Hafnium Attack - How It Works and Defense Strategies
StrategiesHafnium refers to a state-linked adversary group that exploited zero-day vulnerabilities in on-premises Microsoft Exchange servers to gain remote code execution, deploy web shells, and exfiltrate email and sensitive data. By scanning for internet-exposed Exchange services and leveraging unpatched vulnerabilities, attackers achieved broad compromise for espionage and follow-on activity.
Attribute | Details |
|---|---|
|
Attack Type |
Exploitation of Exchange Server zero-days / web-shell deployment / data exfiltration |
|
Impact Level |
Very High |
|
Target |
On-premises Microsoft Exchange servers (enterprises, governments, service providers) |
|
Primary Attack Vector |
Internet-exposed Exchange services (OWA, EWS, Autodiscover), unpatched vulnerabilities, automated scanning |
|
Motivation |
Espionage, data theft, persistence; follow-on ransomware in some incidents |
|
Common Prevention Methods |
Patch Exchange immediately, remove/limit external exposure, EDR/IDS, web-shell detection, network segmentation, threat hunting |
Risk Factor | Level |
|---|---|
|
Potential Damage |
Very High — mailbox/data theft, domain access, downstream disruption |
|
Ease of Execution |
Medium — requires scanning and exploitation but many exploit tools were widely shared |
|
Likelihood |
Medium to High for orgs with internet-facing, unpatched Exchange instances |
What is the Hafnium attack?
“Hafnium” describes a series of attacks (and an actor) that targeted on-premises Microsoft Exchange servers using multiple zero-day vulnerabilities. Attackers scanned for internet-reachable Exchange instances, exploited flaws to achieve remote code execution, deployed web shells for persistent access, and exfiltrated mail and sensitive data.
How Does the Hafnium Attack Work?
Below is a high-level breakdown of common stages observed in Hafnium-style intrusions.
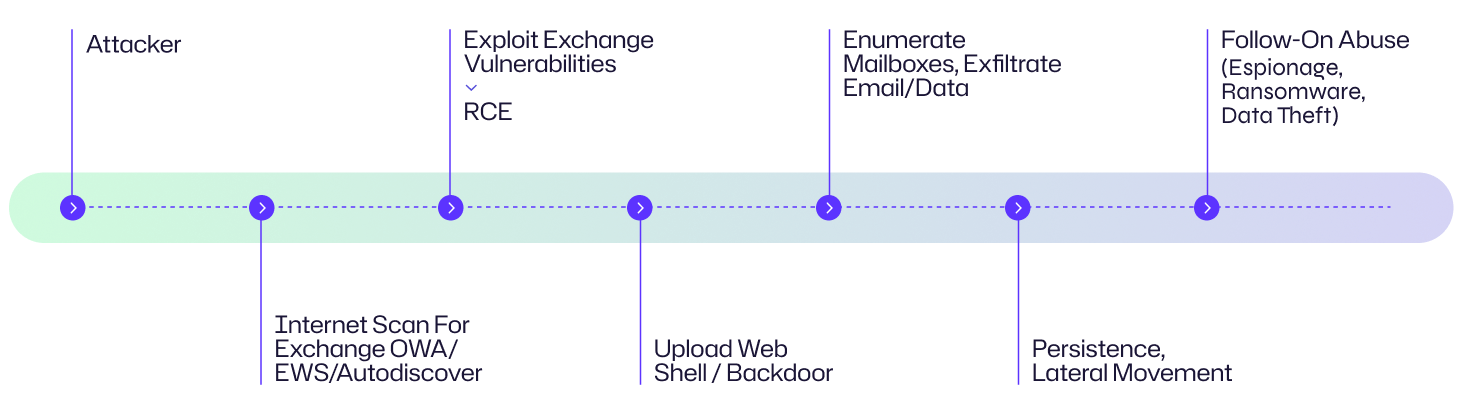
1. Reconnaissance — scan for vulnerable Exchange servers
Adversaries scanned the internet for Exchange endpoints (OWA/EWS/Autodiscover) and cataloged reachable instances and versions. Automated scanners and public exploit code accelerated discovery.
2. Exploit Exchange vulnerabilities
Using server-side vulnerabilities, attackers achieved unauthenticated or authenticated remote code execution on the mail server, enabling arbitrary command execution or file drops (web shells).
3. Deploy web shells/backdoors
Attackers uploaded lightweight web shells into Exchange web directories (IIS) to gain persistent remote command execution via HTTP(S). Web shells blend into normal web traffic and are stealthy.
4. Post-exploitation: account & mailbox access
With code execution and web shells, attackers enumerated mailboxes, read and exfiltrated email, harvested credentials, and searched for high-value data via EWS, PowerShell, or direct file access.
5. Establish persistence & lateral movement
Adversaries created additional backdoors, added accounts, modified mail rules for exfiltration, and attempted lateral movement to domain controllers, file servers, and other infrastructure.
6. Clean up or enable follow-on operations
Some intrusions enabled ransomware or opportunistic exploitation by other actors; others maintained covert espionage access for months.
✱ Variant: Supply-chain and secondary exploitation
Compromised Exchange servers with web shells are often re-used by other threat actors for different campaigns (ransomware, cryptomining). Secondary exploitation amplifies impact across victims.
Attack Flow Diagram
Example: Organization Perspective
An attacker scans for exposed Exchange servers at AcmeCorp, exploits an unpatched server to run commands, installs a web shell, downloads executive mailboxes, exfiltrates attachments containing sensitive IP, and creates scheduled tasks to maintain access. Weeks later a second actor uses the same server to deploy ransomware.
Examples & Real-World Patterns
Case | Impact |
|---|---|
|
Mass exploitation of Exchange zero-days (early 2021) |
Thousands of orgs compromised, web shells detected worldwide, large-scale mailbox theft and follow-on attacks. |
|
Post-exploit secondary use |
Other groups opportunistically used compromised Exchange servers for malware, ransomware, or cryptomining. |
Consequences of a Hafnium-style Compromise
Compromise of Exchange servers is devastating because mailboxes often contain sensitive PII, IP, legal data, and account reset links.
Financial Consequences
Data theft, extortion demands, regulatory fines, and remediation & incident response costs can be very high, especially if financial records or customer data are exposed.
Operational Disruption
Mail service outages, forced takedowns, long recovery windows (rebuilding servers, reissuing certs, rotating credentials), and disruption to business operations.
Reputational Damage
Loss of trust from customers/partners and negative publicity when confidential communications or data leaks occur.
Legal and Regulatory Impact
Breaches involving personal data may trigger GDPR, HIPAA, or other regulatory actions, audits, and fines.
Impact Area | Description |
|---|---|
|
Financial |
Ransom, remediation, fines |
|
Operational |
Service outages, rebuilds, lost productivity |
|
Reputational |
Customer trust erosion, partner concerns |
|
Legal |
Compliance investigations, breach notifications |
Common Targets: Who is at risk?
Internet-facing Exchange servers
Unpatched or unsupported Exchange instances
Organizations with high volumes of sensitive email
Legal, healthcare, government, research entities
Service providers and MSPs
Multi-tenant setups increase blast radius
Environments lacking EDR/web-shell monitoring
No visibility into IIS/Exchange folders
Risk Assessment
Risk Factor | Level |
|---|---|
|
Potential Damage |
Very High — direct access to communications and account-reset vectors. |
|
Ease of Execution |
Medium — exploits existed and scanning was automated; exploit payloads required. |
|
Likelihood |
Medium — high where Exchange servers are exposed and unpatched. |
How to Prevent Hafnium-style Attacks
Key controls include timely patching, reducing exposure, web-shell detection, and threat hunting.
Patch & Update
Apply vendor patches immediately for Exchange and related components. Decommission unsupported Exchange instances and migrate to supported platforms where appropriate.
Reduce Exposure
Block OWA/EWS/Autodiscover from the public internet if not required. Use VPN, reverse proxies, and WAFs to protect Exchange endpoints.
Hardening & Least Privilege
Harden IIS and Exchange configurations, disable unnecessary services, and limit privileges of service accounts.
Detect & Remove Web Shells
Scan web directories for suspicious files and signatures, monitor modified timestamps, and restrict write permissions to web directories.
Improve Authentication & Secrets Hygiene
Rotate certificates and service credentials after suspected compromise. Require MFA for administrative access and use strong unique credentials.
Visibility & Threat Hunting
Deploy EDR and network monitoring, hunt for IoCs such as newly added files in Exchange directories, unusual mailbox exports, and suspicious outbound connections.
How Netwrix Can Help
The Hafnium attacks highlight how quickly an Exchange compromise can escalate into a full Active Directory takeover. Netwrix Identity Threat Detection & Response (ITDR) helps organizations spot unusual authentication, privilege abuse, and persistence techniques in real time, so attackers can be contained before they move deeper into your environment. By securing the identity layer, ITDR closes the door on Hafnium-style intrusions and strengthens your overall security posture.
Detection, Mitigation and Response Strategies
Detection
- Alert on creation or modification of files under Exchange web directories (IIS \inetpub\wwwroot\*).
- Monitor for unusual PowerShell, w3wp.exe, and other processes executed by the Exchange service account.
- Detect unusual mailbox exports or bulk EWS activity.
- Network detection: uncommon outbound connections to staging/exfil hosts, DNS anomalies, or large POST/GET requests to web shells.
Response
- Isolate affected servers immediately and preserve forensic evidence.
- Remove web shells and backdoors only after capture and analysis; attackers often leave multiple persistence mechanisms.
- Rotate credentials and certificates used by Exchange, service accounts, and admin users.
- Perform a thorough hunt across the estate for lateral movement, mailbox exfiltration, and secondary footholds.
- Rebuild compromised servers from known good images where possible.
Mitigation
- Reissue user and service credentials and reset privileged accounts.
- Reinforce perimeter controls and patch management.
- Engage IR and communications for regulatory notifications and customer outreach.
Industry-Specific Impact
Industry | Impact |
|---|---|
|
Healthcare |
PHI exposure and disruption to patient communications. |
|
Legal |
Exposure of privileged legal communications and case data. |
|
Government |
Risk to sensitive interagency communications and national security. |
|
Service Providers |
Amplified compromise across customers/tenants. |
Attack Evolution & Future Trends
- Rapid weaponization of disclosed vulnerabilities — public exploit code increases speed and scale of exploitation.
- Web-shell reuse and secondary exploitation by other threat actors.
- Shift to cloud email services reduces on-prem exposure, but hybrid setups retain residual risk.
- Greater focus on MSP & supply-chain risks where provider compromise affects customers.
Key Statistics & Infographics (suggested telemetry)
- Time from vulnerability disclosure to mass exploitation (measure in your telemetry).
- Number of exposed Exchange endpoints in your external scan.
- Count of web-shell detections or suspicious IIS file modifications.
Final Thoughts
Hafnium incidents show how critical timely patching, reducing public exposure of enterprise services, and rapid threat hunting are. Exchange servers are high-value targets; prioritize patching, reduce external access, and monitor for web shells and post-exploit activity.
FAQs
Share on
View related cybersecurity attacks
Abusing Entra ID Application Permissions – How It Works and Defense Strategies
AdminSDHolder Modification – How It Works and Defense Strategies
AS-REP Roasting Attack - How It Works and Defense Strategies
Kerberoasting Attack – How It Works and Defense Strategies
DCSync Attacks Explained: Threat to Active Directory Security
Golden SAML Attack
What Is a Golden Ticket Attack? How It Works, Detection and Prevention
Group Managed Service Accounts Attack
DCShadow Attack – How It Works, Real-World Examples & Defense Strategies
ChatGPT Prompt Injection: Understanding Risks, Examples & Prevention
NTDS.dit Password Extraction Attack
Pass the Hash Attack
Pass-the-Ticket Attack Explained: Risks, Examples & Defense Strategies
Password Spraying Attack
Plaintext Password Extraction Attack
Zerologon Vulnerability Explained: Risks, Exploits and Mitigation
Active Directory Ransomware Attacks
Unlocking Active Directory with the Skeleton Key Attack
Lateral Movement: What Is It, How It Works And Preventions
Man-in-the-Middle (MITM) Attacks: What They Are & How to Prevent Them
Why Is PowerShell So Popular for Attackers?
4 Service Account Attacks and How to Protect Against Them
How to Prevent Malware Attacks from Impacting Your Business
What is Credential Stuffing?
Compromising SQL Server with PowerUpSQL
What Are Mousejacking Attacks, and How to Defend Against Them
Stealing Credentials with a Security Support Provider (SSP)
Rainbow Table Attacks: How They Work and How to Defend Against Them
A Comprehensive Look into Password Attacks and How to Stop Them
LDAP Reconnaissance
Bypassing MFA with the Pass-the-Cookie Attack
Silver Ticket Attack
