How to Find Illicit Applications in Microsoft Entra ID
Native Solution vs. Netwrix Auditor for Microsoft Entra ID
Netwrix Auditor for Microsoft Entra ID
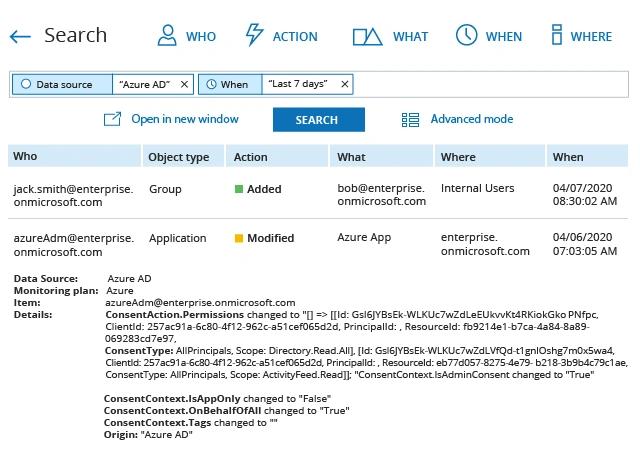
- Run Netwrix Auditor → Navigate to “Search” → Click “Advanced mode” if it is not automatically selected → Set up the following filter: “Data source” "Equal" “Azure AD”.
- Refine your search results to applications only by adding the filter “Object Type” = “Application”, and exclude any whitelisted application by adding the following filter:
Filter = “What”
Operator = “ Not Equal”
Value = “App Name”
Native Solution
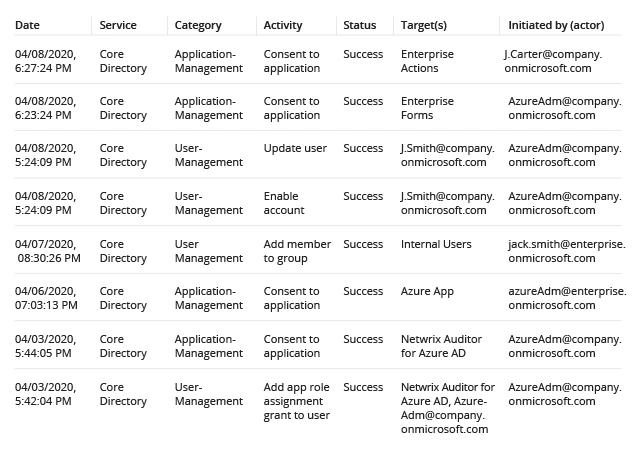
- From the Azure portal menu, select Monitoring, or search for and select Monitoring from any page.
- Select Audit Logs.
- Filter the report to show only application-related events by picking "Application Management" in the Category column’s search section. The Target(s) column shows the application name.
- Review the event details in the Details tab at the bottom of the page.
Note: If you want to filter out whitelisted applications, you will have to pull the log data into a CSV file and analyze it manually, since the native event log filters don’t have an exclude function.
Detecting Illicit Application Activity in Microsoft Entra ID — A Better Way
Enterprise application libraries today are often bursting at the seams, thanks to both organic growth and user demand. But lack of proper insight and management often means that unwanted applications sneak into the mix, and employees often download their own software, bypassing IT altogether.
These unauthorized applications pose a real threat to both security and compliance. For instance, by default, Azure allows any user to give any application from the app gallery permission to access their data — which opens the door for third-party apps to read your business-critical or regulated content.
Therefore, it’s wise to carefully monitor your Azure logs for suspicious applications. With manual tools, that can be a tough job. The Azure Audit log stores data on directory-by-directory basis, so to find data across several Azure directories, you’ll have to run the same search multiple times. Plus, the native event log filters don’t have an exclude function, so to filter out whitelisted applications, you’ll have to pull the log data into a CSV file and analyze it manually.
With Netwrix Auditor, on the other hand, you can search across all your audit data at once and quickly filter out irrelevant audit log records to focus on what’s really important. Moreover, you can easily set up alerts that notify you about suspicious activity in time to prevent a breach. Netwrix Auditor also enables you to store your log data cost-effectively for over 10 years for compliance and investigation purposes.
Share on
