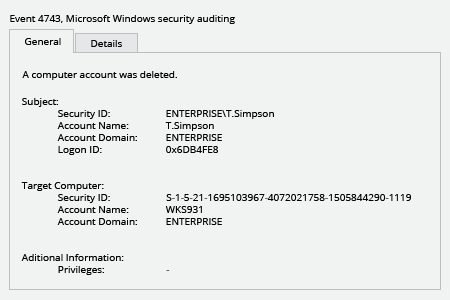
Improper deletion of a user account can cause serious problems for an organization. Users whose computer accounts have been deleted won’t be able to log into IT systems using their domain authentication. If they are already logged in, they will have trouble accessing their email, shared folders, SharePoint and other resources. In addition to this loss of productivity, IT staff have to spend time investigating why an authentication error has occurred. To avoid these issues, it’s vitally important to detect the deletion of computer accounts in a timely manner.
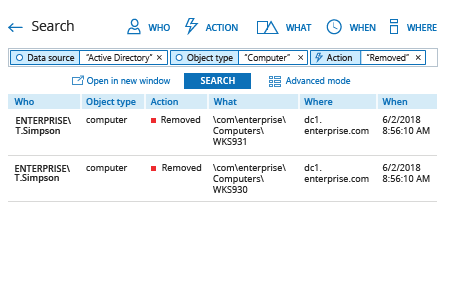
Netwrix Auditor for Active Directory enables complete visibility into activity in Active Directory and Group Policy by providing actionable audit data about access events and changes. Customizable email alerts notify IT administrators when anyone deletes computer accounts, so they can respond quickly to unwanted deletions and prevent the problems that arise when the system could not authenticate a user. Audit reports contain actionable details, such as who deleted which computer account and when and where the change occurred, so admins can investigate and prevent similar problems from happening in the future.