them
Man in the middle attacks occur when an attacker secretly intercepts communication of two parties without their knowledge and silently extract sensitive data such as login credentials and personal data for blackmail or to do fraudulent transactions.
Man in the middle cyber attack can be devastating for individual customers and industries as they can steal sensitive data of individuals and cause reputational damage, regulatory fines or lawsuits.
Financial institutes, Healthcare industry, SMBs and Cloud services are prime targets of MITM attacks to steal financial data, patient medical history and device data.This raises the need to understand what is MITM.
Attribute | Details |
|---|---|
|
Attack Type |
Man-in-the-Middle (MITM) Attack |
|
Impact Level |
Critical |
|
Target |
All: Individuals, Businesses, Governments |
|
Primary Attack Vector |
Network, Email, Social Engineering |
|
Motivation |
Financial Gain, Espionage, Disruption, Hacktivism |
|
Common Prevention Methods |
MFA, VPN, HTTPS, Zero Trust, EDR, SIEM, Employee Training |
Risk Factor | Level |
|---|---|
|
Potential Damage |
High |
|
Ease of Execution |
Moderate to High |
|
Likelihood |
Moderate |
What Is a Man-in-the-Middle Attack?
A man-in-the-middle (MITM) attack occurs when an attacker intercepts communication between client, from where logged in user is communicating to a server without users knowing that an attacker is secretly extracting information from their session.
Main goal of MITM attack is to steal sensitive information such as credentials, credit card information, session cookies or encryption key, or to manipulate data in transit to inject malicious code on server side and sometime simply listening to private communication to gather information. Sensitive information extracted from this type of attack can be used afterwards for unauthorized transactions and ransom demands.
Session hijacking is used for impersonating valid users to gain unauthorized access to service being attacked. When a user logs in to a website, a session cookie or token is often created to remember user, so it doesn’t have to login on page-to-page navigation, attackers can intercept this session identifier and impersonate user to gain access without knowing user’s password. Phishing attacks involves tricking users into providing sensitive information on fake login pages, via fraudulent emails or messages and Malware attacks are typically viruses, worms or spywares that get installed on victim’s device such as computer or mobile to steal data or cause damage, whereas MITM attack focuses on intercepting communication between user’s application and its server to silently listen or collect sensitive information to be used later for financial gains.
MITM attacks are also known with other names such as Machine-in-the middle, Adversary-in-the-Middle (AITM), Manipulator-In-the-Middle or On-Path Attack, all these terms define same concept of unauthorized interception of communication of two parties in real-time.
How Does a MITM Attack Work?
Man in the Middle attack in cyber security is a technique used to secretly intercept communication between two parties i.e. client and server without logged in user knowing it.
Two key phases of MITM attacks
There are two phases of MITM attack, interception and decryption.
- Interception: This is the first phase, where attackers secretively position themselves between the two communicating parties like inserting a listening device in phone lines without anyone noticing it and later listening to the conversation of two or more parties.
- Decryption: Once an attacker has collected data after interception of communication, the next step is to decipher that data, especially if the communication is encrypted (over https protocol), as encrypted data is just gibberish without decryption.
Step-by-Step Breakdown
Following is the step-by-step breakdown of how attackers employe different techniques to intercept communication, extract encrypted data and apply different decryption techniques to decrypt that data for malicious activities.
Reconnaissance: Attacker identifies vulnerable networks or targets (e.g., public Wi-Fi)
In this initial Reconnaissance phase, attackers identify potential targets by scanning vulnerable networks like public wi-fi networks in cafes, airports or hotels, networks without strong passwords or routers setup with default vendor passwords and using sniffing tools like Wireshark gather more information about connected network topologies, open ports, running services and operating systems.
Interception
After getting foothold in networks via reconnaissance, attackers start placing interceptors into the communication channels of network. They can setup up fake wi-fi hotspots by mimicking a legitimate one, i.e. coffee shop’s Wi Fi Network and users connected to these hotspots have their traffic passing through attacker’s device, which silently captures the traffic.
Another intercepting technique is to employ Address Resolution Protocol (ARP) spoofing, attackers send false ARP messages to associate their device’s MAC address with IP address of legitimate device i.e. router, this tricks the network sending traffic meant for router to their device.
DNS spoofing is another technique used to trick end users who are routed to a malicious website, when they try to access a legitimate website, in this case an access request meant for DNS server is intercepted and redirected towards malicious website controlled by attackers.
Decryption
After intercepting encrypted communications, attackers use techniques like Downgrading HTTPS to HTTP (SSL stripping) where they capture users initial attempt to connect to a website on HTTPs protocol, send https request to website and rather than sending back the secure response from website, they send http response to the user tricking them to believe that secure communication is going on and in the meantime attackers are seeing plaintext data from victim side. Tools like SSL Strip are used to automate this process.
In another technique attackers use fake SSL certificates issued by rouge certificate authorities or forged themselves, tricking end user’s browser into establishing a secure connection with them instead of the real server and can view communication in decrypted form.
Data Capture
With successful interception and decryption, attackers then focus on captured data to steal valuable information such as credentials, credit card numbers, bank account details, session cookies, personal information like email, phone numbers and addresses for identity theft. Several techniques are used to log the data as it is flowing through attacker’s devices and later automated scripts are used to sweep through captured data for sensitive data.
Optional Manipulation: Alters transactions (e.g., redirect payments)
In some cases, attackers just don’t extract data, with sophisticated techniques they can manipulate online banking sessions and alter a transaction such as changing the recipient's bank account and redirect payment to their own account.
Exit: Leaves no trace, or maintains a persistent backdoor
After executing a successful MITM attack, attackers will try to cover their tracks by clearing logs on victim’s devices or servers. In some cases, they will try to install malware or create a back door to maintain long-term access to the compromised system or network for data extraction in future.
Attack Flow Diagram
MITM Attack Flow:
Example Scenarios:
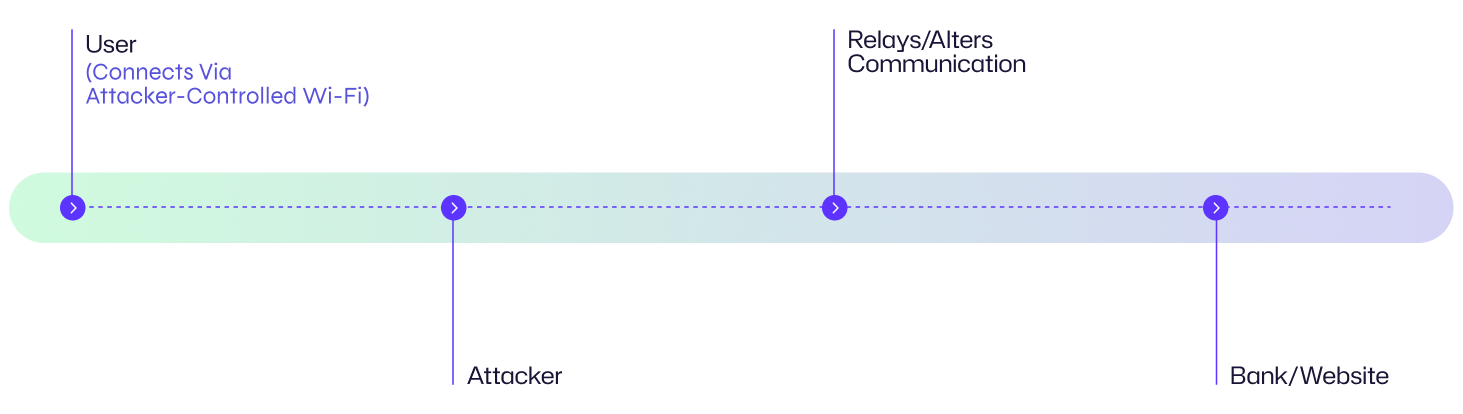
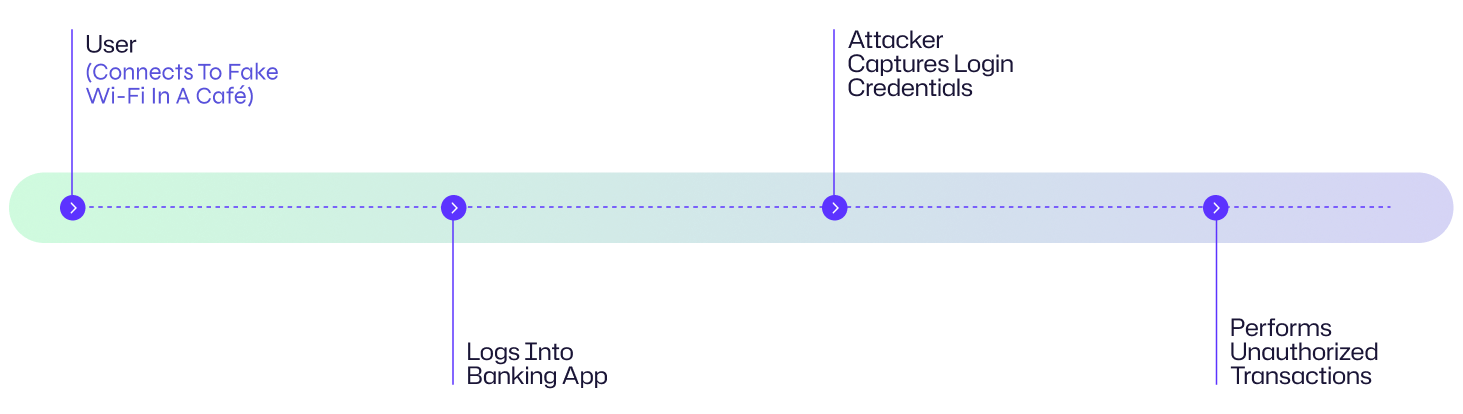
For example, David is an employee of a bank or its customer, becomes a victim to Man-in-the-Middle attack by using an unsecured Wi-Fi Network in a public café. David walks into a café “The Rock” and from the menu connects his phone and laptop to the Wi-Fi named “The Rocks” out of available some wi-fi networks like “The Rock”, “Café the Rock” and “The Rocks”, whereas only “Café the Rock” is legitimate. Now, all of David’s mobile or laptop traffic is going through a suspicious network which is controlled by hackers sitting in the café and collecting data. David logs into his social media and banking application and attackers silently collecting data and later use SSL Striping technique to decrypt the data and scrape login credentials of David for Facebook, Gmail and banking applications.
Luckily, David had multi-factor authentication enabled for banking app, however for Facebook and Gmail MFA was not enabled, attacker tried to login to banking app but wasn’t able to by-pass MFA, however login attempt to Gmail was a success by attacker and he has disabled notification first on Gmail account settings and ran SEO campaign against his account and left a bill which was served to Davids Gmail account after a month.
Examples of Man-in-the-Middle (MITM) Attacks
Below are some real-world Man in the Middle attack examples.
Case | Impact |
|---|---|
|
Equifax (2017) |
Data breach of 145M+ users due to MITM and SSL flaws. |
|
DigiNotar (2011) |
Fake SSL certificates issued; widespread data compromise. |
|
Tesla Wi-Fi exploit (2024) |
Vehicle hijacking via spoofed charging station Wi-Fi. |
|
Lenovo Superfish (2014) |
Pre-installed adware used MITM for injecting ads. |
Case | Impact |
|---|---|
|
Equifax (2017) |
In 2017 Equifax, one of the largest credit reporting agencies, suffered massive data breach where attackers exploited SSL vulnerability in their web application and conducted MITM attacks to intercept sensitive communication. Over 145 million users were affected and had their personal information compromised such as names, addresses, social security numbers, birth dates, driver’s license and credit card numbers. This led to a loss of trust and significant penalties for Equifax. |
|
DigiNotar (2011) |
in 2011, Dutch Certificate Authority (Ca) DigiNotar’s systems were compromised and attackers issued hundreds of fake certificates which were later used for MITM attacks. DigiNotar reputation was damaged and eventually lead to its bankruptcy, MITM attacks occurred on global level and affected millions of users. |
|
Tesla Wi-Fi exploit (2024) |
Security researchers demonstrated a potential exploit and its use to trick Tesla vehicles to connect to spoofed Wi-Fi network. Once connected MITM attack can allow attackers to register a new phone key which could be used for vehicle theft. |
|
Lenovo Superfish (2014) |
Lenovo added an adware software SuperFish on some of their consumer laptops, which installed a self-signed certificate which was used to inject advertisement into web pages, even on secure HTTPS connections, without user knowledge. The private key of this certificate was the same on every laptop, which allowed attackers to create their own malicious certificates and make it possible to conduct MITM attacks. The Federal Trade Commission (FTC) charged Lenovo with deceptive practices and eventually Lenovo removed SuperFish software. |
Consequences of a Man-in-the-Middle (MITM) Attack
The core danger of MITM attacks is the attacker’s ability to listen to the sensitive communication of two parties, use this sensitive data for later attacks and in some cases alter the communication to gain access to communicating parties’ systems. This not only endangers the end user but also the service providers as well. Some of the impacted areas and the nature of impacts are described below:
Impact Area | Description |
|---|---|
|
Financial |
Data theft, ransom payments, fraudulent transactions. |
|
Operational |
Downtime, service disruption, lost productivity. |
|
Reputational |
Loss of customer trust, brand damage. |
|
Legal/Regulatory |
Compliance violations (e.g., GDPR, PCI DSS), lawsuits. |
Impact Area | Description |
|---|---|
|
Financial |
Attackers can intercept and steal financial data such as credit card numbers, login credentials to bank accounts and this can lead to financial losses of individuals and organizations in case of fraudulent transactions or demand of ransom payments. |
|
Operational |
If critical systems or communication channels are intercepted during MITM attack, it can result in manipulation of network traffic or complete failure of service, impacting users’ productivity and data security, in case of service provider lots of complaints, refund demands or possible lawsuits. |
|
Reputational |
When an organization is exposed to MITM attacks and customers data is compromised it can severely damage its reputation, lost consumer trust can reduce market share or stock prices decrease and long-term damage of brand image. |
|
Legal/Regulatory |
Many industries holding customers’ private data are subjected to regulations like General data protection Regulation (GDPR), Payment Card industry Data security standard (PCI DSS) and Health Insurance Portability and Accountability (HIPPA), which require protection of sensitive data and in case of data breach, Regulatory fines and penalties for non-compliance. |
Common Targets of MITM Attacks: Who Is at Risk?
- Finance: Financial institutes and online baking are the prime target of MITM attacks due to high value financial data such as login credentials, account details and transaction details. MITM attackers can intercept login attempts, transaction data or alter fund transfer which can lead to financial problems for both end user and institute.
- Healthcare industry: MITM attacks can intercept communication between medical systems and patients to compromise confidential health records for identity theft and insurance fraud, medical history and even manipulation of medical device data.
- SMB Industry: Small and Medium businesses are targeted because they often lack strong cybersecurity infrastructure and can fall victim of MITM attacks due to less secure communication channels, vulnerable outdated networks and systems. Attacker can steal Business data, personal data of customers and gain access to internal systems.
- Cloud SaaS providers: Modern Software-as-Service (SaaS) applications handle a wide range of customers data, if they are not properly configured and secured, MITM attackers take advantage of these services to steal credentials, sensitive data files in case of cloud storage and unauthorized access to business applications.
- Industrial IoT networks: Industrial IoT networks control critical infrastructure like power plants, water treatment facilities, transportation systems and attackers can intercept data being exchanged between devices in IoT networks causing disruption of service, equipment damage or even safety hazards.
- Public Wi-Fi Users: Public Wi-Fi Networks are often poorly configured and unsecure, making them favorite targets of MITM attacks. End users connected to these infected or unsecure networks can easily compromise their personal information, browser activity and login credentials.
Risk Assessment
Risk assessment is important for organizations and for even individuals to understand the vulnerabilities susceptible to MITM attacks. Identifying weakness in communication channels, prioritizing resources and implementing effective security measures to protect sensitive data and login mechanisms.
The likelihood of MITM attack becomes significantly high when communication is being done on public wi-fi or unsecured channels without HTTPS or VPNs and on misconfigured systems or networks. Severity of MITM attacks depends on the data being compromised, however in case of financial institutes, healthcare industry and government agencies its critical because it can lead to fraud and identity theft, manipulation of medical records or devices and leaking of personal information, which can have severe consequences for the targeted organization.
MITM attacks are getting more and more sophisticated due to the availability of modern automation tools and increasing integration of AI with these tools and techniques. Making it easier for attackers to bypass traditional security measures without detection and prevention in real-time.
Common gaps contributing to rise of MITM attacks are poor endpoint security such as outdated software and lack of malware protection, unencrypted communication channels like use of HTTP instead of HTTPS and lack of training for employees to understand different phishing techniques or avoid access of company resources without protection.
How to Prevent MITM Attacks
To detect and prevent Man-in-the-Middle attack requires implementing a combination of different techniques, policies and employee’s awareness initiatives, some of the measures are described in following headings.
Use HTTPS and HSTS to enforce encrypted connections
Use HTTPS protocol to secure communication between clients and servers using SSL\TLS such as between a browser and website, encrypting data in transit and preventing attackers from listening or tempering with data. HSTS is a policy mechanism to enforce communication over HTTS only, protect against SSL striping and protocol downgrade attacks. Regularly update expired SSL/TLS certificates from trusted CA authorities, use strong TLS configurations like disable outdate versions and enforce HSTS including subdomains.
Deploy VPNs for secure remote access
Virtual private network (VPN) creates an encrypted tunnel between end user device and VPN server, routing all traffic from user to the main network via VPN and providing a secure connection for remote access. VPN provides a secure way for employees to access corporate resources from public or private networks and safeguards data interception during transit.
Implement MFA to add layers beyond passwords
Multi-Factor authentication adds an additional layer of security for end users for authentication and authorization process by presenting extra verification factors apart from credentials like authentication apps, security keys or OTP and biometric verification. This helps in reducing MITM attacks because even if an attacker has acquired your username and password, they won’t be able to bypass extra layer of verifications for authentication and access.
Zero Trust Architecture and network segmentation to reduce attack surfaces.
Zero trust is a security framework meaning “never trust, always verify”, assuming that any user account or device can be compromised, must require authentication and authorization before accessing resources. Zero trust architecture includes implementation of network segmentation by dividing network into secure independent segments, applying least privilege policy like need to access based privileges and continuous verification of user’s identity and monitoring activity patterns.
DNSSEC and encrypted DNS (DoH, DoT) to prevent spoofing.
Domain Name system (DNS) is responsible for name resolution of human-readable domains to IP addresses like google.com to 8.8.8.8 and MITM attack, DNS spoofing is used to redirect end users’ traffic to attackers’ own malicious websites or servers. Domain Name System Security Extension (DNSSEC) is a set of protocols and extensions used in this scenario that adds a layer of security to DNS queries, authenticity and integrity of DNS data. Other techniques like DNS over HTTPS (DoH) and DNS over TlS (DoT) protocols are used to encrypt connectivity between host and DNS servers.
Employee training to recognize phishing attempts.
Even with the best technical security measures, a well-crafted phishing email can trick untrained employees to compromise accounts or network segments and thus it is important to invest in employees training. Employees should be trained to recognize red flags in phishing emails such as suspicious sender addresses, urgency and requests of sensitive information, unrecognized URLs without expected domain names. Encourage employees to report suspicious emails or activities, conduct regular phishing simulation exercises to train employees and provide additional information to those who fail exercise.
Netwrix Tools To Prevent MITM Attacks
Netwrix offers a different set of tools to provide a comprehensive threat detection and mitigation mechanisms. Netwrix Privilege Secure provides functionality like Just Enough privilege (JEA), Just-in-time privileges, modular login identities to provide limited time permissions to suit diverse access scenarios. Netwrix End Point Policy Manager (formerly PolicyPak), enables administrators to protect windows end points and prevent users from installing unknown software, manage how to use removable storage and protect application settings from misconfiguration and change.
Netwrix Change Tracker product, a security configuration management and change control software which helps in securing and regulating critical IT systems. Netwrix Threat Prevention (formerly StealthINTERCEPT) generates security intelligence by actively monitoring user behavior and alerting suspicious activities, providing an additional layer of visibility and security. Netwrix Access Analyzer (formerly Enterprise Auditor) automates the collection and analysis of data such as groups, users’ membership, access details and provide comprehensive reports for different platforms such as Active Directory, Exchange server, EntraID, AWS.
Detection, Mitigation, and Response Strategies
Early Warning Signs
There are certain signs we can look for an ongoing MITM attack, such as sudden connectivity drop issues in login attempts on website or remote session to a network, browser starts showing SSL certificate warnings like expired or invalid certificate can be a sign that someone is trying to intercept communication. Websites start taking unusual time to load, some parts or sections look different than usual or distorted and if you are repeatedly being asked for login despite being logged in to site already, are probably signs of MITM attack.
Immediate Response
When we sense that there is a possibility of any kind of MITM attack going on, we should promptly take action to avoid damage in a timely manner. If a device like laptop or phone is suspected to be compromised, immediately disconnect it from network or internet by switching off wi-fi, VPN or Ethernet to stop attackers’ further infiltration in private network or device. Immediately, change all passwords or API keys or access tokens and implement multi-factor authentication on device or remote services and notify respective authorities like IT department of company, banks or financial institutions and third-party vendors or customers to take precautionary measures at their side. Once the immediate threat is contained launch a thorough investigation of network and system logs, endpoint activity and data repositories to determine the scope of attack and how it occurred, to recover any data loss and implement security measures to prevent future failures.
Long-Term Mitigation
Implement strong encryption protocols like TLS 1.3 with connection algorithms AES-GCM or chacha20 and disable older protocols sslv3 or TLS1.0 or TLS 1.1. VPNs should be sued for remote access, regularly update firewall and systems security configuration, deploy intrusion detection/prevention systems (IDS/IPS) for monitoring suspicious activities patterns in network and DNS security extensions (DNSSEC) to protect against DNS spoofing
Regularly perform penetration testing of network to assess the effectiveness of security configurations, outdated certificates and vulnerabilities in communication protocols.
Review logs from various systems like firewalls, IDS/IPS implementations, servers and endpoints and review source code of custom applications for any vulnerabilities or infectious code.
Deploy Endpoint Detection and Response (EDR) systems to monitor endpoint activity in real time, train users to recognize phishing attacks patterns, SSL certificate warnings and avoid unsecure networks.
Industry-Specific Impact
Man in the middle attack can have severe impacts on different industries, in terms of data breaches, financial frauds, reputational damages and regulatory bodies fines or penalties.
Industry | Impact |
|---|---|
|
Healthcare |
Patient data breaches, HIPAA fines. |
|
Finance |
Account takeovers, fraudulent transactions, PCI DSS. |
|
Retail |
POS data theft, supply chain vulnerabilities. |
Industry | Impact |
|---|---|
|
Healthcare |
Attackers can intercept electronic health records, personal health information and these can be used for blackmail and insurance fraud. Data breaches can lead to non-compliance with HIPPA and result in significant fines and legal actions. |
|
Finance |
MITM attacks help harvest login credentials to online banking, account details leak, fraudulent transactions and ransomware attacks which can lead to financial losses and non-compliance with PCI DSS. |
|
Retail |
Attackers can intercept and infect Point of Sales (POS) systems like retail stores that can allow them to harvest credit card details and other sensitive customer data during transactions. Attackers can further target partner organizations and suppliers of infected retailers to gain further access to bigger targets. |
Attack Evolution & Future Trends
AI and Deepfake Phishing: AI-generated emails and voices for social engineering.
Attackers are now a days using AI to generate highly convincing phishing emails, messages and voice messages for social engineering attacks to manipulate users into revealing sensitive information. These text and voice messages are being sent on social media platforms, via email or text messages to lure unsuspecting users to reveal bank account details, OTP codes, personal information, which can be used for access or fraudulent transactions.
Rise in IoT-based MITM: Exploiting smart devices and industrial networks.
IoT devices are now becoming part of regular household, businesses, industrial setup and becoming the entry point of MITM attacks as they are less secure. Devices like smart security cameras, thermostats, TV, medical devices, industrial robots, control systems can be compromised and used to intercept communication within a network.
Advanced SSL/TLS exploits: Targeting older cryptographic protocols.
Attackers are continuously looking for vulnerabilities in older cryptographic protocols and target systems which are still supporting outdated versions of SSL or TLS with known weaknesses with attacks like SSL Striping, protocol downgrade, fake certificates to bypass encryption and intercept sensitive data.
Machine-in-the-Middle Bots: Automated persistent MITM attacks.
Automated bots are developed to contentiously surveil networks for weaknesses and with help of AI infiltrate networks, establish themselves as interceptors, continuously monitor and manipulate traffic without requiring manual input from attackers. Once they have retrieved sensitive data for which they are specifically programmed, they leave the network without any trace or leaving some backdoor in place for future activity.
Key Statistics & Infographics
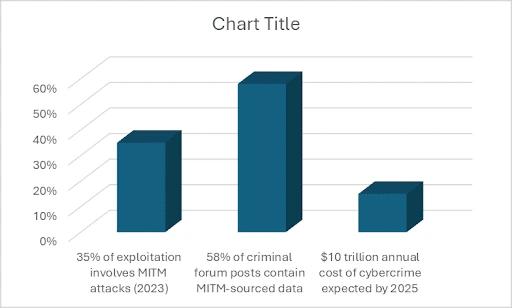
- MITM attacks remains one of the prominent sources of cyberattacks and some reports suggest that 35% of the exploitation involves MITM attacks.
- 58% of stolen data leaks on dark web forums are harvested from MITM attacks, which end up being traded and used in criminal activities.
- According to Cybersecurity Ventures, it is predicted in 2020 that the annual cost of cybersecurity measures will grow 15% per year and by 2025 it will reach 10 trillion dollars.
Final Thoughts
We have discussed in detail about man in the middle attack definition, different steps of Man in the middle attack like reconnaissance of potential weak entry points of networks, interception of communication between client and servers through compromised devices or communication channels, decryption of extracted encrypted data and lastly, data manipulation during intercepted sessions and exit without leaving traces. Main targets of MITM attacks are industries like finance, Healthcare, Retail and government agencies, and it can cause severe financial issues and regulatory penalties.
It is important to assess the security measures implemented in an organization such as data protection via encryption mechanism, secure connections with enforcement of HTTPS protocol and VPN usage, educating employees to recognize different phishing attacks and avoid unsecure networks while accessing corporate resources. Deploy network monitoring systems, enforcing MFA, implementing DNSSEC and intrusion detection and prevention systems (IDPS), perform regular penetration testing exercises to detect and prevent MITM attacks.
FAQ Section
Share on
View related cybersecurity attacks
Abusing Entra ID Application Permissions – How It Works and Defense Strategies
AdminSDHolder Modification – How It Works and Defense Strategies
AS-REP Roasting Attack - How It Works and Defense Strategies
Hafnium Attack - How It Works and Defense Strategies
DCSync Attacks Explained: Threat to Active Directory Security
Golden SAML Attack
What Is a Golden Ticket Attack? How It Works, Detection and Prevention
Group Managed Service Accounts Attack
DCShadow Attack – How It Works, Real-World Examples & Defense Strategies
ChatGPT Prompt Injection: Understanding Risks, Examples & Prevention
NTDS.dit Password Extraction Attack
Pass the Hash Attack
Pass-the-Ticket Attack Explained: Risks, Examples & Defense Strategies
Password Spraying Attack
Plaintext Password Extraction Attack
Zerologon Vulnerability Explained: Risks, Exploits and Mitigation
Active Directory Ransomware Attacks
Unlocking Active Directory with the Skeleton Key Attack
Lateral Movement: What Is It, How It Works And Preventions
Kerberoasting Attack – How It Works and Defense Strategies
Why Is PowerShell So Popular for Attackers?
4 Service Account Attacks and How to Protect Against Them
How to Prevent Malware Attacks from Impacting Your Business
What is Credential Stuffing?
Compromising SQL Server with PowerUpSQL
What Are Mousejacking Attacks, and How to Defend Against Them
Stealing Credentials with a Security Support Provider (SSP)
Rainbow Table Attacks: How They Work and How to Defend Against Them
A Comprehensive Look into Password Attacks and How to Stop Them
LDAP Reconnaissance
