In order to monitor AD group membership changes with PowerShell:
- Open the PowerShell ISE.
- Copy and run the following script, adjusting the timeframe in the PowerShell code:
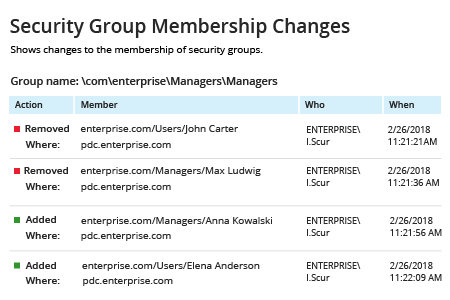
# Get domain controllers list
$DCs = Get-ADDomainController -Filter *
# Define timeframe for report (default is 1 day)
$startDate = (get-date).AddDays(-1)
# Store group membership changes events from the security event logs in an array.
foreach ($DC in $DCs){
$events = Get-Eventlog -LogName Security -ComputerName $DC.Hostname -after $startDate | where {$_.eventID -eq 4728 -or $_.eventID -eq 4729}}
# Loop through each stored event; print all changes to security global group members with when, who, what details.
foreach ($e in $events){
# Member Added to Group
if (($e.EventID -eq 4728 )){
write-host "Group: "$e.ReplacementStrings[2] "`tAction: Member added `tWhen: "$e.TimeGenerated "`tWho: "$e.ReplacementStrings[6] "`tAccount added: "$e.ReplacementStrings[0]
}
# Member Removed from Group
if (($e.EventID -eq 4729 )) {
write-host "Group: "$e.ReplacementStrings[2] "`tAction: Member removed `tWhen: "$e.TimeGenerated "`tWho: "$e.ReplacementStrings[6] "`tAccount removed: "$e.ReplacementStrings[0]
}}
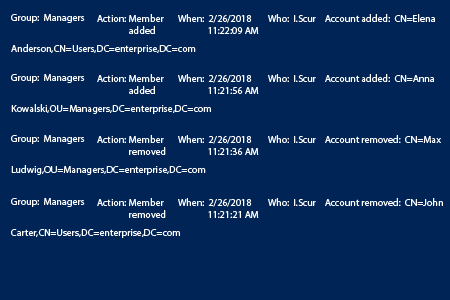
- Run Netwrix Auditor → Click on “Reports” → Open “Active Directory” → Go to “Active Directory Changes” → Select “Security Group Membership Changes” → Click “View”.
- If you want to get this report by email regularly, click the "Subscribe" option and define the schedule and recipients.
- To export the report to PDF, click the “Save” button and select where you want to save the file.