Netwrix Auditor: The Network Device Monitoring Tool
Unprotected devices are an open gateway for would-be attackers. Track router, switch, and firewall changes with comprehensive network device monitoring.
Read their Stories
Trusted by





































































Network device monitoring software that keeps you in the know
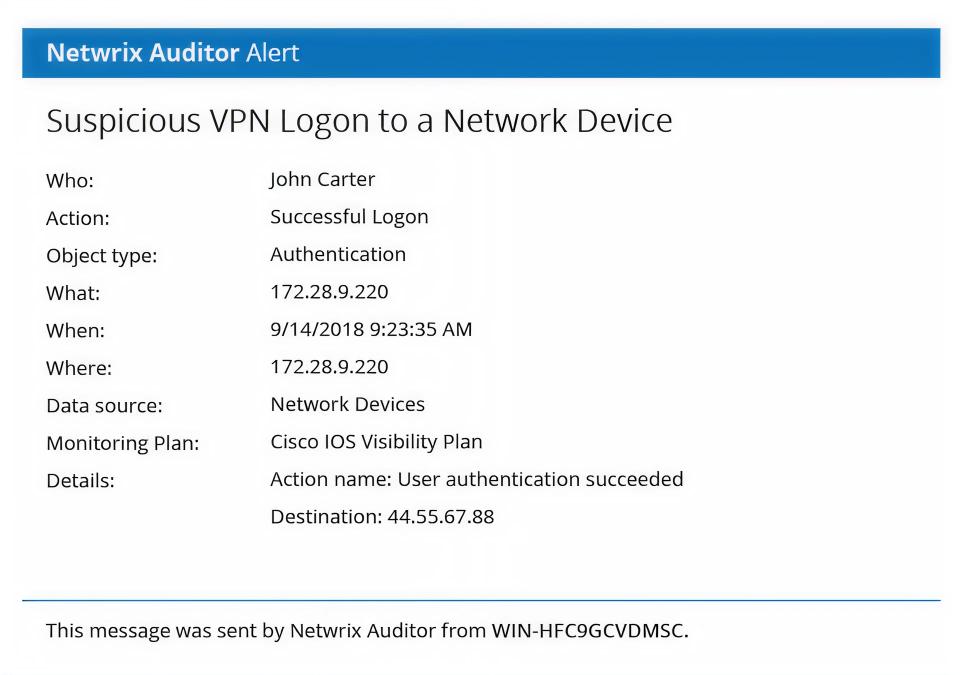
Detect security threats
Spot and investigate improper configuration changes, suspicious logon attempts, scanning threats, and more.
Pass audits with ease
Slash audit preparation time with hard evidence proving that your security controls are working as expected.
Boost IT team productivity
Minimize time and effort with our network device monitoring tool for network devices, incident investigation, and routine reporting.
Cross-platform integration
Centralize network monitoring alongside Active Directory, databases, and cloud systems for unified security visibility.
Capabilities
Get instant visibility with network device monitoring tools that track every logon, change, and update — so you’re never left scrambling
Ready to get started?
Solutions
Go beyond single-threat protection. Secure every angle with Netwrix solutions.






