Lateral Movement: What Is It, How It Works And Preventions
Lateral movement in cyber security is a technique to navigate through network to get a hold of critical data from a compromised location i.e. stolen credentials or infectious mail attachment. Attackers silently achieve objectives like data extraction, encrypting sensitive data, damage infrastructure for financial gain and espionage. Multiple techniques are employed to reduce the attack surface such as strict Identity and Access Management (IAM) policies, regular review of privileges, deploying Automated threat monitoring systems to remediate malicious user activity patterns in timely manner.
Attribute | Details |
|---|---|
|
Attack Type |
Lateral Movement |
|
Impact Level |
High / Critical |
|
Target |
Businesses, Governments, Critical Infrastructure |
|
Primary Attack Vector |
Network, Stolen Credentials, Exploited Vulnerabilities |
|
Motivation |
Financial Gain (Ransomware), Espionage, Data Theft, System Sabotage |
|
Common Prevention Methods |
Zero Trust, MFA, Network Segmentation, Endpoint Detection & Response (EDR), SIEM, User Behavior Analytics (UBA) |
Risk Factor | Level |
|---|---|
|
Potential Damage |
Critical |
|
Ease of Execution |
Medium to High |
|
Likelihood |
High |
What Is Lateral Movement?
Lateral Movement is the set of techniques used by cyber attackers to gain initial access to a network to further navigate and spread in sub-systems, applications and data for malicious activity. Instead of directly attacking the target system, attackers move sideways through the network, evaluating valuable targets, escalating privileges and positioning themselves for larger attack.
The purpose of lateral movement during an attack is to expand the control and reach within compromised network. This phase allows attackers to locate and access high-value targets such as sensitive data stores, critical servers like domain controllers, escalate privileges such as gain administrative control, maintain long-term undetected access in network and prepare for the final attack like data extraction, ransomware deployment or disrupt critical services.
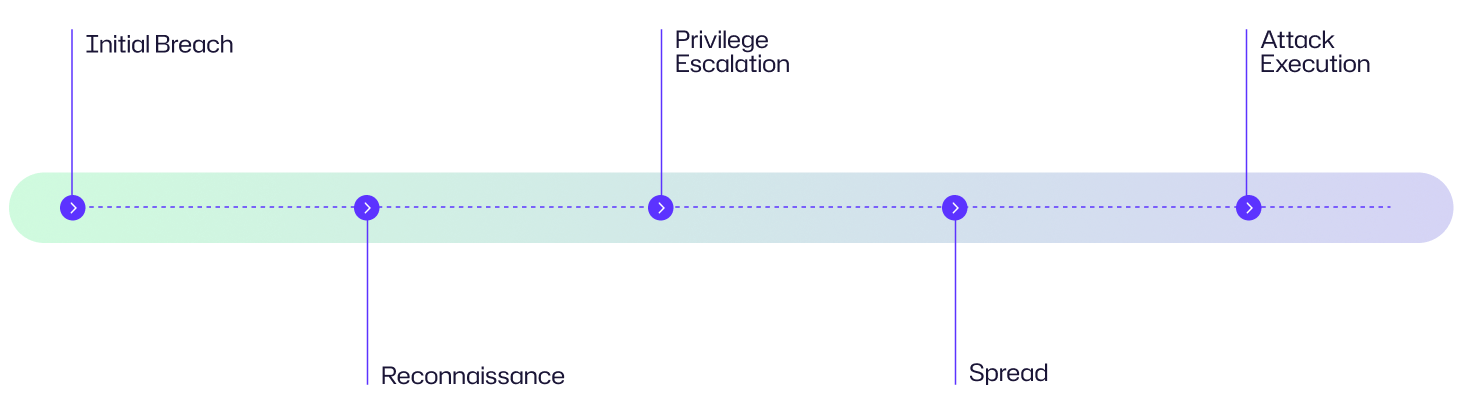
- Initial Access: Attackers gain access to network through phishing emails, malware infections or with stolen credentials.
- Reconnaissance: once attackers get access, they explore network to understand its structure and try to identify assets like weak system and user accounts, servers and applications.
- Privilege Escalation: after initial exploration, attackers try to gain higher level access by stealing credentials and exploiting known or zero-day vulnerabilities of applications and systems.
- Lateral Movement: using tools like remote desktop protocol, PowerShell and other administrative utilities attacker move from one system to another, expanding their control and reach.
- Final Attack: After mapping the network and gaining sufficient access in sub-systems, attackers execute their final attack by stealing sensitive data, deploying ransomware or destroying critical services or systems.
How Does Lateral Movement Work? (Step-by-Step Breakdown)
Lateral movement is a multi-phase process used by attackers after they are successful in their initial breach of network security to navigate and gain total or partial control of network and its subsystems to achieve their malicious goal. A more detailed breakdown of each phase is given below.
Initial Access
There are different techniques used by cybercriminals to penetrate network defense and gain access to at least one system.
Phishing Emails
There are different types of phishing attacks used to entrap people to reveal sensitive information.
Spear phishing
Targeted emails are designed to trick specific individuals into revealing credentials or clicking malicious links and attachments to infect systems.
Whaling
A specific type of attack targeting high-profile individuals like CEOs or CFOs, to gain access to their privileged accounts.
Business Email Compromise (BEC)
Attackers impersonate trusted entities, i.e. vendors, business partners, colleagues via email to reveal sensitive information or transfer of funds.
Malware Infections
Malware like keyloggers, Remote Access Trojans (RATs) are deployed via email attachments, infected USB devices, legitimate sites ads with infected executable code to open a backdoor into target network.
Brute-Force Attack
Automated tools that try different combinations of username and password, are used to systematically attack services that are exposed to the internet like Remote Desktop Protocol (RDP), VPNs or Web applications.
Software Vulnerabilities
Attackers identify and exploit known vulnerabilities in operating systems, applications, web servers or network devices, which are not yet patched. Zero Day exploits, for which no patch is yet available, are highly effective in gaining unauthorized access.
Internal Reconnaissance
After the initial access, attackers start the next phase of internal Reconnaissance, gathering information silently about network and connected systems like Network Mapping, identifying user accounts with elevated privileges, locating critical servers, shared folders, databases and evaluating different security configurations.
Common tools used in this exercise are as follows
- Command prompt and PowerShell to run in-memory scripts to evaluate system and network configurations.
- PSExec, a command-line tool used for executing commands on remote systems to evaluate accessibility and privileges levels.
- NetStat, a command line utility used to gather information about network connections, listening ports and established connections.
The focus of reconnaissance phase is to identify accounts with administrative privileges like domain admins, default accounts with known default passwords, locate system or shared folders, database servers or ERP solutions with sensitive information.
Credential Dumping & Privilege Escalation
This phase involves extraction of credentials, username and passwords from system memory, registries or files with specially designed tools like keyloggers and Mimikatz.
Keyloggers silently capture keystrokes and steal sensitive data like username and password or answers to security questions for MFA. Mimikaz specially is used for extracting plaintext passwords, Password Hashes, PINs and Kerberos tickets and target windows components like LSASS, WDigest and Kerberos.
Once credentials are acquired, different techniques are employed to escalate privileges, on local systems or on domain level exploiting weak policies and misconfigurations. Attackers exploit known OS vulnerabilities, services or scheduled tasks with privileged accounts and impersonate user access token of a privileged account.
Lateral Movement & Spread
After getting privileged credentials, attackers further expand the lateral movement to navigate different systems in network to locate sensitive information repositories for their final attack. Techniques include.
Pass-the-Hash (PtH)
Pass-the-Hash (PtH) is a clever technique used by attackers to authenticate to remote system without needing plaintext passwords. When any user authenticates on a windows system, their password gets converted into a cryptographic hash and used for further verification. Attackers extract these password hashes using special tools for their malicious activity and this technique is effective bypassing different detection mechanisms.
Pass-the-Ticket (PtT)
Pass-the-Ticket (PtT) is used for Domain joined machines, when a user logs into a domain joined machine with Kerberos authentication a Ticket is assigned to it for repeated authentication without re-entering credentials. That ticket is used in Pass-the-Ticket attack and used to access different resources on network impersonating user without knowing their password.
Remote Desktop protocol (RDP)
Remote Desktop protocol (RDP) allows remote access to devices and is commonly used protocol. Hijacking, active remote services sessions due to misconfigured RDP settings or credentials reuse is an effective way of lateral movement and it provides a full graphical interface as the attacker is sitting in front of that system.
Final Attack Execution
After the successful execution of different phases of lateral movement, attackers execute their goals like deploying ransomware, extracting sensitive information or sabotaging critical infrastructure.
Ransomwares are malwares which encrypt files on local drives or admin shares on network, making the data unusable without the decryption key. After encryption, attackers typically leave ransom notes on the affected system demanding payment to release the decryption key and in some sophisticated attacks, backups are also deleted or encrypted to prevent restoration without payment.
Sensitive data exfiltration is another common goal of attackers to steal corporate data for extortion or sell it on darknet markets. After achieving certain privileged access and identifying data sources in network, attackers start sending data to their servers, cloud storage or removable storage derives and cover their track. This data can be financial records, employees or customer private data and intellectual property like source code or product designs.
Sabotaging of critical infrastructure is mostly involved in gaining control of operational technology of power grids, hospitals and government institutions to spread disruption and denial of service. Once privileged access is established in these target organizations malwares are deployed or configuring equipment for permanent damage in such a way that intended operation or service of organization is delayed or shut down completely.
Attack Flow Diagram
Examples of Lateral Movement
Case | What happened |
|---|---|
|
SolarWinds Breach (2020) |
Attackers exploited the Orion software update, moving laterally to compromise U.S. government agencies. |
|
NotPetya (2017) |
Used credential theft and exploit propagation, crippling businesses worldwide. |
|
WannaCry (2017): |
Spread rapidly using the EternalBlue exploit, affecting over 200,000 systems. |
Case | What happened |
|---|---|
|
SolarWinds Breach (2020) |
Attackers exploited Orion software update mechanisms to gain access to different organization’s infrastructure, including US government agencies. Initially, attackers compromised SolarWind’s software building setup and added malicious code in Orion updates, as they were digitally signed it appeared legitimate to customers and once, they got installed in target systems, malicious code opened backdoor communication with attacker’s servers and with lateral gained further foothold. |
|
NotPetya (2017) |
NotPetya attack originated from Ukraine in 2017, initially its believed that Software M.E.Doc update mechanism was compromised and Mimikatz like technique was used for credential harvesting. After getting entry in networks, Pass-the-Hash (PtH), External blue exploit, PsExec tool abuse and self-replicating methods were employed to use lateral movement to spread quickly and it globally infected systems, causing billions of dollars loss. |
|
WannaCry (2017): |
It was a ransomware attack, which exploited Eternal blue exploit of windows Server block version 1 (SMBv1) protocol and spread quickly across the globe infecting over 200,000 systems. Eventually, Microsoft released a patch for Eternal blue vulnerability, and its impact was contained. |
Consequences of Lateral Movement
Sophisticated cyber-attacks with lateral movement allowed attackers to damage organizations in several ways, some of them are as follows:
Impact Area | Description |
|---|---|
|
Financial |
Ransom payments, regulatory fines, revenue loss due to downtime. |
|
Operational |
Business disruption, data encryption, locked systems. |
|
Reputational |
Loss of customer trust, brand damage, loss of partnerships. |
|
Legal/Regulatory |
GDPR fines, PCI DSS violations, HIPAA non-compliance. |
Impact Area | Description |
|---|---|
|
Financial |
Attackers may encrypt data across multiple systems and demand ransom for decryption key, data breach results in regulatory fines, remediation cost is separate and ultimately revenue loss. |
|
Operational |
System lockouts, services outages and loss of critical data can cause severe operational problems for organizations from day-to-day basis and sometimes for even weeks or months. |
|
Reputational |
Data breaches and security incidents are nightmares for organization’s reputation and consequently lead to loss of customers, brand damage, loss of partnerships and decreased stock values. |
|
Legal/Regulatory |
Organizations handling personal data of general public can face severe fines according to reginal laws like EU General Data protection Regulations (GDPR), in banking industry regulations like Payment Card Industry Data Standard (PCI DSS) and HIPPA Non-Compliance in United States regarding patient health information comes in effect in case of data breaches. |
Most common targets
Enterprises & Corporations
Large organizations are attractive targets because they often hold high-value data including financial data, intellectual property and customers records.
Financial institutions like Banks, investment firms and payment processors are targeted due to their direct access to funds and customer’s financial information.
Retail and Ecommerce are lucrative for various reasons i.e. Point of sale systems hold credit cards information, Customer databases contain personal and financial information and supply chain networks can allow access to partner organizations.
Government & Critical Infrastructure
Government Agencies are targets of rival state sponsored or lone cyber criminals for extraction of classified data, espionage purposes and to sabotage government operations and services.
Energy sectors such as Power grids, water treatment plants, gas pipelines are also target of criminal minded attacks with foreign funding or for namesake. These facilities use operational technologies and industrial control systems, require sophisticated techniques and planning to disrupt the operations.
Healthcare & Hospitals are targeted for patient’s data which can be sold online, ransomware attacks and denial of critical services are also common as critical data in patient history is important in this industry, and they are forced to meet attackers demands to stay operational.
SMBs & Supply Chains
Small & Medium Businesses (SMBs) are also frequently targeted as in most cases they have weaker security defenses and fewer resources dedicated to cybersecurity and become steppingstones to reach partner enterprises.
Attackers often target third-party vendors and suppliers of large organizations to gain access to target organizations, SolarWinds incident is an example of this scenario.
Cloud Environments & Remote Workforces
As more and more organizations are moving towards cloud-based solutions, attackers are also targeting cloud-based networks and lateral movement allows threat actors to hop around multi-tenant cloud environments to gain access to sensitive data stored in cloud.
Remote workforce of organizations with weak authentication policies or credentials using VPNs, Remote desktop and cloud-based web portals are prime targets of attackers as entry points to move in corporate networks and subsystems.
High-Privilege Accounts & IT Administrators
System administrators and IT personnels with privileged access are the prime targets of attackers to gain unrestricted lateral movement in network and remain undetected.
Service accounts and privileged user accounts are used for different applications and services for different third-party software and if compromised by attackers can be used for deep infiltration without detection.
Risk Assessment
Risk assessment associated with lateral movement attack is extremely important to identify vulnerabilities, implement security controls, and develop effective strategies to prevent, detect and respond to any potential intrusions. Without any planning or thorough assessment, any security gap will remain undetected and exposure to devastating attacks will be high without knowledge.
Lateral movement is not an edge-case scenario nowadays, it’s a highly common tactic used by attackers to gain further access of valuable assets, once they breached the security defense.
The potential severity of lateral movement is level critical because after initial breach by accident or entrapment, if attackers can easily move around networks and subsystems, they can quickly escalate access privileges and can take total control of the enterprise systems without detection and can do a lot of damage in terms of finance or disruption of critical systems.
Detection difficulty is also high in case of lateral movement as it mimics legitimate and normal network activity using compromised accounts and standard tools. Identifying lateral movement requires sophisticated monitoring tools, skilled security analytics and a deep understanding of network traffic patterns.
How to Prevent Lateral Movement
A proactive and layered approach should be adopted by organizations security teams to implement security measures strategically to prevent, detect and mitigate lateral movement.
Zero Trust Security – Assume every user and device is a potential threat.
Zero trust security is a security philosophy operating on principle of “never trust, always verify”. Implement strict Identity and Access Management (IAM) by strong authentication and authorization mechanisms for every user and devices attempting to access resources. Continuous verification of users, devices and applications with re-authentication and re-authorization and configuring access token with time limitation. Create segmentation in network to limit and segregate access of users, devices and applications to restrict undetected movement if one segment is compromised.
Multi-Factor Authentication (MFA) – Blocks unauthorized logins.
Multi-factor authentication adds an extra layer of security to the login process, forcing end users to provide two or more verification factors. Enforce multi factor authentication on all users and service accounts and add context awareness in this process to consider user’s location, device and resource being accessed during the login process.
Network Segmentation & Micro-Segmentation – Restricts lateral movement paths.
Network segmentation involves dividing networks into distinct, isolated segments with restricted access for specific set of resources i.e. users, devices, applications. Micro-segmentation takes this approach to the next level by creating even smaller segments with granular control for specific workflows between resources. This can be achieved by identifying critical assets, data flow and map legitimate communication paths between only essential resources. Define security zones, implement physical and logical segmentation with the help of VLANs, firewalls, SDN (software defined Networks) and implement the least privileges for network access.
Endpoint Detection & Response (EDR) – Identifies suspicious activity on devices.
Endpoint Detection & Response (EDR) solutions continuously monitor and analyze endpoint activities, collect data on processes and network connections, file changes and can generate alerts or automated responses. EDR solutions can analyze activities patterns, detect malicious pass-the-hash attempts, remote process injections and abnormal tool usage. They also provide insights on post incident analysis, helping security teams track attacker’s movements and identify potential compromised systems.
Security Information & Event Management (SIEM) – Logs & detects anomalies.
Security information and Event Management (SIEM) systems collect and analyze security logs and event data from different sources within systems such as network devices, servers, application endpoints and security tools to detect suspicious patterns and potential security incidents that can point out lateral movement and help in security threat hunting. SIEM can detect generate alerts in real-time based on configured Indicators of compliance (IoCs), provide forensic insights of failed login attempts, unusual network traffic from specific location or system and privileged access attempts.
User Behavior Analytics (UBA) – Flags unusual login patterns.
User Behavior analytics (UBA) monitors and establishes user activity patterns like login times, duration, device location, resource usage and then analyzes any deviation from the pattern to flag suspicious activity such as lateral movement. UBA assign risk scores to anomalous activities, helping security team prioritize alerts and can be integrated with SIEM and other security tools.
How Netwrix Endpoint Policy Manager Helps to Lateral Movement
Netwrix Endpoint Policy Manager is an enterprise solution that provides organizations with solutions for managing user privileges on organization devices. This can help in preventing lateral movement and ransomware attacks because even after gaining the initial access, attackers find a totally locked down system with no points, direction to move and gain further access.
Netwrix Endpoint Policy Manager policies can prevent users from installing any software apart from essential allowed software, manage how users can use removeable storage and prevent from changing security configurations. It can restrict end-user’s interaction with applications, browsers settings and java applets, restrict them from reconfiguring them, achieve compliance and reduce vulnerability by certainty that group policy settings are configured properly.
Detection, Mitigation, and Response Strategies
Early Warning Signs of an Attack
Keep an eye on unusual login activities from unfamiliar locations or outside of regular working hours. Sudden increase in failed login attempts and surge in network traffic can point to brute force attacks, malware communication, botnet activity or on-going lateral movement. Attempts to access critical services or backend servers, especially from unknow IP addresses and attempts of large data transfer, require immediate response to investigate anomalies.
Immediate Response Steps
Start isolating affected systems by disconnecting from main network, via firewall rules or physically unplugging cables, disable compromised credentials or force reset passwords and enable MFA on compromised accounts. Examine logs on compromised systems, fire walls, authentication logs and analyze endpoint activities to trace the movements of attackers. Use specialized forensic tools to analyze presence of malware, backdoors or any persistence mechanisms.
Long-Term Mitigation Strategies
Implement long-term mitigation strategies like principle of least privilege, ensuring users only have access to resources which are required to perform their tasks and regularly review access permissions. Conduct routine penetration testing to identify vulnerabilities that can be abused for potential attacks and address them promptly with patching and configuration changes.
Industry-Specific Impact
Industry | Impact |
|---|---|
|
Healthcare |
Patient data leaks, ransomware targeting hospital systems. |
|
Finance |
Banking fraud, unauthorized transfers, insider threats. |
|
Retail |
POS malware, supplier breaches affecting supply chains. |
Industry | Impact |
|---|---|
|
Healthcare |
Cyber attackers in the healthcare industry are commonly after patient data such as medical history, diagnosis, treatment plans and personal details, in result healthcare institutes can not only face financial problems but also regulatory issues like HIPPA non-compliance can result in legal and financial penalties. Ransomware attacks can disrupt critical services like access to patients records and lab reports in ERP, configurations of critical devices can be changed to malfunction and forcing institute to pay in urgency of system restoration. |
|
Finance |
In the financial sector, attackers usually exploit vulnerabilities in online banking systems for unauthorized transfer of funds, deploy phishing techniques to deceive employees to reveal sensitive information and then can use it to gain access to network. This not only results in financial loss but also regulatory fines and scrutiny from regulatory bodies due to weak security measures. In the case of financial institutes like stock markets or investment banks, undetected access to sensitive information can lead to insider trading, stock prices manipulation and can be difficult to distinguish from legitimate and malicious activity due to the scale of transactions. |
|
Retail |
Lateral movement meaning in context of cyber-security for retail industry is to help attackers breach multiple Point of Sale (POS) systems across organization, collect customers payment card information and this leads to widescale data breaches. Lateral movement techniques can be used to exploit supply chain systems, targeting vendors and partner organizations which can be used for further infiltration to disrupt operations or extract data. |
Attack Evolution & Future Trends
Just like any other technology, cyberattacks are evolving and adopting sophisticated techniques to remain persistent and navigate networks undetected.
AI-Driven Lateral Movement: Attackers using AI for automated reconnaissance and faster privilege escalation.
Attackers are using Artificial Intelligence and machine learning algorithms to automate various stages of lateral movement to mimic legitimate user behaviors, complex and faster reconnaissance techniques to find software and network exploits with easy privileged escalation without detection.
Cloud-Based Attacks: Lateral movement within cloud environments and hybrid networks.
With infrastructure getting moved to cloud or hybrid implementation, attackers are also targeting cloud infrastructures such as AWS, Azure and GCP. In these environments, misconfiguration, stolen credentials or access tokens, vulnerable API’s, weak Identity and Access Management (IAM) policies are easy entry points and to move around cloud services.
Deepfake Phishing: AI-generated impersonations used to steal credentials.
AI-generated deepfake such as audio or video messages are used to impersonate higher authority and to deceive employees into sharing credentials or approving authorized access to critical services or resources.
Supply Chain Exploits: Attackers moving laterally through third-party vendors.
This approach involves gaining access to target organizations through a third-party vendor’s compromised resources which have access to the target organization, such as software updates. Once, backdoor is established in the target organization, attackers can move laterally in network and these attacks are virtually silent as target organization has less control over vender’s environment
Key Statistics & Infographics
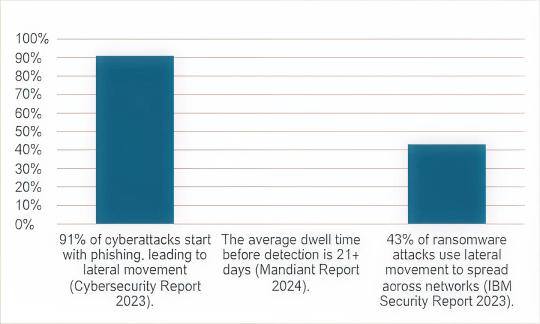
According to cybersecurity reports, 91% of cyberattack starting points are phishing techniques, tricking individuals into revealing credentials or downloading malware unknowingly.
According to Mandiant report 2024, the average dwell time of attackers moving around network without detection is 21+ days which is alarming in nature as some of the data exfiltration techniques leave no traces and this interval provides ample time for disrupting any critical service or system.
IBM security report 2023 suggests that nearly half of the attacks (43%) use lateral movement techniques to amplify the impact and reach as many systems as possible and data repository before initiating final attack.
Final Thoughts
We have discussed lateral movement definition and different phases in detail such as initial access with phishing attack or infected attachments, Reconnaissance of network segments after gaining initial access, escalating privileges using known vulnerabilities to gain further control of system, lateral movement to find critical data repositories and executing final attack to extract sensitive data and disrupt critical services for ransom or permanent damage. Lateral movement attacks focus differently on various industries such as financial institutes attackers are after unauthorize fund transfer, credit card frauds and sensitive data manipulation for insider trading. In Healthcare industry patient data is the goal or to deploy malware for ransom, in retail businesses attackers deploy malicious code at point-of-sale terminals to extract customers data or target small businesses to gain access to their partner enterprises.
A proactive approach with a combination of strategies and tools is the best way to prevent and detect lateral movement in case attackers gain access to one segment of the network. Implement multi-factor authentication for every user and service accounts with segregation of network and employing least privileges access principle. Deploy End point detection and response (EDR) solutions, regular monitoring of failed login attempts, unusual data flows, thorough weekly analysis of logs and regularly testing different configurations for privileges escalation scenarios.
FAQ's
Share on
View related cybersecurity attacks
Abusing Entra ID Application Permissions – How It Works and Defense Strategies
AdminSDHolder Modification – How It Works and Defense Strategies
AS-REP Roasting Attack - How It Works and Defense Strategies
Hafnium Attack - How It Works and Defense Strategies
DCSync Attacks Explained: Threat to Active Directory Security
Golden SAML Attack
What Is a Golden Ticket Attack? How It Works, Detection and Prevention
Group Managed Service Accounts Attack
DCShadow Attack – How It Works, Real-World Examples & Defense Strategies
ChatGPT Prompt Injection: Understanding Risks, Examples & Prevention
NTDS.dit Password Extraction Attack
Pass the Hash Attack
Pass-the-Ticket Attack Explained: Risks, Examples & Defense Strategies
Password Spraying Attack
Plaintext Password Extraction Attack
Zerologon Vulnerability Explained: Risks, Exploits and Mitigation
Active Directory Ransomware Attacks
Unlocking Active Directory with the Skeleton Key Attack
Kerberoasting Attack – How It Works and Defense Strategies
Man-in-the-Middle (MITM) Attacks: What They Are & How to Prevent Them
Why Is PowerShell So Popular for Attackers?
4 Service Account Attacks and How to Protect Against Them
How to Prevent Malware Attacks from Impacting Your Business
What is Credential Stuffing?
Compromising SQL Server with PowerUpSQL
What Are Mousejacking Attacks, and How to Defend Against Them
Stealing Credentials with a Security Support Provider (SSP)
Rainbow Table Attacks: How They Work and How to Defend Against Them
A Comprehensive Look into Password Attacks and How to Stop Them
LDAP Reconnaissance
Bypassing MFA with the Pass-the-Cookie Attack
Silver Ticket Attack
