Come verificare i permessi utente in Active Directory
Netwrix Auditor for Active Directory
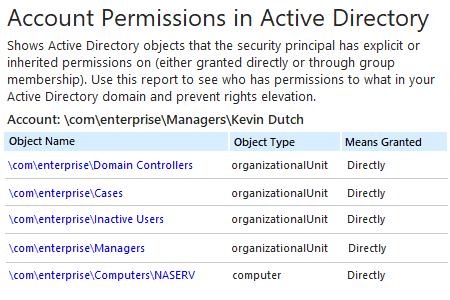
- Esegui Netwrix Auditor → Vai alla sezione "Rapporti" → Espandi la sezione "Active Directory" → Vai a "Active Directory - Stato nel Tempo" → Seleziona "Permessi Account in Active Directory" → Clicca su "Visualizza".
- Specificare i valori per i filtri qui sotto e fare clic su "Visualizza Report":
- Percorso UNC dell'account
- Mezzi Concessi
- Permessi
- Per salvare il rapporto, clicca sul pulsante "Esporta" → Scegli un formato dal menu a tendina → Clicca "Salva".
Scopri di più su Netwrix Auditor for Active Directory
Auditing nativo
- Apri il Powershell ISE → Crea un nuovo script con il seguente codice, specificando il nome utente e il percorso per l'esportazione → Esegui lo script.
Import-Module ActiveDirectory
# Array for report.
$report = @()
$schemaIDGUID = @{}
# ignore duplicate errors if any #
$ErrorActionPreference = 'SilentlyContinue'
Get-ADObject -SearchBase (Get-ADRootDSE).schemaNamingContext -LDAPFilter '(schemaIDGUID=*)' -Properties name, schemaIDGUID |
ForEach-Object {$schemaIDGUID.add([System.GUID]$_.schemaIDGUID,$_.name)}
Get-ADObject -SearchBase "CN=Extended-Rights,$((Get-ADRootDSE).configurationNamingContext)" -LDAPFilter '(objectClass=controlAccessRight)' -Properties name, rightsGUID |
ForEach-Object {$schemaIDGUID.add([System.GUID]$_.rightsGUID,$_.name)}
$ErrorActionPreference = 'Continue'
# Get a list of AD objects.
$AOs = @(Get-ADDomain | Select-Object -ExpandProperty DistinguishedName)
$AOs += Get-ADOrganizationalUnit -Filter * | Select-Object -ExpandProperty DistinguishedName
$AOs += Get-ADObject -SearchBase (Get-ADDomain).DistinguishedName -SearchScope Subtree -LDAPFilter '(objectClass=*)' | Select-Object -ExpandProperty DistinguishedName
# Loop through each of the AD objects and retrieve their permissions.
# Add report columns to contain the path.
ForEach ($AO in $AOs) {
$report += Get-Acl -Path "AD:\$AO" |
Select-Object -ExpandProperty Access |
Select-Object @{name='organizationalunit';expression={$AO}}, `
@{name='objectTypeName';expression={if ($_.objectType.ToString() -eq '00000000-0000-0000-0000-000000000000') {'All'} Else {$schemaIDGUID.Item($_.objectType)}}}, `
@{name='inheritedObjectTypeName';expression={$schemaIDGUID.Item($_.inheritedObjectType)}}, `
*
} # Filter by single user and export to a CSV file.
$User ='Username'
$report | Where-Object {$_.IdentityReference -like "*$User*"} | Select-Object IdentityReference, ActiveDirectoryRights, OrganizationalUnit, IsInherited -Unique |
Export-Csv -Path "C:\data\explicit_permissions.csv" -NoTypeInformation
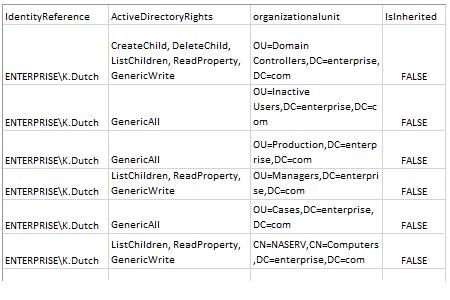
- Avvia MS Excel e apri il file generato dallo script.
Rapporto di esempio:
Riduci le aree di superficie di attacco controllando continuamente i rapporti dei permessi utente di Active Directory
Per una corretta gestione di Active Directory e una maggiore sicurezza, le migliori pratiche richiedono che i permessi siano ereditati tramite l'appartenenza a gruppi di Active Directory piuttosto che assegnati esplicitamente. Tuttavia, garantire che i diritti di accesso seguano questo principio può essere una sfida. Gli amministratori IT devono regolarmente visualizzare i rapporti sui permessi degli utenti di Active Directory che dettagliano come i permessi sono stati concessi per poter rimuovere quelli che sono stati assegnati esplicitamente, oltre a lavorare con i proprietari dei dati per rimuovere gli utenti dai gruppi che concedono loro permessi non necessari per il loro lavoro quotidiano. Una regolare revisione e pulizia dei permessi aiuta a minimizzare il rischio di abuso di privilegi e violazioni dei dati. Ma creare rapporti basandosi su uno strumento di reporting come PowerShell e rivedere un output criptico è sia dispendioso in termini di tempo che soggetto a errori.
Netwrix Auditor for Active Directory supera i limiti dello scripting PowerShell fornendo un rapporto completo che elenca tutti gli oggetti a cui un determinato utente ha accesso e se i diritti sono stati concessi tramite l'appartenenza a un gruppo o esplicitamente. È possibile approfondire facilmente per maggiori dettagli, come ad esempio quali permessi esatti l'utente ha su un oggetto specifico.
Condividi su
